By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Phishing is one of the most common cyber threats that target individuals to organizations. The attack relies on human psychology and technical vulnerabilities to obtain sensitive information such as login credentials, financial details, and personal data. This article examines some important parameters that identify phishing attacks, with a particular focus on suspicious email and URL characteristics. By knowing such indicators, the targeted ones could improve their cybersecurity awareness and keep themselves safe from such malware. In addition, there will be a short table of the main indicators of phishing, including an attached flowchart about the detection process for better understanding.
Introduction:
Phishing attacks are getting more intelligent, and so the need arises for users to be able to identify warning signs in emails and URLs. The cyber attackers pose as trusted sources to trick their victims into clicking on malicious links or revealing information[1]. This paper will provide in-depth information on phishing attack signs and how the risks can be minimized.
Key Indicators of Phishing Emails
Phishing emails have a number of different warning signs that may indicate an imminent threat:
- Suspicious Sender Address: Attackers use email addresses that look almost, but not quite, like legitimate email addresses.
- Urgency or Threatening Language: Phishing emails try to make the user feel like they must take action right away[2].
- Unusual Greetings and Formatting: Generic salutations, such as “Dear User,” and poor grammar/spelling mistakes may show a potential phishing attempt.
- Unsolicited Attachments or Links: Email messages that include unsolicited attachments or hyperlinks are suspicious.
- Company Logos and Branding Spoofing: Attackers seek to make it look like well-known organizations; however, many times this is not the same as it would be on the original website[3].
Key Indicators of Phishing URLs
Phishing links actually redirect the target to a malignant website that will facilitate information stealing. Here, suspicious URLs are identified:
- Misspelled Domain Names: Hackers use typosquatting, a procedure where they will register domains including slight misspellings of those used by popular sites-for example, g00gle.com instead of google.com.
- Use of Shortened Links: Attackers mask malicious URLs inside shortened links such as bit.ly or tinyurl.com.
- HTTPS Abuse: While secure websites use HTTPS, some phishing sites obtain fraudulent SSL certificates to appear legitimate.
- Embedded Redirects: Some phishing URLs contain redirects leading to malicious destinations[4].
- Excessive Use of Special Characters: URLs with random symbols or unusual domain structures indicate a potential threat[5].
Table Representation of Key Indicators:
Category | Key Indicators |
Phishing Emails | Suspicious sender address, urgent language, generic greetings, unexpected attachments, spoofed branding. |
Phishing URLs | Misspelled domain names, shortened links, HTTPS misuse, embedded redirects, special characters. |
Table[6]
Flowchart to assist users in determining whether an email or URL is suspicious is provided below:
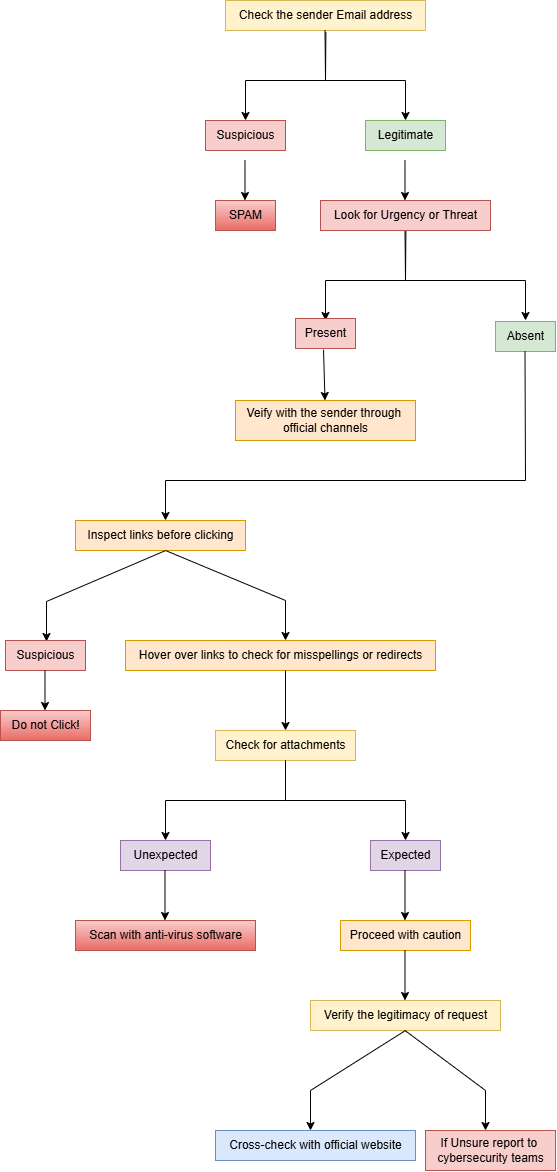
Conclusion:
Phishing attacks keep changing, but knowing key indicators in emails and URLs, users can save themselves from becoming victims. Cyber awareness, combined with security best practices, forms a very critical role in reducing risks. This also calls for organizations to have periodic training for their people on how to detect and report phishing attempts.
References:
- G. Desolda, J. Aneke, C. Ardito, R. Lanzilotti, and M. F. Costabile, “Explanations in warning dialogs to help users defend against phishing attacks,” Int. J. Hum.-Comput. Stud., vol. 176, p. 103056, Aug. 2023, doi: 10.1016/j.ijhcs.2023.103056.
- A. Jayatilaka, N. A. G. Arachchilage, and M. A. Babar, “Why People Still Fall for Phishing Emails: An Empirical Investigation into How Users Make Email Response Decisions,” Jan. 24, 2024, arXiv: arXiv:2401.13199. doi: 10.48550/arXiv.2401.13199.
- Y. Yu, S. Ashok, S. Kaushik, Y. Wang, and G. Wang, “Design and Evaluation of Inclusive Email Security Indicators for People with Visual Impairments,” in 2023 IEEE Symposium on Security and Privacy (SP), May 2023, pp. 2885–2902. doi: 10.1109/SP46215.2023.10179407.
- “Hidden Path: Understanding the Intermediary in Malicious Redirections | IEEE Journals & Magazine | IEEE Xplore.” Accessed: Feb. 07, 2025. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9762296
- S. Garnayak, A. Kumar, S. Sahoo, B. Gouda, and V. Sharma, “Enhancing Cybersecurity: Machine Learning Techniques for Phishing URL Detection,” in 2024 International Conference on Electrical Electronics and Computing Technologies (ICEECT), Aug. 2024, pp. 1–6. doi: 10.1109/ICEECT61758.2024.10739207.
- T. Laava, “External email tags in phishing detection.” Accessed: Feb. 07, 2025. [Online]. Available: http://www.theseus.fi/handle/10024/873603
- Gupta, B. B., Gaurav, A., Panigrahi, P. K., & Arya, V. (2023). Analysis of artificial intelligence-based technologies and approaches on sustainable entrepreneurship. Technological Forecasting and Social Change, 186, 122152.
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). InFeMo: Flexible big data management through a federated cloud system. ACM Transactions on Internet Technology (TOIT), 22(2), 1-22.
- K. Yadav, B. B. Gupta, D. Peraković (2022), Developing Cyber-Attacks with Machine Learning, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Spotting the Hook: Key Indicators of Phishing Attacks in Emails and URL’s, Insights2Techinfo, pp.1