By: Bakkireddygari Sai Sravanthi, International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, sravanthisai1113@gmail.com
Abstract
Vishing is an emerging form of cybercrime in which attackers employ phone calls to trick victims into revealing confidential financial and personal data. Vishing exploits the promptness and reliability of voice communication, in contrast to conventional phishing methods. This study examines the mechanics of vishing, differentiating it from other types of phishing, discussing typical objectives and techniques employed, and providing strategies for identifying and thwarting such fraudulent schemes. In addition, it explores AI-based methods to mitigate vishing, such as call screening, natural language processing, behavioral analytics, automated threat intelligence, and voice biometrics, to strengthen defense against this type of attack.
1. Introduction to Vishing and Its Growing Threat
A cybercrime combining “voice” with “phishing,” vishing, is one in which attackers trick victims into disclosing sensitive financial and personal information by phone calls[1]. Unlike traditional phishing based on emails, vishing uses the immediacy and trust of phone conversations. As technology advances, vishing has changed to include caller ID spoofing and artificial intelligence-generated deepfake voices to create realistic frauds. Maintaining private data requires an understanding of vishing since these scams can lead to identity theft and significant financial loss.
Increasing threats of Vishing scams have continued to rise with the statistics showing a steep rise of more than 550 percent between Q1 2021 and Q1 2022. To this end, the level of incidence has increased mainly due to voice-based frauds which are designed to make the victim act in haste or out of fear by pretending to be from a trustworthy organization. This makes vishing especially risky because people typically tend to put a lot of trust in voice communication. Phishing is a common type of tactic where the attacker disguises as a trustworthy source like a bank, government body, or anyone relating to computer support, and defraud them.
This implies that for individuals to protect their selves and their money from attackers hoping to fleece them out of their money, then vishing awareness and understanding are of paramount importance. Proceeding further, people will be able to recognize frequent schemes vishers use and potential signals of the call’s deceit. Awareness of avoidance techniques namely checking the identity of the caller, avoiding the disclosure of personal information when called, and using the caller ID option helps in preventing vishing attacks. Also, the developments in AI and machine learning can be used to identify these attacks and improve overall security.
2. What is Vishing?
Vishing, also termed as voice phishing is a style of cybercrime in which false telephone calls are made to a person to mislead the target into divulging his or her details. While vishing is distinct from traditional phishing in which false emails, text messages, and other forms are used to steal information, vishing takes advantage of the direct and trusted face-to-face nature of voice calls. Such con often takes the form of cloning the organizations the scammers are portraying as the real deal to make the victims provide sensitive information[2].
3. How Vishing Differs from Other Phishing Types:
Medium of Communication: Vishing utilizes phone calls on the other hand, phishing majorly employs emails or sends text messages which are referred to as smishing.
Immediacy and Pressure: Vishing is carried out online in real time putting pressure on the victims and thus does not give the victims enough time to think very hard like in the case of email or text scams.
Caller ID Spoofing: Remarkably, vishing usually entails that the caller disguises the number to make the call seem authentic, unlike in the case of e-mail phishing, where the e-mail address is fake or intercepted[3].
