By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Information is one of the most precious resources in today’s world and thus keeping it safe from unauthorized access is imperative. Data encryption is one of the essential cybersecurity tools that make sure sensitive information is kept secret even if it is intercepted by unauthorized attackers. Data encryption protects financial, organizational, and personal data from theft, fraud, and breaches by making it unreadable.The significance of encrypting data, the types, advantages, and best practices for implementing encryption are explained in this article. It also mentions the dangers of not encrypting and offers actionable advice on how individuals and organizations can successfully encrypt their data.
Introduction
The digital landscape depends so much on data to propel communication, innovation, and decision-making. The increasing volume of data does, however, make it a prime target for cybercriminals too. Issues of identity theft, data breaches, and unauthorized access are becoming increasingly common to individuals as well as companies.Data encryption is one of the best ways of guaranteeing privacy, accuracy, and authenticity of information[1]. Even if information ends up in the wrong hands, encryption keeps it safe from unauthorized users by disguising it in such a way as to not reveal the sensitive information, this article explores the significance of data encryption and how to encrypt successfully.
What is Encryption of Data
Using an algorithm and an encryption key? Data transforms readable data, or plaintext, into unreadable data, or ciphertext.The ciphertext can only be converted back into plaintext by authorized individuals who possess the proper decryption key[2]. Encryption guarantees that information is confused and useless to an attacker, even if it is intercepted or viewed without permission.
There are several uses for encryption, such as:
- Protecting texts and emails.
- Safeguarding information on devices (such as computers and cellphones).
- Protecting information sent across networks, such as those involved in online transactions.
- Making sure that data protection laws are followed.
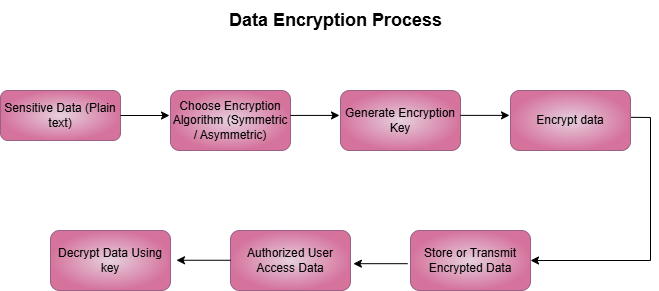
Why Data Encryption Matters[3]
Data encryption is necessary for a few reasons:
- Protecting Sensitive Information: Organizational, financial, and personal data are protected from unwanted access by encryption.
- Preventing Data Breaches: Even if hackers can intercept encrypted data, they will be unable to use it.
- Ensuring Compliance: To secure sensitive data, encryption is required by numerous legislations, including GDPR and HIPAA.
- Building Trust: By showcasing a dedication to data security, encryption increases stakeholder and customer trust.
- Risk Mitigation: Encryption lessens the effect of ransomware and phishing attacks.
Signal and WhatsApp, for instance, are encrypted communication services that guarantee the privacy of messages, even if they are intercepted.
Types of Data Encryption[4]
Encryption Type | Description | Example Algorithms |
Symmetric Encryption | Uses a single key for encryption and decryption | AES, DES, Blowfish |
Asymmetric Encryption | Uses a pair of public and private keys for encryption and decryption | RSA, ECC |
Hashing | Convert data into a fixed length hash value, ensuring integrity. | SHA-256, MD5 |
Data Encryption Benefits[5]
Data encryption has many benefits, such as:
- Restricted access to sensitive information is ensured via confidentiality.
- The protection of data against alteration or tampering during transmission is provided by integrity.
- Organizations can meet legal and regulatory standards with the aid of compliance.
- Reputation: Increases credibility and trust with buyers and partners.
- By reducing the impact of data breaches and cyberattacks, risk mitigation makes a significant contribution.
Risks of Not Using Encryption[6]
If data is not encrypted, there may be serious risks, including:
- Data Breaches: Hackers can easily access and take advantage of unencrypted data.
- Financial Loss: Violations may lead to penalties, legal costs, and lost income.
- Reputational Damage: Businesses who do not protect their data risk losing the trust of their customers.
- Identity Theft: Personal information that isn’t secured can be used fraudulently.
For example, the 2017 Equifax hack, which was mostly caused by unencrypted data, revealed the personal data of 147 million people.
