By: Gonipalli Bharath, Vel Tech University, Chennai, India, International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
DDoS has become one of the main cybersecurity threats that could bring online services, financial institutions, and even national infrastructures to their knees. The paper analyzes such major real-world DDoS incidents as on Dyn, GitHub, Estonia, and AWS with the motive of highlighting vulnerabilities leveraged by the attackers. We will come up with the basic lessons of how to secure IoT devices, strengthen DNS infrastructure, avoid amplification attacks, and be resilient against large-scale cyber threats. By integrating WAFs, cloud-based security solutions, IoT security, and incident response strategies, organizations can reduce the risks of DDoS. As cyber threats evolve, keeping up with good defense mechanisms becomes crucial for maintaining a secure digital landscape.
Introduction:
DDoS attacks have been one of the most crippling cyber menaces in the last few years. In this style of attack, an attacker makes a network, server, or website of the target go down by flooding it with an enormous volume of traffic. It results in huge loss, destruction of reputation, and sometimes even acts as a threat to national security. This article explores about some of the largest real-world DDoS attacks and the critical lessons learned from these cyber incidents.
The Dyn Attack, 2016,
One of the best-known DDoS attacks occurred in 2016 on October 21st against Dyn-one of the major DNS providers. The attack, under the so-called Mirai botnet, involved hundreds of thousands of IoT devices, including CCTV cameras and routers. Consequently, extremely popular websites such as Twitter, Netflix, Reddit, and PayPal went completely down[[1]]. It can be said that the proliferation of insecure IoT devices contributed to a great degree in this attack. Improving the security of IoTs through firmware updates, strong authentication mechanisms, and proper management is very necessary. DNS infrastructure should be robust, with a backup and mitigation plans for countering volumetric attacks.
The GitHub Attack, 2018,
In February 2018, GitHub faced a record-breaking DDoS attack with peak traffic of 1.35 terabits per second. Unlike traditional attacks based on botnets, the attack used a new form of DDoS attack known as Memcached amplification, which allowed attackers to reflect and amplify the traffic towards GitHub by exploiting open Memcached servers[[2]]. Poorly secured services can be exploited to execute an amplification attack. Best security practices include limiting access to services using UDP and disabling any feature that is not useful. A high-volume DDoS attack can be mitigated by having an efficient content delivery network and traffic filtering mechanisms.
The Estonia Cyberattack, 2007,
In 2007, Estonia fell victim to one of the largest politically motivated DDoS attacks following the relocation of a Soviet-era war memorial. Governmental sites, banks, and media all fell victim to this attack, crippling the digital infrastructure of the country for weeks[[3]]. Indeed, nation-state actors may use DDoS attacks as cyber weapons; therefore, cybersecurity strategies for protecting critical infrastructures become very important. Large-scale cyber threats can be managed only through effective public-private collaboration. The Estonian response was all about stressing the need for national and organizational cybersecurity resilience.
AWS DDoS Attack, 2020,
Amazon Web Services faced one of the largest-known DDoS attacks in history this year, peaking above 2.3 terabits per second in February 2020. The attack lasted for three continuous hours and disrupted cloud services and businesses running on it[[4]].Even large-scale cloud service providers with robust security are found vulnerable to large-scale attacks. The mitigation techniques need continuous improvement. Enterprises using cloud infrastructure should have multi-layered security: rate limiting, anomaly detection, and automated response mechanisms.
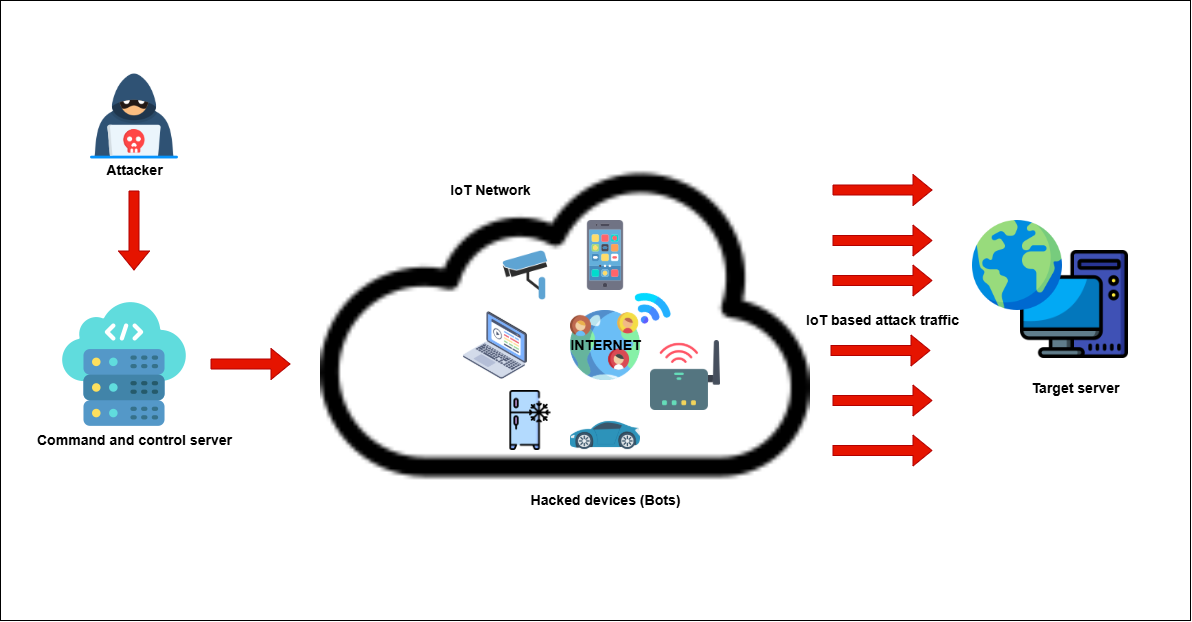
Fig([5])
Organizations can be ready for Cyber DDoS Threats :
These instances can, therefore, indicate a number of things that the organization might take to strengthen itself against DDoS attacks, including:
Deploy Web Application Firewalls -WAFs can assist filter malicious traffic and prevent volumetric attacks from overwhelming servers. Employ DDoS Mitigation Services Cloud-based mitigation services like as Cloudflare, Akamai, and AWS Shield absorb and filter harmful traffic before it reaches its intended destination. Improve IoT Security IoT security could be upgraded so that botnet-driven attacks are unfeasible. Regularly Monitor and Test Systems Conducting stress testing on a regular basis, as well as having an incident response strategy, enables a business to respond rapidly to an attack. Network redundancy and load balancing -Distributing network resources across many data focuses and Employing load balancing can reduces of the DDoS assaults(Distributed Denial-of-service-attack).
