By: Nicko Cajes; Northern Bukidnon State College, Philippines
Abstract
A sophisticated type of cyber-attack is introduced in the modern age which is the spear phishing. This attack targets a specific individual through the use of messaging platform aiming to gain confidential information. This paper ventures to the techniques utilized by the attackers in conducting a spear-phishing attack and the effective defense strategies against it. By comprehensively understanding the root cause and the threat this poses, individuals and organization can effectively avoid the harms related to this attack.
Introduction
Fraudulent activities have been widely operated in the cyber space, and spear phishing is one of them. Spear phishing is a type of cyber-attack which targets a specific business or person where fraudulent emails are being sent in order to gain confidential information [1]. This attack has posed a significant threat to individuals and organization as this have a huge potential in providing huge damage generally, necessitating an effective defensive measurement against it [2]. With the continuous advent of technology, spear-phishing attacks have grown into sophistication, taking itself a huge leap together with the rapid advancement in technology, enabling them to easily adapt and prevent being detected by security measurements [3]. This article will discuss the hidden threat of spear phishing, by comprehensively discussing it, it will aim to give an understanding of how to prevent spear phishing attacks.
How Spear Phishing Works
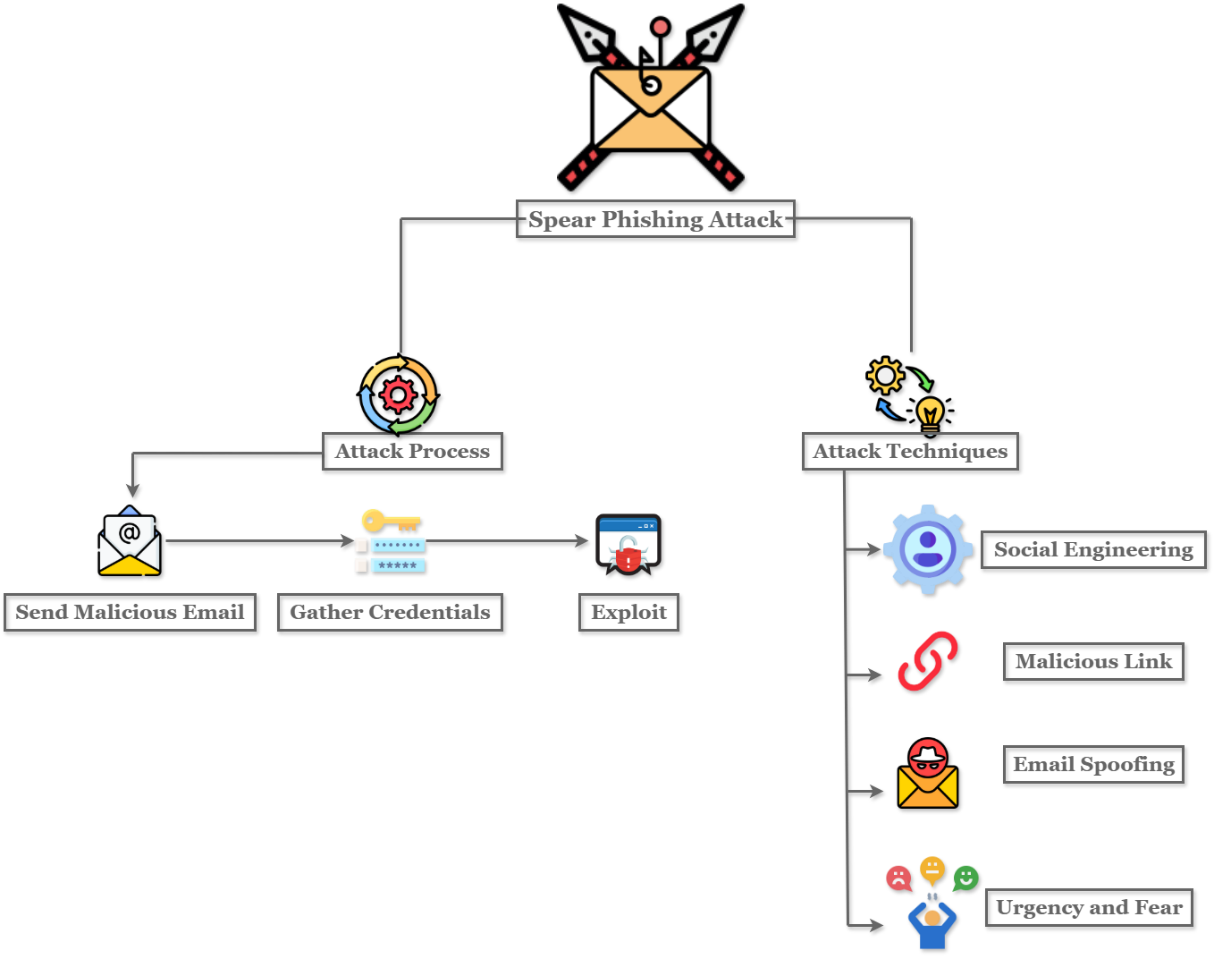
Spear phishing attack utilize advancement of technological communication such as the email to conduct their attack. It is done by the way of sending malicious email to fool a specific person, business, or organization eventually gaining their user or company credentials giving them access and allowing them to conduct malicious activity resulting to a huge problem financially and possibly data theft [4]. With its dynamically evolving nature, spear-phishing attacks was carried out by the attackers in various techniques such as email spoofing, social engineering, malicious links attachment, urgency and fear tactics, and impersonating of trusted services, an overview of phishing attack is shown in figure 1.
Email Spoofing: The email spoofing technique is one of the well-known methods carried out in a spear-phishing attack. This is done by modifying the headers of the message in order to have a high success rate of fooling the recipient and will make the message looks like it comes from a legitimate sender [5].