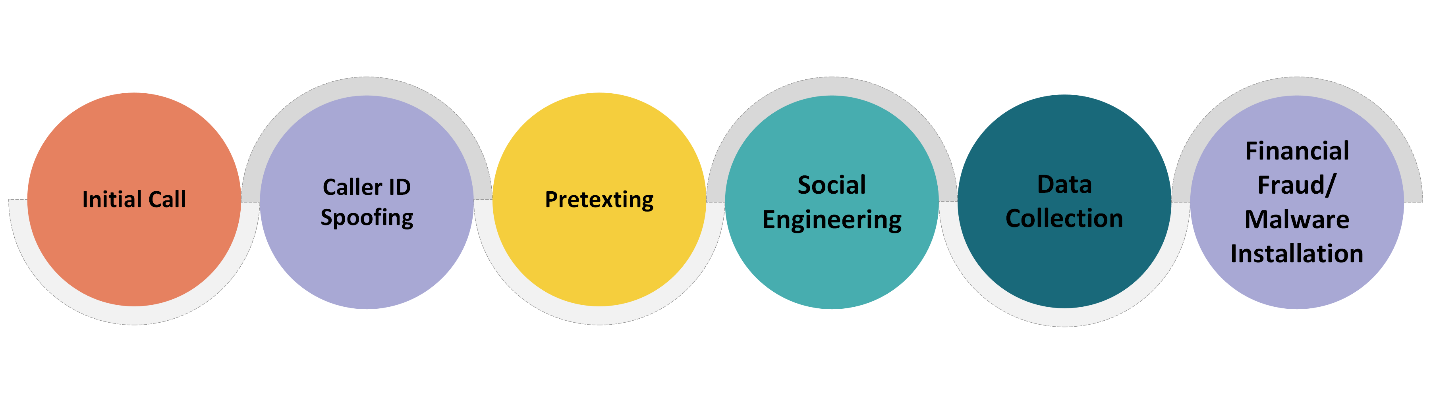
4. Common objectives of vishing scams
Stealing Personal Information: Procedures often seek to obtain the targeted user’s account number or driver’s license number, social security number, address, birth date, and password. This information can be used for identity theft whereby criminals use the information obtained to open credit accounts or apply for loans and any other unlawful activity they wish to carry out in the victim’s identity.
Financial Fraud: One common goal that many vishing scams have therefore is to try and obtain the financial credentials of the victims. These might pretend to be from the victim’s bank and inform him/her of there being some suspicious transactions in the account, and therefore ask for the account details or the login credentials. The said information is then utilized in the process of directly stealing money from the accounts of the victim. Other related ones are Tech support scams whereby the victim they are offered unnecessary services or software to pay for, apparently using a fake credit card.
Installing Malware: Sometimes, the vishing calls will urge victims to access a website or an application where they are likely to download entities that will corrupt their devices. Once installed, this malware can be employed for purposes such as extracting information, spying, or even taking over the victim’s computer remotely.
Social Engineering Attacks: Moreover, Vishing like other forms of phishing, uses social engineering methods to influence the emotions of the victims. Such commonly include portraying they are a relative in need of immediate cash or a representative of a reputable organization calling for an immediate response based on fear, trust, and compassion[4].
5. Techniques Used in Vishing
Caller ID Spoofing: Identity spoofing is one of the most typical types of vishing where the attackers deceive the caller ID information to seem like the call is originating from a legal source. This is done by making use of a code or service that changes the shown number so that the victim is likely to believe the caller. Now and then some organizations experience high levels of pharming, and these are the organizations that they mimic; these include banks, government institutions, and technological support. For instance, a victim occasionally receives a phone call that comes along with a message that their bank account appears to have been compromised and needs them to give more account information to sort it out.
Pretexting: This form of social engineering entails coming up with a pretense to induce the victim into a particular action, to get the victim to disclose more details. Worms and viruses pose believable stories to do what they want, backed by often impressive research. Examples of such pretexts are emergent events like Suspicious account activity or security alerts where the victim is pressured to act quickly because there is something to lose or face the law. Its effectiveness in this is astonishing since it creates a quick feel, and the victim is forced to do as the caller instructs without worrying whether the caller the real thing[5].
Social Engineering: vishing in social engineering is different from the other categories because it relies on an ability to change the victim’s behavior by appealing to the emotions of the victim. Subtle tactics trigger rational or irrational feelings like the fear of being harmed the trust in the sender, or even compassion. Such strategies are the pressure that comes with threats such as a fake call demanding urgent pay to avoid adverse outcomes being a call from banks or government officials or even posing to be a relative in dire straits. These are sick strategies that are meant to work around the rational mind of the recipient with a view of eliciting personal details from him/her.
Robocalls and Automated Messages: Pre-recorded messages or Robocalls and Automated messages are adopted by vishers to contact a massive number of prospects within a short duration. This is normally a recorded message that sounds rather official and that triggers a sense of urgency on the part of the recipient. Subtypes include the receipt of alerts by banks regarding unusual transactions, tech support messages stating that computer systems are infected by viruses, and government messages stating the balance of past-due taxes. The aim is to make the victim return the courtesy of a call to a specific number, enter a website link, or give out personal details on the phone. This method takes advantage of the auto-generated calls to make the calls seem somewhat official and impending[6].