Conclusion
One of the most critical elements of contemporary cybersecurity is data encryption, which safeguards confidential information from internet attacks and unauthorized use. Encryption ensures data integrity, confidentiality, and compliance by encoding information into an unreadable format.The lack of encryption can result in reputation loss, financial loss, and data breaches. Organizations and individuals can best protect their data by implementing best practices like employing robust algorithms, keeping encryption keys secure, and training employees. Encryption isn’t a choice; it’s a requirement in an age in which information is always at risk.
References
- M. A. Mannan, “Data Privacy in E-Commerce: Challenges and Best Practices,” in Analyzing Privacy and Security Difficulties in Social Media: New Challenges and Solutions, IGI Global Scientific Publishing, 2025, pp. 415–440. doi: 10.4018/979-8-3693-9491-5.ch017.
- “Cryptography_Online-libre.pdf.” Accessed: Feb. 18, 2025. [Online]. Available: https://d1wqtxts1xzle7.cloudfront.net/70204417/Cryptography_Online-libre.pdf?1632532209=&response-content-disposition=inline%3B+filename%3DCryptography_Online.pdf&Expires=1739853858&Signature=gqyCSc7k5te9nwebC~zB0KW8azK3tr-2numyYKcBMGYd0naE-Zy3DbOHlwNj1r4VZdgdnHQKaWEDMyPefw0OeXdctsiXOpQYGjSsDJDMnoD3ds4o6rJDZefL9tPxW9Y7PIHR-4jiSeTCmWM8lRTaP~2XcR6Lj4NAPGVwJmyoGSgRm1rHQnFCCF4xt9gU3IV8z0-pKqCxLibZd7weIPnYGVCpdfInkTlKrxOtzABLZCnXlTqqU2~edAyLu6PinGbUnIlmuu32WFkU0XPo2qFxUUfUWkWRtoHJAdEwT1WJQtCnFLLcBOrvW20wts4ZPgi9AfBtsk8Y3plhUqppdJYYjw__&Key-Pair-Id=APKAJLOHF5GGSLRBV4ZA
- A. Atadoga, O. A. Farayola, B. S. Ayinla, O. O. Amoo, T. O. Abrahams, and F. Osasona, “A COMPARATIVE REVIEW OF DATA ENCRYPTION METHODS IN THE USA AND EUROPE,” Comput. Sci. IT Res. J., vol. 5, no. 2, Art. no. 2, Feb. 2024, doi: 10.51594/csitrj.v5i2.815.
- M. N. Alenezi, H. Alabdulrazzaq, and N. Q. Mohammad, “Symmetric Encryption Algorithms: Review and Evaluation study,” vol. 12, no. 2, 2020.
- “The Advantages of Data Encryption.” Accessed: Feb. 18, 2025. [Online]. Available: https://shardsecure.com/blog/advantages-data-encryption
- G. Inc GMO Internet Group, “Security Risks of Outdated Encryption,” GlobalSign. Accessed: Feb. 18, 2025. [Online]. Available: https://www.globalsign.com/en/blog/security-risks-outdated-encryption
- .Secure multi-party computation (SMPC) protocols and privacy
- M Rahaman, V Arya, SM Orozco, P Pappachan – Innovations in Modern Cryptography, 2024
- Rahaman, M., Bakkireddygari, S. S., Chattopadhyay, S., Gomez, A. L., Arya, V., & Bansal, S. (2024). Infrastructure and network security. In Advances in information security, privacy, and ethics book series (pp. 108–144). https://doi.org/10.4018/979-8-3693-3824-7.ch005
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2020). IoT-based big data secure management in the fog over a 6G wireless network. IEEE Internet of Things Journal, 8(7), 5164-5171.
- Esposito, C., Ficco, M., & Gupta, B. B. (2021). Blockchain-based authentication and authorization for smart city applications. Information Processing & Management, 58(2), 102468.
- Sahoo, S. R., & Gupta, B. B. (2021). Multiple features based approach for automatic fake news detection on social networks using deep learning. Applied Soft Computing, 100, 106983.
- Chokkappagari R. (2024) Quantum Cryptography: Securing the Internet of the Future, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) The Importance of Data Encryption, Insights2techinfo pp.1