By: Karanvir Singh Khokhar1& Piyush Thakur2
1,2Department of CSE, Chandigarh College of Engineering & Technology, Chandigarh, India.
Abstract:
The article provides a comprehensive overview of the evolving landscape of security engineering in software development, emphasizing proactive measures to address contemporary cyber threats. Prior to moving on to the new computing technology, there is an imperative need to have knowledge of the number of levels of security that the technology provides to the data. Addresses the ever-changing nature of the security threat landscape, highlighting the need for software developers to adapt and proactively counter emerging threats. Emphasizes the importance of threat modeling as a proactive measure in identifying potential vulnerabilities and designing robust security measures during the software development life cycle. Explores the significance of adhering to security standards to ensure that software systems meet established criteria for security, thereby enhancing their resilience against cyber threats. Discusses the role of automated vulnerability scanning as a crucial component of a robust security framework, enabling the detection of potential weaknesses in software code and configurations. Highlights the importance of incorporating secure coding practices into the software development process, promoting the creation of inherently secure code and minimizing the risk of vulnerabilities. Explores the transformative impact of artificial intelligence on security, particularly in the realms of threat detection and response. AI is positioned as a valuable tool in enhancing the efficiency and effectiveness of security measures. Provides insights into practical strategies for implementing security measures, offering guidance on integrating threat modeling, compliance with standards, automated vulnerability scanning, secure coding practices, and AI into the software development process. Concludes by emphasizing the dynamic nature of the field and the need for continuous evolution in security engineering practices. Urges the software development community to remain vigilant and adaptive to address emerging challenges and ensure the resilience of software systems. Overall, the article encourages a proactive and comprehensive approach to security engineering, acknowledging the importance of staying ahead of cyber threats in the fast-paced digital landscape.
Keywords: Security Engineering, Security Frameworks and Models, Vulnerability Assessment and Mitigation, Security Standards.
Introduction to security engineering:
In an era dominated by digital connectivity, the role of security engineering [1] is more critical than ever in safeguarding software systems [2]. This section introduces the multifaceted nature of security engineering and its pivotal importance in contemporary software development [3]. As cyber threats continue to evolve, a proactive approach to security is essential for ensuring the integrity and resilience of software applications. From traditional security concerns to emerging risks associated with cloud computing [4] and IoT [5], understanding the breadth of potential threats sets the stage for comprehensive security engineering [6]. Some researchers have focused on problem of data leakage [7] in distributed systems [8] as data transferred across multiple systems.
Security frameworks and models:
Exploring the significance of threat modeling, this section delves into methodologies that help identify and mitigate potential security threats throughout the software development life cycle [9]. By systematically analyzing potential vulnerabilities, developers can proactively address security concerns and design robust counter measures. This subsection emphasizes the importance of adhering to security standards. Examining various standards, such as ISO/IEC 27001 or OWASP, provides insights into best practices for securing software applications. To overcome these issues, various security mechanisms have been proposed by researchers such as cryptography [10] and authentication [11]. Cryptography can be used to provide data integrity [12], authorization for data manipulation, and also making the data unreadable to an interceptor through encryption. Some researchers even compared encryption algorithms based on their performance in terms of stimulated time [13].
Vulnerability assessment and mitigation:
Highlighting the role of automated tools in identifying vulnerabilities, this section discusses the integration of scanning mechanisms into the development process. Automated vulnerability scanning [14] not only identifies potential weaknesses but also allows for rapid response and mitigation, minimizing the window of exposure to cyber threats [15]. This subsection underscores the importance of incorporating secure coding practices into the software development process. From input validation [16] to secure error handling [17], developers play a crucial role in mitigating potential security risks. Examining best practices in secure coding ensures that software is built with security in mind from its inception.
Security standards in security engineering:
Examining the integration of artificial intelligence [18] in security engineering, this section explores how AI enhances threat detection and response. From machine learning algorithms identifying anomalous patterns to natural language processing [19] in cyber security, AI-driven security represents a frontier in proactively addressing sophisticated cyber threats. Implementation of AI [20] based algorithms to enhance online system security have been explained by some researchers.