Social Engineering: Social engineering is a type of technique where it focuses mainly on the weakest link in the security systems, and the is the user itself. This attack has the novel method where it bypasses the advancement of the security implemented against cyber-threats by utilizing the chances of humans and providing ease to gain their trust easily [6].
Malicious Links Attachment: In spear-phishing technique, the malicious links attachment was made by the attackers to act as a bait to the victim. This bait will play a crucial role in this attack, as if ever the victim clicked it, it will have a huge chance of having them download a malicious software or giving the attacker a chance to exploit the weaknesses in their system and conduct the malicious software installation in the later part [7].
Urgency and Fear Appeals: Urgency and fear appeals is a type of spear phishing technique which utilize the method of human psychology. Attackers are making this attack possible through manipulating human behavior, providing a legitimate fear and urgency to the victim by stating harms and risks that they can obtain if they are not going to follow to their instructions [8].
Real-World Examples
Due to its wide implementation, spear-phishing attacks have posed a huge threat considering its potential to give massive damage. Some notable phishing incidents have already been witnessed in the new era, which gives some scary threat when thinking of becoming the attack victim.
2020 Twitter Hack: In the middle of the month of July year 2020, the popular social media platform named Twitter was targeted in a spear phishing attack. In this attack, primary accounts have begun in twittering a message which asked to transfer bitcoin to a specific bitcoin wallet, the message has a promise that the amount of bitcoin sent will be doubled when the sender sends it, utilizing the incident of COVID-19 to act as a method of helping them in the time of crisis [9].
The 2014 Sony Pictures Hack: This spear-phishing incident targets Sony employees and was one of the attacks that was treated as bold and daring. In this attack, one of the identified elements is the “rapaciousness” which North Korea have entitlement , making a huge shift on how countries see North Korea aside from its immense nuclear power. However, this attack has another meaning, it doesn’t aim to steal money, besides it was conducted to just embarrass Sony Pictures remotely [10].
