By: Bakkireddygari Sai Sravanthi, International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, sravanthisai1113@gmail.com
Abstract
This paper examines the rising threat of smishing, a cybercrime combining SMS and phishing tactics to deceive individuals into revealing personal information or downloading malware. As mobile device usage surges globally, smishing becomes a more frequent and sophisticated threat. By leveraging the immediacy and personal nature of text messages, attackers create seemingly legitimate messages that often appear to come from trusted entities like banks or government agencies. This paper delves into the mechanics of smishing attacks, the reasons behind their increasing success, and essential techniques for identifying and preventing such attacks to safeguard financial and personal information. Understanding the intricacies of smishing and maintaining vigilance can help individuals and organizations better protect themselves against this escalating cybersecurity risk.
1. Introduction
Combining “SMS” and “phishing,” cybercrime assaults known as “smishing,” use text messages to mislead victims into disclosing personal information or downloading malware on their devices[1]. As mobile device use worldwide keeps increasing, smishing has become a more regular and complex threat. With the immediacy and personal character of text messages, attackers create convincing messages usually looking to come from reputable companies, banks, or even close friends. This article explores the mechanics of smishing attacks, the causes of their increasing success, and basic techniques for spotting and stopping such assaults to protect financial and personal information. Understanding the subtleties of smishing and being alert helps people and companies to better guard themselves against this increasing risk in cybersecurity.
SMS (short message service) combined with phishing a sophisticated cybersecurity threat using the broad usage and confidence in text messaging is smishing. Unlike traditional phishing which relies on email smishing fool’s victims with the quick and personal character of SMS. These messages are meant to seem as though they come from respectable sources, such as banks, government agencies, or well-known service providers, therefore enhancing their credibility.
One of the main features of smishing campaigns is their real look. Attackers produce these messages to pass for official correspondence, full of legitimate-looking logos, language, and phone numbers, therefore making it difficult for receivers to differentiate real from false messages. Attackers typically create urgency or fear, warning of suspicious account activity, imminent legal actions, or limited-time offers, therefore compelling recipients to react rapidly without closely reviewing the legitimacy of the information.
Mostly, smishing methods consist of a strong call to action. Usually advised to click on a website, call a phone number, or answer with personal information are victims[2]. Depending on what you do, these could lead to varied negative consequences including direct attacker contact, launching malware downloads, or leading people to phishing websites. Seeking sensitive information such as credit card numbers, login credentials, and personal identifying details, phishing websites linked in smishing messages closely mirror authorized ones.
2. How Does Smishing Work?
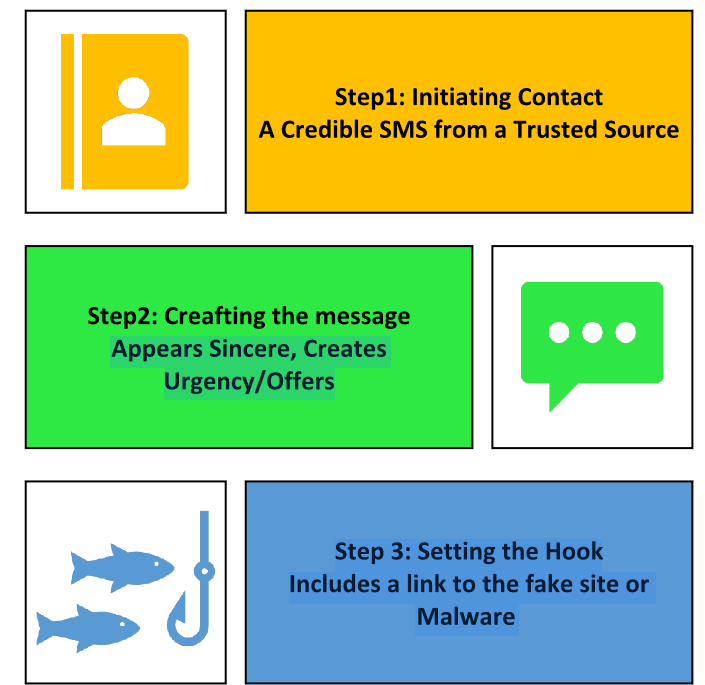
Smishing targets victims into revealing private information or launching dangerous apps on their devices by use of bogus SMS texts. Usually, this is the pattern. Refer to Fig 1.
