By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Commercial growth of Internet of Things technology has converted major sectors and households together with cities into more efficient platforms that bring better convenience. Smart devices connected to the internet expose security gaps which criminal attackers use for their harmful operations. Bots as well as DDoS attacks through botnets have made IoT devices important attack targets for cyber criminals who also use devices to steal data while performing unauthorized surveillance. This article examines the IoT dark side through its criminal hacking methods as well as actual events and protection approaches against these cyber threats. The analysis demonstrates the critical necessity of adopting better security strategies and regulatory approaches which will protect against these developing cyber threats.
Introduction
Modern life has transformed through the Internet of Things (IoT) technology which allows smart devices to enter residential, work-based and industrial infrastructure systems. IoT has brought multiple benefits such as connected medical devices and home surveillance systems and improved voice assistants and smart refrigerators for users. The numerous connections between IoT devices create security dangers because hackers take advantage of security vulnerabilities within IoT systems[1]. Smart devices have become targets for cybercriminals to carry out destructive attacks which include hacking operations combined with economic crimes and spying activities.
How Cybercriminals Exploit IoT Devices
1. Botnet-Based DDoS Attacks
The dangerous capabilities of IoT botnets emerged through their flagship examples Mirai and Mozi by enabling the takeover of smart devices. When cybercriminals breach vulnerable IoT devices they convert them into botnets which launch destructive Distributed Denial-of-Service (DDoS) assaults that flood target networks thus creating interruptions[2].
2. Unauthorized Surveillance and Espionage
Voice assistants together with baby monitors and smart cameras enable unauthorized surveillance of users by hackers who can access the devices secretly. Cyber attackers use default login information and exposed system vulnerabilities to break into devices which they use for collecting victims’ information or conducting business espionage or conducting blackmail operations or personal surveillance[3].
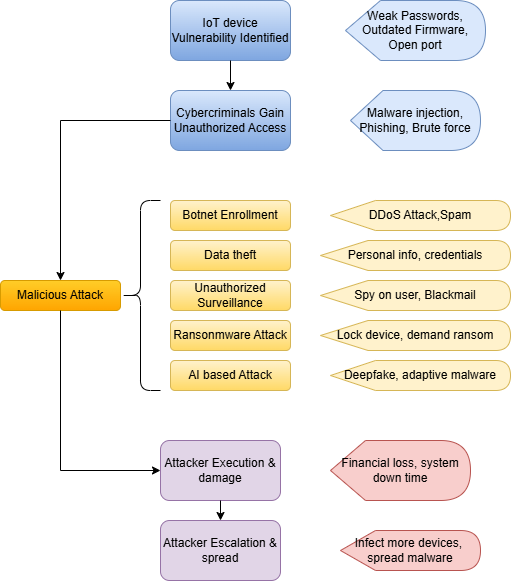
3. Data Theft and Identity Fraud
Multiple IoT devices routinely gather as well as distribute critical personal information joined with money-related facts along with biometric information[4]. Cybercriminals achieve this data interception by using man-in-the-middle attacks which they exploit either by weak encryption methods or inadequate cloud storage security to carry out identity theft and financial fraud.
4. Ransomware on IoT Devices
The number of ransomware attacks targeting IoT devices continues to rise because hackers prevent users from accessing critical systems after encrypting their data to extort ransom payments[3]. Specifically, the functions performed by smart thermostats and industrial IoT systems and medical devices make these devices vulnerable targets for attacks.
5. Deepfake and AI-Driven Attacks
Deepfake technology enables cybercriminals to use AI for breaking through biometric authentication measures on smart devices because of the recent AI advancements. The adaptation of security defenses by intelligent malware through AI-driven attacks makes traditional cybersecurity solutions less capable of preventing such attacks[4].
Real-World Cases of IoT Exploitation
During 2016 the Mirai Botnet Attack became infamous for taking control of thousands of IoT devices to launch the biggest DDoS exploit which disrupted critical online services[5].
Multiple instances of Ring security cameras’ compromise have emerged where hackers managed to gain surveillance access that resulted in family spying and child harassment.