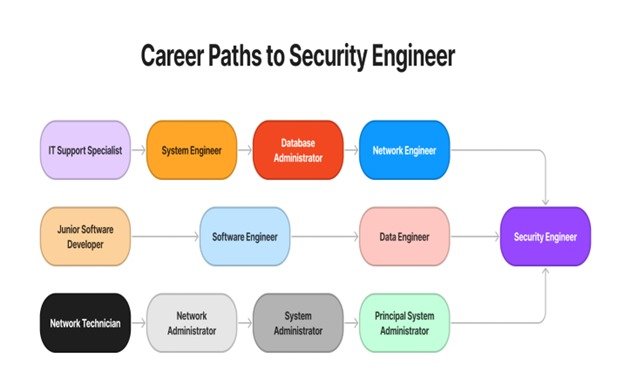
Fig 1: Career options leading to security engineering

Challenges and considerations:
Security engineering involves the intricate task of strengthening systems against various threats and vulnerabilities. A significant challenge lies in the increasing complexity of modern systems, which expands the potential attack surface and necessitates careful examination of interactions between components. Staying updated on emerging threats presents another significant hurdle; security engineers must constantly refresh their knowledge to predict and mitigate new attack vectors. Human error remains a persistent concern, highlighting the importance of addressing user behavior through comprehensive training and awareness efforts. Retrofitting security onto legacy systems presents its own challenges, requiring careful balancing of trade-offs between security, usability, performance, and cost. Compliance with regulatory standards further complicates matters, necessitating strict adherence to stringent requirements, particularly in regulated sectors. Supply chain security introduces additional risks, requiring thorough vetting of third-party suppliers and service providers. Encryption and data protection are critical, necessitating robust mechanisms to safeguard sensitive information against unauthorized access. Effective incident response planning is essential for promptly detecting, containing, and mitigating the impact of security breaches. Lastly, fostering a culture of security awareness among users and stakeholders is crucial, emphasizing the importance of ongoing education and vigilance in maintaining a secure environment. Addressing these complex challenges requires a multidisciplinary approach, drawing upon expertise in cryptography, software development, network security, and risk management, among other fields. Moreover, security engineering is an iterative process, requiring continuous monitoring, evaluation, and adaptation to evolving threats and technologies.
Conclusion:
In conclusion, the dynamic and interconnected nature of the digital landscape necessitates a continuous evolution of security engineering practices in software development. The findings of this article underscore that the traditional reactive approach to cyber security is insufficient in the face of rapidly emerging cyber threats. As technology progresses, the software development community is urged to adopt a proactive stance, anticipating and mitigating potential vulnerabilities throughout the entire development life cycle. The imperative to stay ahead of cyber threats is not merely a recommendation but a mandate for software developers and security practitioners. The ever-changing tactics employed by malicious actors demand a persistent commitment to innovation and adaptation. The conclusion serves as a clarion call for the industry to invest in research and development, embracing new tools, methodologies, and technologies that can bolster the resilience of software systems against evolving threats. Moreover, the call to action extends beyond individual developers to the broader software development community. Collaboration and knowledge sharing become crucial components in the collective effort to fortify digital ecosystems. By fostering a culture of vigilance, education, and collaboration, the industry can create an environment where the latest advancements in security engineering are shared and implemented universally. The concluding remarks emphasize that security is not a one-time fix but an ongoing commitment. It encourages the software development community to view security an integral part of the software development life cycle, woven into the fabric of every code, process, and decision. This approach ensures that security measures are not retrofitted but are intrinsic to the very foundation of software systems. In essence, the conclusion calls for a paradigm shift in how the industry perceives and prioritizes security. It challenges the status quo, pushing for a forward-looking, adaptive, and collaborative approach that can effectively navigate the complexities of the contemporary digital landscape. As technology continues to advance, the resounding message is clear: only through continuous evolution and a collective commitment to proactive security engineering can the software development community fortify itself against the ever-growing and sophisticated array of cyber threats.
References:
- Kumar, S., Singh, S. K., Aggarwal, N., & Aggarwal, K. (2021). Evaluation of automatic parallelization algorithms to minimize speculative parallelism overheads: An experiment. Journal of Discrete Mathematical Sciences and Cryptography, 24(5), 1517-1528.
- Singh, I., Singh, S. K., Singh, R., & Kumar, S. (2022, May). Efficient loop unrolling factor prediction algorithm using machine learning models. In 2022 3rd International Conference for Emerging Technology (INCET) (pp. 1-8). IEEE.
- Aggarwal, K., Singh, S. K., Chopra, M., Kumar, S., & Colace, F. (2022). Deep learning in robotics for strengthening industry 4.0.: opportunities, challenges and future directions. Robotics and AI for Cybersecurity and Critical Infrastructure in Smart Cities, 1-19.