Step 1: Initiating Contact
Smishing begins with an innocuous SMS message. Usually mirroring a respectable source, a bank, tax authority, family member, or company this remark sounds reliable and credible.
Step 2: Crafting the Message
Smishing is most effective when it stimulates listeners to respond by clearly conveying to them the message is sincere. These well-crafted messages are supposed to either present a good bargain or build urgency.
Step 3: Setting the Hook
Usually, the text message comprises a link or a directive for action. This link might result in a phony website that closely resembles a real one where victims are urged to input credit card data, social security numbers, or login credentials, therefore posing a threat. On the other hand, the link might cause malware to download onto the recipient’s device, which could then be used to monitor activity, pilfer data, or take over the device[3].
2. The Mechanics of Smishing Attacks
Smishing attacks using a range of deceptive techniques cause victims to download malware onto their devices or reveal confidential information. These strategies are meant to profit from human psychology and confidence in SMS messaging. These are the main elements and techniques employed in smishing campaigns. Refer to Table 1
Phony Alerts and Notifications: Text messages sent by attackers sometimes seem to originate from reputable sources government institutions, or service providers, for example. These messages notify recipients of critical account or service problems including security alerts, pending payments, or suspicious activities. The urgency is meant to inspire quick response; hence recipients click on a link or contact a number without confirming the validity of the message.
Malicious Links: Standard practice in smishing includes links leading victims to phony websites designed to look like authentic ones. With logos and branding, these websites are meant to resemble almost exactly real ones. Once on the site, users are advised to enter important information including login credentials, social security numbers, or credit card details. The attackers then compile this information for use in fraudulent activities.
Malware Distribution: When clicked, links or attachments seen in some smishing messages initiate the virus download on the victim’s device. Among the numerous negative behaviors this virus could engage in include keystroke recording, data collecting, communication monitoring, even device control. From this one can follow severe compromises of personal and financial security.
Social Engineering: Attackers convince victims to divulge personal information using advanced social engineering methods. Under pretenses, they could pose trustworthy connections or authority figures family members, colleagues, or officials and seek sensitive information. Attackers raise the possibility of victims following their demands by misusing relationships and seeming power.
Spoofed Numbers: Sometimes attackers pick phone numbers that sound like those of respectable businesses to increase the belief in their messages. Sometimes called number spoofing, this approach makes it more difficult for receivers to distinguish actual from fake messages. Seeing a known or trusted number helps the recipient to let go of her defenses, therefore increasing the possibility of an efficient attack.
Urgency and Fear: Often using strategies meant to generate hurry or anxiety, smishing messages Typically, the recipient’s account has been hacked or quick action is needed to prevent fines. Usually ignoring the validity of the communication or the expected outcomes, this psychological pressure drives recipients to react fast.
Enticing Offers: Sometimes smishing tactics include promises of rewards, awards, or special offers to lure consumers to click on dangerous links. These presents are meant to appeal to the recipient’s needs or curiosity, which will cause them to interact with the message and maybe become victims of fraud.
Malware Links: Links in smishing messages could lead to websites that download malware of their own choice. From spyware and adware to more dangerous forms like ransomware, which could lock people off their devices or data until a ransom is paid, the nature of this infection may differ. The presence of malware greatly raises the risk and consequences of a smishing attack[4].