The 2016 Democratic National Committee Hack: This incident has a unique impact in the society as it introduces the strong idea that social engineering tactics are not just a threat to companies and individuals, but also for the huge world of politics. In this attack, hackers from Russia targets a high-profile individual in the Democratic national Committee through sending a legitimate look-a-like email coming from Google primarily requesting him to change his credentials as there are suspicious activities detected from his account [11].
These notable incidents have provided a wake-up call to everyone, as it demonstrates how much is the level of attack techniques performed by the attackers nowadays. This can be reflected through the way and the target of their attacks, which has the huge potential of damaging the spear targeted victim in reputation and financially.
Prevention and Protection Strategies
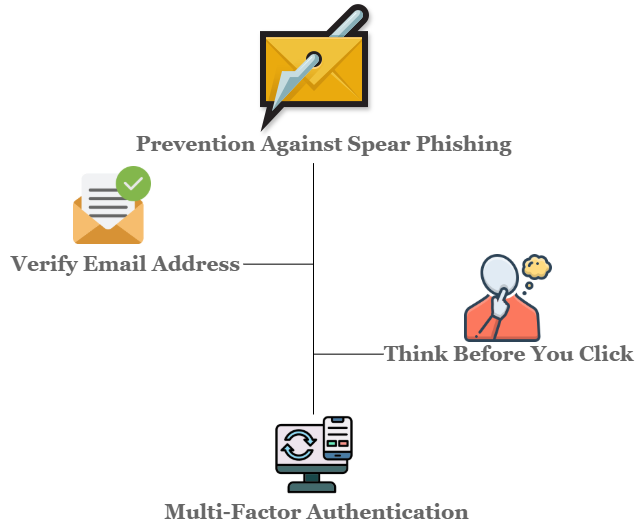
The threat posed by this attack cannot be neglected easily, in this regards there are already a lot of strategies deployed in order to effectively prevent being a victim later. The following are the best practices for individuals which will definitely aid them to avoid being a victim of the attack.
Verify Email Address: One of the things that a receiver of the email address can do to prevent being attacked is to carefully verify the email address of the sender. In this way, they can easily identify if the sender is a legitimate or unknown, even though there are a lot of look-a-like email sender, this method is still an effective way to authenticate the legitimacy of the sender as the email address will highly replicate the originality of the email [12].
Think Before You Click: As one of the well-known mottos in cybersecurity, think before you click is an important part to avoid this attack. By thinking first for the major factors and consequences related to the email or message itself, this motto can significantly bolster the chances of not being a victim even though you are targeted as an attack victim [13].
Multi-Factor Authentication: The Multi-Factor Authentication method is a great way to evade this attack, it offers a far more advance strategy against the sophistication techniques of the attackers. With this strategy, even if the victim is already being blocked, the attacker can’t still access the information they wanted because they are lacking for the important characteristics needed to unlock your accounts aside from the user and password credentials [14].
Security Measures for Organizations
Employee Awareness Training: Many spear phishing attacks from the business or companies involved the attack from its employees, with this the importance of having an employee awareness training plays a crucial part of making the organization safe from the spear-phishing attack. With the help of this, employees can gain the necessary knowledge on the dos and don’ts of a legitimate and fraudulent messages received [15].
Email Filtering: Email filtering is an effective method that can be done by the organization to prevent being attack. In this strategy, the email was filtered out either a potential risk or harmless email before they reach the inbox of the receiver. This strategy can aid a lot of things especially if the user is not too wary about this attack, by applying this danger signs and risk description can be easily introduced to the recipient advertising a comprehensive way of tackling the issue [16].
Conclusion
One of the remaining important cyber-threats to tackle is the spear-phishing. Its evolving nature and targeted methodology have made it become well-known and eventually noticed. The damage it provides to real-world have highlighted it risks to individuals, organizations, and even political entities. In order to cope up with this threat, advanced strategies in solving this problem needs to be implemented like employee training, email verification, email filtering, and many more are needed to be applied to have the least chance of being the victim of this attack.
References
- Karmakar, S., & Bhatia, M. (2022). Phishing Attacks and It’s Working Methodology and How Spear Phishing Is Happening in Modern IT Hubs. International Journal of Mechanical Engineering, 9.