- Kumar, S., Singh, S. K., Aggarwal, N., Gupta, B. B., Alhalabi, W., & Band, S. S. (2022). An efficient hardware supported and parallelization architecture for intelligent systems to overcome speculative overheads. International Journal of Intelligent Systems, 37(12), 11764-11790.
- Sharma, A., Singh, S. K., Badwal, E., Kumar, S., Gupta, B. B., & Arya, V. & Santaniello, D.(2023, January). Fuzzy Based Clustering of Consumers’ Big Data in Industrial Applications. In 2023 IEEE International Conference on Consumer Electronics (ICCE) (pp. 01-03).
- Mengi, G., Singh, S. K., Kumar, S., Mahto, D., & Sharma, A. (2021, September). Automated Machine Learning (AutoML): The Future of Computational Intelligence. In International Conference on Cyber Security, Privacy and Networking (pp. 309-317). Cham: Springer International Publishing.
- Kaur, P., Singh, S. K., Singh, I., & Kumar, S. (2021, December). Exploring Convolutional Neural Network in Computer Vision-based Image Classification. In International Conference on Smart Systems and Advanced Computing (Syscom-2021).
- Singh, M., Singh, S. K., Kumar, S., Madan, U., & Maan, T. (2021, September). Sustainable Framework for Metaverse Security and Privacy: Opportunities and Challenges. In International Conference on Cyber Security, Privacy and Networking (pp. 329-340). Cham: Springer International Publishing.
- Sharma, A., Singh, S. K., Kumar, S., Chhabra, A., & Gupta, S. (2021, September). Security of Android Banking Mobile Apps: Challenges and Opportunities. In International Conference on Cyber Security, Privacy and Networking (pp. 406-416). Cham: Springer International Publishing.
- Sharma, A., Singh, S. K., Badwal, E., Kumar, S., Gupta, B. B., Arya, V., … & Santaniello, D. (2023, January). Fuzzy Based Clustering of Consumers’ Big Data in Industrial Applications. In 2023 IEEE International Conference on Consumer Electronics (ICCE) (pp. 01-03). IEEE.
- Saini, T., Kumar, S., Vats, T., & Singh, M. (2020). Edge Computing in Cloud Computing Environment: Opportunities and Challenges. In International Conference on Smart Systems and Advanced Computing (Syscom-2021).
- Kumar, S., Singh, S. K., & Aggarwal, N. (2023). Speculative parallelism on multicore chip architecture strengthen green computing concept: A survey. In Advanced computer science applications (pp. 3-16). Apple Academic Press.
- Kumar, S. S., Singh, S. K., Aggarwal, N., & Aggarwal, K. (2021). Efficient speculative parallelization architecture for overcoming speculation overheads. In International Conference on Smart Systems and Advanced Computing (Syscom-2021) (Vol. 3080, pp. 132-138).
- Dubey, H. A. R. S. H. I. T., Kumar, S. U. D. H. A. K. A. R., & Chhabra, A. N. U. R. E. E. T. (2022). Cyber Security Model to Secure Data Transmission using Cloud Cryptography. Cyber Secur. Insights Mag, 2, 9-12.
- Kumar, S., & Singh, S. K. (2021). Brain computer interaction (BCI): A way to interact with brain waves.
- Sharma, A., Singh, S. K., Chhabra, A., Kumar, S., Arya, V., & Moslehpour, M. (2023). A novel deep federated learning-based model to enhance privacy in Critical Infrastructure Systems. International Journal of Software Science and Computational Intelligence (IJSSCI), 15(1), 1-23.
- Singh, K., Setia, H., & Kumar, S. (2021, December). Wi-Vi and Li-Fi based framework for Human Identification and Vital Signs Detection through Walls. In International Conference on Smart Systems and Advanced Computing (Syscom-2021).
- Setia, H., Chhabra, A., Singh, S. K., Kumar, S., Sharma, S., Arya, V., … & Wu, J. (2024). Securing the Road Ahead: Machine Learning-Driven DDoS Attack Detection in VANET Cloud Environments. Cyber Security and Applications, 100037.
- Vats, T., & Kumar, S. NEXT-GENERATION TOWARDS CONSTRUCTION OF CYBER-PHYSICAL SYSTEMS AND DIGITAL TWINS.
- Rastogi, A., Sharma, A., Singh, S., & Kumar, S. (2017). Capacity and Inclination of High Performance Computing in Next Generation Computing. Proceedings of the 11th INDIACom. IEEE.
Cite As
Khokhar K S, Thakur P (2024) Security Measures in Contemporary Software Engineering, Insights2Techinfo, pp.1