Conclusion:
Over the years, DDoS attacks have continuously been evolving in their sophistication and size. Incidents against Dyn, GitHub, Estonia, and AWS have shown just how vulnerable critical infrastructure and major online platforms can be. Still, it is robust security measures, collaboration between public and private sectors, and staying ahead of emerging techniques that would serve organizations in defending against probable DDoS threats. Cybersecurity is a never-ending war, and vigilance is the only way to reduce the risks in the digital era.
References:
- Pipyros, Kosmas, Christos Thraskias, Lilian Mitrou, Dimitris Gritzalis, and Theodoros Apostolopoulos. “A New Strategy for Improving Cyber-Attacks Evaluation in the Context of Tallinn Manual.” Computers & Security 74 (May 1, 2018): 371–83. https://doi.org/10.1016/j.cose.2017.04.007.
- Sharafaldin, Iman, Arash Habibi Lashkari, Saqib Hakak, and Ali A. Ghorbani. “Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy.” In 2019 International Carnahan Conference on Security Technology (ICCST), 1–8, 2019. https://doi.org/10.1109/CCST.2019.8888419.
- Snehi, Manish, and Abhinav Bhandari. “Vulnerability Retrospection of Security Solutions for Software-Defined Cyber–Physical System against DDoS and IoT-DDoS Attacks.” Computer Science Review 40 (May 1, 2021): 100371. https://doi.org/10.1016/j.cosrev.2021.100371.
- ———. “Vulnerability Retrospection of Security Solutions for Software-Defined Cyber–Physical System against DDoS and IoT-DDoS Attacks.” Computer Science Review 40 (May 1, 2021): 100371. https://doi.org/10.1016/j.cosrev.2021.100371.
- “The Aftermath of the Dyn DDOS Attack | IEEE Journals & Magazine | IEEE Xplore.” Accessed January 31, 2025. https://ieeexplore.ieee.org/abstract/document/8771413?casa_token=J5gXnLd_gv4AAAAA:TBdRx1Iw5jzK17U4u6oota1OF1Ff5hsOWqu0pwvN7QFbs5B6IZfQUUFtMl7DHcZDF5aw4Wo5vO4.
“The Aftermath of the Dyn DDOS Attack | IEEE Journals & Magazine | IEEE Xplore,” accessed January 31, 2025, https://ieeexplore.ieee.org/abstract/document/8771413?casa_token=J5gXnLd_gv4AAAAA:TBdRx1Iw5jzK17U4u6oota1OF1Ff5hsOWqu0pwvN7QFbs5B6IZfQUUFtMl7DHcZDF5aw4Wo5vO4. ↑
Iman Sharafaldin et al., “Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy,” in 2019 International Carnahan Conference on Security Technology (ICCST), 2019, 1–8, https://doi.org/10.1109/CCST.2019.8888419. ↑
Kosmas Pipyros et al., “A New Strategy for Improving Cyber-Attacks Evaluation in the Context of Tallinn Manual,” Computers & Security 74 (May 1, 2018): 371–83, https://doi.org/10.1016/j.cose.2017.04.007. ↑
- Manish Snehi and Abhinav Bhandari, “Vulnerability Retrospection of Security Solutions for Software-Defined Cyber–Physical System against DDoS and IoT-DDoS Attacks,” Computer Science Review 40 (May 1, 2021): 100371, https://doi.org/10.1016/j.cosrev.2021.100371. ↑
- Manish Snehi and Abhinav Bhandari, “Vulnerability Retrospection of Security Solutions for Software-Defined Cyber–Physical System against DDoS and IoT-DDoS Attacks,” Computer Science Review 40 (May 1, 2021): 100371, https://doi.org/10.1016/j.cosrev.2021.100371. ↑
- Gupta, B. B., Joshi, R. C., & Misra, M. (2009). Defending against distributed denial of service attacks: issues and challenges. Information Security Journal: A Global Perspective, 18(5), 224-247.
- Zheng, Q., Wang, X., Khan, M. K., Zhang, W., Gupta, B. B., & Guo, W. (2017). A lightweight authenticated encryption scheme based on chaotic scml for railway cloud service. IEEE Access, 6, 711-722.
- Gaurav A. (2023) Cybersecurity in the Smart Grid: Detecting and Mitigating DDoS Attacks, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Real-World DDoS Attacks: Lessons Learned from Major Cyber Incidents, Insights2Techinfo, pp.1