- Alaaraj, A., & Yassin, A. (2024). Investigating cybersecurity response strategies: Measures to responding to successful spear phishing attacks.
- Nadeem, M., Zahra, S., Abbasi, M., Arshad, A., Riaz, S., & Ahmed, W. (2023). Phishing Attack, Its Detections and Prevention Techniques. International Journal of Wireless Security and Networks, 1(2), 13-25p.
- Baig, M. S., Ahmed, F., & Memon, A. M. (2021, November). Spear-Phishing campaigns: Link Vulnerability leads to phishing attacks, Spear-Phishing electronic/UAV communication-scam targeted. In 2021 4th International Conference on Computing & Information Sciences (ICCIS) (pp. 1-6). IEEE.
- Birthriya, S. K., Ahlawat, P., & Jain, A. K. (2025). Detection and Prevention of Spear Phishing Attacks: A Comprehensive Survey. Computers & Security, 104317.
- Tomsu, M., Rosiková, V., Vojtek, P., & Hrabakova, M. (2023). Spear-phishing and Its Specifics Within Social Engineering. Annals of DAAAM & Proceedings, 34.
- TrendLabsSM, A. P. T. (2012). Spear-Phishing Email: Most Favored APT Attack Bait. Trend Micro.
- Alsulami, S., & Dupuis, M. (2024, October). The Effectiveness of Education and Fear Appeal to Prevent Spear Phishing Attacks. In 2024 Cyber Awareness and Research Symposium (CARS) (pp. 1-8). IEEE.
- Witman, P. D., & Mackelprang, S. (2022). The 2020 Twitter Hack–So Many Lessons to Be Learned. Journal of Cybersecurity Education, Research and Practice, 2021(2).
- Rose, L. A. (2021). Bridging the Realms Between Cyber and Physical: Approaching Cyberspace with an Interdisciplinary Lens.
- Aldawood, H., & Skinner, G. (2020). An advanced taxonomy for social engineering attacks. International Journal of Computer Applications, 177(30), 1-11.
- Nahmias, D., Engelberg, G., Klein, D., & Shabtai, A. (2024). Prompted contextual vectors for spear-phishing detection. arXiv preprint arXiv:2402.08309. [13] Tchakounte, F., Nyassi, V. S., Danga, D. E. H., Udagepola, K. P., & Atemkeng, M. (2021). A game theoretical model for anticipating email spear-phishing strategies. EAI Endorsed Transactions on Scalable Information Systems, 8(30), e5-e5.
- Muir, A., Brown, K., & Girma, A. (2024, November). Reviewing the Effectiveness of Multi-factor Authentication (MFA) Methods in Preventing Phishing Attacks. In Proceedings of the Future Technologies Conference (pp. 597-607). Cham: Springer Nature Switzerland.
- Braham, N. R. (2022). Mitigating the Spread of Spear-Phishing Attacks as a Form of Cybercrime: A Human Cognitive Challenge. Utica University.
- Birthriya, S. K., Ahlawat, P., & Jain, A. K. (2025). Detection and Prevention of Spear Phishing Attacks: A Comprehensive Survey. Computers & Security, 104317.
- Stergiou, C. L., Plageras, A. P., Psannis, K. E., & Gupta, B. B. (2020). Secure machine learning scenario from big data in cloud computing via internet of things network. Handbook of Computer Networks and Cyber Security: Principles and Paradigms, 525-554.
- Lu, J., Shen, J., Vijayakumar, P., & Gupta, B. B. (2021). Blockchain-based secure data storage protocol for sensors in the industrial internet of things. IEEE Transactions on Industrial Informatics, 18(8), 5422-5431.
- Katiyar A. (2024) Social Engineering Phishing Detection, Insights2Techinfo, pp.1
Cite As
Cajes N. (2025) The Hidden Threat: Understanding and Preventing Spear Phishing Attacks, Insights2Techinfo, pp.1