Technique | Description | Example |
Phony Alerts and Notifications | Messages mimicking banks or government agencies to create urgency and prompt quick response. | “Your account has suspicious activity, click here to verify.” |
Malicious Links | Links lead to fake websites designed to steal personal information. | “Click here to reset your password.” |
Malware Distribution | Links or attachments that download malware onto the victim’s device. | “Download this app to claim your prize.” |
Social Engineering | Using trust and authority to deceive victims into revealing sensitive information. | “This is your boss, send me your login details.” |
Spoofed Numbers | Messages appear to come from familiar or trusted numbers to increase credibility. | “Verification code from your bank: 123456.” |
Urgency and Fear | Creating a sense of urgency to prompt immediate action without verification. | “Your account will be locked in 24 hours if not verified.” |
Enticing Offers | Promising rewards or prizes to lure victims into clicking links or providing information. | “You’ve won a gift card! Click here to claim it.” |
3. Effectiveness of Smishing Attacks
Smishing attacks are particularly effective due to several key factors:
Higher Click Rates: Studies on raised clicks show that text message links are considerably more clickable than email links. This is so because text messages are considered as faster readable and more personal. Perfect candidates for smishing attacks, SMS receivers are less cautious and more responsive.
Lack of Awareness: Public misunderstanding of the dangers makes smishing successful. Few consumers know that SMS phishing works as much as email phishing. Lack of knowledge makes people more prone to smishing frauds since do not check textbooks as carefully.
Limited Spam Filters: SMS messages lack strong security and spam filtering, unlike emails. More dangerous literature is sent to consumers without their being observed or prevented. Damage messages are more likely to find their targets when SMS infrastructure is not secured.
4. Examples of Smishing Attacks
The most frequent smishing attack would include messages that the attacker pretends to originate from a victim’s bank[5]. These messages inform the recipient about a security problem on his/her account and encourage the user to check the account details by clicking on the given link. The link takes the user to a fake login page to get the victims to input their banking details including their login information and PINs where the attacker can easily log into the victim’s bank account and make transactions that will benefit the attacker but harm the victim. Another common smishing message that people receive claims to be from courier services. There are these messages, which state that a parcel could not be delivered and urge the receiver to click a link to order the delivery instead. The link may take the user to what looks like a legitimate site, but it tricks the user into inputting their details, or the link may install a virus in the user’s computer which enables the attacker to gain control over the computer and steal the user’s data.
Prizes and rewards are common tricks used by smishing attackers and as seen above are very effective. A victim gets to his or her email where he or she finds a message notifying him or her that he or she has won a prize and all that is required of him or her is to click a link. This link normally directs users to sites where they are asked to submit personal details or cause a software download. The desire to claim a prize or possess something that is seen as valuable distorts the recipients’ reason, making them more susceptive to the scams.
Example | Description |
Bank Security Alert | An attacker sends a message claiming to be from the victim’s bank, asking them to verify account details. |
Courier Delivery Notification | A message claiming a parcel could not be delivered, asking the victim to click a link to reschedule. |
Prize Winning Message | A message informing the victim they have won a prize and need to click a link or provide personal information. |
5. Impact on Mobile Security
Smishing creates a highly dangerous threat to mobile protection as it involves leakage of the client’s information, loss of cash, and stolen individuality. Mobile devices tend to be more prone to such threats because they are not usually equipped with protection on the level of standard PCs. Also, users are somewhat more trusting of text messages, positively affecting the smishing tactics’ success rate over email phishing practices.
Studies show that smishing attacks have been increasing over the recent past. In a study conducted by Jain et al., the identification and combating of smishing remain primary due to the increased exploitation of the gaps in the SMS conversation. Hybrid smishing attacks are described in them as requiring better algorithms in machine learning to help in prevention[6].
6. Identifying Smishing Attacks
The best way for a user to defend himself from smishing is when a user is well informed of the signs of a smishing attack. The first signal is that when a partner’s behavior is out of the ordinary, there may be a message from them that was not expected. Avoid messages from people you do not know, or are strangers to, people asking for personal details. Such messages can be very spontaneous, talking about some emergent situation or presenting some marvelous opportunities that should not be missed. Another major issue to look at as a sign of low-quality content is the grammatical and spelling mistakes. Most smishing messages contain simple grammatical mistakes, and if that is not the case, other features are usually noticeable, implying that they are fake.
