By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
The installation of 5G technology delivers substantial progress in connectivity systems, which provides both swifter performances along with reduced delay times and encourages wider usage of IoT devices. The next-generation network presents new security weaknesses that cybercriminals rapidly take advantage of mostly through Distributed Denial of Service (DDoS) attacks. Internal and external network complexities alongside rising unauthorized IoT devices and expanded bandwidth have transformed 5G networks into an optimal target for completing destructive and advanced DDoS attacks. The article evaluates the hidden dangers of 5G technology through its technological developments which drive Distributed Denial of Service attacks. The analysis presents actual threats to intelligent urban areas and automated transport systems and vital infrastructure in addition to providing practical solutions for protection against these dangers. The benefits of 5G become secure through implementing strong security safeguards to protect against cyber disruptions.
Introduction
5G technology has launched into the market with widespread acceptance because it delivers enhanced speed alongside decreased delay and expanded connectivity. A significant transformation of daily life and work activities will occur because of 5G technology implementation. This technological revolution that delivers 5G introduces a harmful consequence through expanded vulnerability to Distributed Denial of Service (DDoS) attacks. As 5G networks grow in size they generate fresh security weaknesses which attract determined cyberattacks[1]. This paper analyzes the ways 5G technology drives Distributed Denial of Service threats together with techniques for security risk reduction.
The 5G Revolution and its Vulnerabilities
The 5G network infrastructure supports multiple connected devices including smartphones together with IoT sensors. Although advantageous for connectivity the wider interconnected network makes it simpler for cybercriminals to launch attacks. 5G networks base their operation on software-defined networking (SDN) and network function virtualization (NFV) unlike the previous communication system[2]. These technologies improve 5G flexibility, but their implementation creates additional security weaknesses.
The centralized structure of 5G control planes exposes them to attacks from potential intruders. The successful penetration of 5G infrastructure by cybercriminals enables them to control network traffic while using it to boost DDoS attacks and conduct complete network shutdowns. The large number of devices linking to 5G networks creates multiple possibilities for attackers to establish botnets which serve as networks of controlled devices for executing DDoS attacks[1].
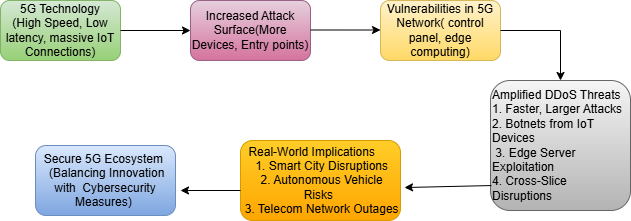
How 5G Amplifies DDoS Threats
1. Increased Bandwidth and Speed:
The fast bandwidth and quick response times of 5G technology allow attackers to launch more effective and stronger DDoS attacks[3]. Attractors now generate high volumes of traffic rapidly that enables them to deplete defensive systems in condensed periods of time.
2. Proliferation of IoT Devices:
The foundation of the 5G system depends on a large number of IoT devices which operate without sufficient built-in security protocols. The devices represent effortless targets which hackers find simple for recruiting bots into their networks. The spread of disruptive DDoS attacks in 2016 occurred when the Mirai botnet exploited IoT devices lacking proper security to execute destructive cyberattacks[4]. Fast growth projections of connected devices through 5G networks will result in generalized attacks since attackers will gain access to more potential bots.
3. Edge Computing Risks:
The processing of source data using 5G networks becomes more efficient through edge computing which shortens data transfer times. The implementation of decentralization through edge computing technology enables new possible security attack entry points[5]. Critical edge servers become vulnerable when security measures are insufficient because attackers can easily take control of these systems for launching destructive DDoS attacks that disrupt basic infrastructure services[6].
4. Network Slicing Vulnerabilities:
5G presents the idea of network slicing, which is the division of a single physical network into several virtual networks. Customized services are made possible by this, however there may be drawbacks. An attacker may exploit the hacked slice to launch attacks or maybe disrupt additional slices if they manage to compromise one.