The security of connected medical equipment such as pacemakers and insulin pumps face considerable threats from Cyber-attacks which affect patient safety levels[6].
Mitigating IoT Cyber Threats[7]
Security professionals and both manufactures and users need to follow multiple proactive measures together to reduce IoT-based cyber threats.
1. Systems that offer multiple authentication levels should be deployed with manufacturers, preventing users from setting default passwords on devices.
2. Frequent software upgrades along with security fixes must be provided to IoT devices to repair their weaknesses.
3. Network Segmentation represents a security method to place IoT devices on independent networks which minimizes the spread of hackers during breaches.
4. Artificial intelligence technologies would detect abnormal IoT ecosystem behavior to quickly respond to threats when used in this approach.
5. Governments along with industry bodies need to establish more stringent IoT security standards which require proper certifications for safety reduction.
Conclusion
Although IoT has many benefits in terms of automation and connectivity, its flaws provide up new opportunities for criminal activity. The issues posed by the dark side of IoT require ongoing innovation in security procedures, regulation, and user education. Our defenses must develop together with technology to guarantee a safer digital environment where smart devices serve us rather than against us. Establishing industry-wide security standards and best practices require cooperation from organizations, manufacturers, and legislators. We can only successfully reduce the hazards and safely realize all that is possible of IoT by working properly.
References
- J.-P. A. Yaacoub, H. N. Noura, O. Salman, and A. Chehab, “Ethical hacking for IoT: Security issues, challenges, solutions and recommendations,” Internet Things Cyber-Phys. Syst., vol. 3, pp. 280–308, 2023, doi: 10.1016/j.iotcps.2023.04.002.
- M. N, V. K R, and E. R. B, “Short Paper : Current Challenges in IoT Cloud Smart Applications,” in 2021 IEEE International Conference on Cloud Computing in Emerging Markets (CCEM), Oct. 2021, pp. 36–40. doi: 10.1109/CCEM53267.2021.00016.
- M. Humayun, N. Jhanjhi, A. Alsayat, and V. Ponnusamy, “Internet of things and ransomware: Evolution, mitigation and prevention,” Egypt. Inform. J., vol. 22, no. 1, pp. 105–117, Mar. 2021, doi: 10.1016/j.eij.2020.05.003.
- A. Trivedi, “Identifying Deepfake Cyber Attacks: Challenges and Countermeasures,” Int. J. Res. Appl. Sci. Eng. Technol., vol. 13, no. 1, pp. 475–478, Jan. 2025, doi: 10.22214/ijraset.2025.66305.
- V. Vajrobol, B. B. Gupta, A. Gaurav, and H.-M. Chuang, “Adversarial learning for Mirai botnet detection based on long short-term memory and XGBoost,” Int. J. Cogn. Comput. Eng., vol. 5, pp. 153–160, 2024, doi: 10.1016/j.ijcce.2024.02.004.
- M. Rahaman, C. Y. Lin, I. Rachmat, R. Bansal, and Prayitno, “Secure Health Features: Implementing Hyperledger Fabric in Blockchain-Driven Healthcare Management Systems,” in Digital Forensics and Cyber Crime Investigation, CRC Press, 2024.
- A. Alagappan, L. J. Baptist Andrews, S. Kumar Venkatachary, S. D, and R. A. Raj, “Cybersecurity Risks Mitigation in the Internet of Things,” in 2022 2nd International Conference on Innovative Sustainable Computational Technologies (CISCT), Dec. 2022, pp. 1–6. doi: 10.1109/CISCT55310.2022.10046549.
- AlZu’bi, S., Shehab, M., Al-Ayyoub, M., Jararweh, Y., & Gupta, B. (2020). Parallel implementation for 3d medical volume fuzzy segmentation. Pattern Recognition Letters, 130, 312-318.
- Cajes N. (2025) The Future of IoT Security: Defending Against DDoS Attack, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) The Dark Side of IoT : How Cyber Criminals are Leveraging Smart Devices, Insights2techinfo pp.1