If you have many unidentified connections, then they are another very informative warning signal. Do not click links from people you do not know or if you receive an email from someone in your contact list but with an odd link, be very careful because this can lead to phishing sites or downloading of malware. The URL should always be checked by typing it into a web browser manually or by contacting the sender/organization via official means. Hasty calls should also not be trusted. Most smishing messages are meant to give the recipient a sense of danger/urgency and compel them to act immediately e.g., notification of suspicious activities on your account or we will freeze your account, or you will be charged x amount.
Verification is always important in situations like smishing, which involves the use of links and putting in phone numbers. If you received a phishing email or text message then respond to the message claiming to be from the company using the phone numbers or addresses given on a different message or the back of a credit card, and so on. Never reply to the message or use any of the contact details that were relayed in the message as they may be fake. Therefore, by recognizing these signs and confirming any doubts, the users will safeguard themselves from smishing and their personal information.
7. Prevention Strategies
Several strategies can help mitigate the risk of smishing attacks:
Education and Awareness: Regular education and awareness are among the best strategies available for preventing smishing. Companies and people should be educated on the dangers of smishing and taught how to recognize suspicious communications. These cover an understanding of typical attack strategies like urgency, unwanted requests for personal data, and suspicious connections. Frequent seminars, updates, and educational materials help consumers remain aware of the most recent dangers and preventative measures.
Security Software: Preventing smishing depends on using strong security programs. Features like SMS filtering and malware prevention, which can help find and stop harmful messages before they get to the user, abound in many of these programs. Another layer of protection is provided by security software, which can additionally identify and destroy malware potentially obtained by smishing links.
Two-Factor Authentication: Two-factor authentication (2FA) gives sensitive accounts a vital layer of security. Even if attackers use smishing to get login credentials, 2FA would still be necessary for access to the account usually a code delivered to a mobile device or an authentication app. This greatly lessens the possibility of illegal access and helps to stop the use of hacked credentials.
Report Smishing: Fighting these assaults depends critically on reporting smishing efforts to pertinent authorities and mobile providers. Users assist carriers and security firms in tracking and blocking harmful numbers by reporting strange texts, therefore slowing the impact of smishing efforts. Most carriers offer simple methods to report smishing, and by doing so you can help more general initiatives to neutralize this menace.
Regular Updates: Protecting against the newest dangers depends critically on routinely updating mobile devices and security tools. Security patches included in updates can solve recently identified vulnerabilities, therefore making it more difficult for attackers to use out-of-date software. To guarantee they are always covered by the most recent security improvements, users should turn on automatic updates for their devices and apps.
8. Machine Learning-Based Prevention Strategies
More complex approaches for spotting and stopping smishing attempts have come from recent developments in machine learning (ML)[6]. These innovative approaches greatly improve the capacity to find and stop harmful messages by using ML to examine patterns, behaviors, and content in real time.
Content and URL Analysis: Using the content and URLs found in SMS messages, machine learning models find trends suggestive of smishing. Suspicious language and phishing URLs are found using methods including natural language processing (NLP). By helping the system grasp the context and semantics of the communication, NLP flags odd words or links usually connected to phishing efforts. This helps to more precisely identify smishing communications that might not be immediately apparent to human recipients.
Behavioral Analysis: By monitoring and assessing user behavior, ML models can find abnormalities suggestive of a smishing assault. For example, this unusual behavior can set off an alarm if a user hits a link right away after getting a message from an unidentified number. Behavioral analysis models evaluate user interactions with messages over time, therefore creating a baseline of normal behavior and spotting deviations that might indicate a security risk. This proactive method aids in the identification of smishing efforts dependent on quick, out-of-character reactions by users.
Ensemble Learning: Combining several machine learning techniques helps smishing detection to be more accurate. To provide a stronger detection system, ensemble learning methods combine several algorithms like neural networks, random forests, and decision trees. Using the strengths of several models allows ensemble learning to offer a more complete study, hence lowering false positives, and enhancing the recognition of smishing messages. This diversified strategy guarantees that even the most deftly veiled attacks are more likely to be seen[7].