Real-World Implications
The impact from DDoS attacks caused by 5G technology can lead to major losses. When attacks prove successful against businesses they suffer monetary damage along with damaged reputations together with regulatory consequences[7]. Critical infrastructure systems which include healthcare facilities alongside transportation networks could potentially endanger human life through successful 5G-fueled DDoS cyberattacks. Consider the following scenarios:
An attack on smart city 5G-enabled infrastructure would disrupt traffic management systems emergency services and public utility services thus causing dangerous disarray that endangers public lives.
The damage to 5G networks providing autonomy features in vehicles creates transportation dangers and safety issues that reduce acceptability of this technological advancement among the public.
Telecommunications providers face a significant risk when a 5G-based DDoS attack occurs because it disrupts communication networks and impacts millions of users alongside many businesses.
Conclusion
People benefit greatly from 5G technology yet face new cybersecurity challenges because of its introduction into the market. DDoS attacks continue to develop their sophistication while increasing their power which requires businesses to establish unparalleled defense capabilities more than ever before. Our ability to grasp 5G risks combined with preventive steps enables us to capture these network technology benefits without permitting its negative outcomes. The advancement of future connectivity requires us to lead cybercriminals by staying ahead since this will keep 5G as a beneficial force within our continuously connected world.
References
- X. Chen et al., “Real-Time DDoS Defense in 5G-Enabled IoT: A Multidomain Collaboration Perspective,” IEEE Internet Things J., vol. 10, no. 5, pp. 4490–4505, Mar. 2023, doi: 10.1109/JIOT.2022.3218728.
- F. Z. Yousaf, M. Bredel, S. Schaller, and F. Schneider, “NFV and SDN—Key Technology Enablers for 5G Networks,” IEEE J. Sel. Areas Commun., vol. 35, no. 11, pp. 2468–2478, Nov. 2017, doi: 10.1109/JSAC.2017.2760418.
- Y.-E. Kim, Y.-S. Kim, and H. Kim, “Effective Feature Selection Methods to Detect IoT DDoS Attack in 5G Core Network,” Sensors, vol. 22, no. 10, Art. no. 10, Jan. 2022, doi: 10.3390/s22103819.
- M. Jazzar and M. Hamad, “An Analysis Study of IoT and DoS Attack Perspective,” in Proceedings of International Conference on Intelligent Cyber-Physical Systems, B. Agarwal, A. Rahman, S. Patnaik, and R. C. Poonia, Eds., Singapore: Springer Nature, 2022, pp. 127–142. doi: 10.1007/978-981-16-7136-4_11.
- A. M. Alwakeel, “An Overview of Fog Computing and Edge Computing Security and Privacy Issues,” Sensors, vol. 21, no. 24, Art. no. 24, Jan. 2021, doi: 10.3390/s21248226.
- R. Uddin, S. A. P. Kumar, and V. Chamola, “Denial of service attacks in edge computing layers: Taxonomy, vulnerabilities, threats and solutions,” Ad Hoc Netw., vol. 152, p. 103322, Jan. 2024, doi: 10.1016/j.adhoc.2023.103322.
- U. D. Maiwada, S. A. Imran, K. U. Danyaro, A. A. Janisar, A. Salameh, and A. B. Sarlan, “Security Concerns of IoT Against DDoS in 5G Systems,” Int. J. Electr. Eng. Comput. Sci., vol. 6, pp. 98–105, Mar. 2024, doi: 10.37394/232027.2024.6.11.
- Zhang, Q., Guo, Z., Zhu, Y., Vijayakumar, P., Castiglione, A., & Gupta, B. B. (2023). A deep learning-based fast fake news detection model for cyber-physical social services. Pattern Recognition Letters, 168, 31-38.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- Masud, M., Gaba, G. S., Alqahtani, S., Muhammad, G., Gupta, B. B., Kumar, P., & Ghoneim, A. (2020). A lightweight and robust secure key establishment protocol for internet of medical things in COVID-19 patients care. IEEE Internet of Things Journal, 8(21), 15694-15703.
- Neelapareddigari P (2024) Reinforcement Learning for Cybersecurity, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) The Dark Side of 5G : How Next Generation Network are fueling DDoS Threats, Insights2techinfo pp.1