Transformers and Deep Learning: Transformers and other advanced models help one recognize the context and semantics of SMS material. Transformers, which have altered NLP tasks, can find minute signals in the text that conventional techniques would detect. Trained on vast collections of both benign and harmful communications, deep learning algorithms can identify intricate trends and relationships inside the text. These models are very good at spotting complex smishing efforts with sensitive language and dishonest strategies.
Real-Time Detection Systems: Real-time detection systems using ML to rapidly assess incoming messages can assist stop smishing efforts before they get to the user. By including these technologies in SMS gateways and mobile security apps, constant smishing protection is offered. Using ML algorithms’ speed and efficiency, real-time detection scans communications as they arrive to provide instant defense against possible hazards. This proactive step guarantees quick protection from smishing attempts for users[8].
9. Conclusion:
Smishing, a blend of SMS and phishing, poses a significant threat to mobile security by exploiting the trust in text messaging. Its effectiveness stems from the personal nature of SMS and the lack of robust security measures. Attackers craft convincing messages mimicking legitimate sources, using urgency and fear to prompt immediate responses. Key prevention strategies include education, awareness, security software, two-factor authentication, and reporting suspicious messages. Advancements in machine learning, such as content and URL analysis, behavioral analysis, and deep learning, offer promising real-time detection and prevention solutions. Staying informed and proactive is crucial to mitigate risks and protect personal and financial information from this growing cyber threat.
References:
- “What Is Smishing (SMS Phishing)? | IBM.” Accessed: Jul. 28, 2024. [Online]. Available: https://www.ibm.com/topics/smishing
- “Phishing: Spot and report scam emails, texts, websites and calls.” Accessed: Jul. 28, 2024. [Online]. Available: https://www.ncsc.gov.uk/collection/phishing-scams
- “Users Really Do Respond To Smishing | Proceedings of the Thirteenth ACM Conference on Data and Application Security and Privacy.” Accessed: Jul. 28, 2024. [Online]. Available: https://dl.acm.org/doi/abs/10.1145/3577923.3583640
- P. Y. Leonov, A. V. Vorobyev, A. A. Ezhova, O. S. Kotelyanets, A. K. Zavalishina, and N. V. Morozov, “The Main Social Engineering Techniques Aimed at Hacking Information Systems,” in 2021 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), May 2021, pp. 0471–0473. doi: 10.1109/USBEREIT51232.2021.9455031.
- Shweta, “What Is Smishing? Definition, Examples & Protection,” Forbes Advisor. Accessed: Jul. 28, 2024. [Online]. Available: https://www.forbes.com/advisor/business/what-is-smishing/
- “(PDF) A Machine Learning-based Approach for Detecting Smishing Attacks at End-user Level,” in ResearchGate, doi: 10.1109/ICEBE59045.2023.00042.
- “Ensemble Learning | SpringerLink.” Accessed: Jul. 28, 2024. [Online]. Available: https://link.springer.com/chapter/10.1007/978-1-4419-9326-7_1
- F. Tango and M. Botta, “Real-Time Detection System of Driver Distraction Using Machine Learning,” IEEE Trans. Intell. Transp. Syst., vol. 14, no. 2, pp. 894–905, Jun. 2013, doi: 10.1109/TITS.2013.2247760.
- Gaurav, A., et al. (2023, October). Adaptive Defense Mechanisms Against Phishing Threats in 6G Wireless Environments. In 2023 IEEE 98th Vehicular Technology Conference (VTC2023-Fall) (pp. 1-5). IEEE.
- Abd El-Latif, A. A., Hammad, M. A., Maleh, Y., Gupta, B. B., & Mazurczyk, W. (Eds.). (2023). Artificial Intelligence for Biometrics and Cybersecurity: Technology and Applications. IET.
- Almomani, A., Alauthman, M., Shatnawi, M. T., Alweshah, M., Alrosan, A., Alomoush, W., & Gupta, B. B. (2022). Phishing website detection with semantic features based on machine learning classifiers: a comparative study. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-24.
Cite As
Sravanthi B.S. (2024)
The Rise of Smishing: How SMS Phishing Attacks are Negotiating Mobile Security, Insights2Techinfo, pp.1