6. Recognizing Vishing Scams
Common Red Flags
The signs of a vishing scam are like those of other kinds of scams, but one of the most obvious ones is guilt by pressure. Scammers put a lot of pressure on their messages indicating that urgent action should be taken as the account will be suspended, you will be taken to court, or you will lose lots of money. This feeling of urgency is intended to cloud the victim’s rational decision-making and make them act impulsively. This is followed by the most obvious red mark which is the one whereby the sender solicits personal or financial details. Scam organizations can easily pose as genuine ones and hence they especially do not request vital information like social security numbers, banking details, or passwords via the telephone. This is an indication of a possible vishing scam if a caller is specifically asking for this information. Besides, communicating via calls from unknown or hidden numbers should also be treated with certain measures of caution. Although caller ID spoofing can be used by scammers to display several a called person’s choices, receiving an unexpected call from an unknown number may be a sign of vishing[7].
Common Red Flags in Vishing Scams:
Red Flag | Explanation |
Urgent Action Required | Scammers create a sense of urgency to prompt immediate action |
Request for Personal/Financial Information | Legitimate organizations don’t ask for sensitive info over unsolicited calls |
Unknown/Hidden Numbers | Unexpected calls from unknown numbers should be treated with caution |
Threats or Legal Consequences | Scammers often use threats to coerce victims into complying |
Requests to Visit a Website or Download | Directing victims to malicious websites or downloads to install malware |
Examples of Vishing Scenarios
The most frequently reported type of vishing is when the attackers pretend to be calling from a bank to report suspicious transactions. The attacker pretends to be an officer from the bank and comes with the message that there have been strange transactions on the account. The caller then presents the case that the account of the victim is at risk and then proceeds to request the victim’s account information or login credentials to fix the account. This fraud causes the victim to tighten up by panicking that they will lose the funds and rely on the fact that they are using their bank. The other common vishing scenario that is on the rise is the fake IRS or a tax authority call. In this case, the caller assumes the authority of the Internal Revenue Service or another revenue service, telling the victim that they are owed money in taxes and must pay right away to avoid being arrested or facing some legal consequences[8]. This sort of fraud depends on the victim’s appreciation, and rightly so, of the legal backlash and the authority of governmental agencies. That is why technical support scams are also prevalent in vishing. The attacker disguises him as a technology support personnel from recognizable and authoritative companies such as Microsoft or Apple, who notifies the victim their computer has a virus, or the account is compromised. The scammer then directs the victim to download some programs or share the password to their computer, and the next thing you know is the malware infiltration or the stealing of personal information.
In this context, it is appropriate to list the main encountered red flags while recognizing the general vishing situations to protect oneself from being deceived by such clever fraud schemes. Knowing the tactics applied by the vishers and using precaution when dealing with such calls and other requests is a long way toward protecting personal and financial information.
7. How to Protect Yourself from Vishing
Verify Caller Identity: Avoid vishing incidents by always confirming the caller’s identity before you give him/her any details. When the received call is fake, one should ask for the name of the called person, department, and telephone number for a return call. That information should not be a problem with any genuine representative of the modafinil community. Also, do not use the phone number that the caller provides to you but use other numbers that belong to the organization that you can find on the organization’s website or any official document. If for example, your caller pretends to be from your bank, just hang the call and instead dial the bank service contact number indicated in your statement or the bank’s website.
Do Not Share Personal Information: Do not provide your personal or any financial information to anyone over the phone unless sure of their identity. Normal organizations cannot call their clients and tell them to give them their details. Avoid believing the caller’s requests for personal information like social security numbers, bank account numbers, and passwords. Because it is safer to take any unexpected call, which requires personal details, as a possible vishing attempt.
Use Call Blocking and Screening Tools: Use call blocking and call screening to prevent cases of vishing. Some of the common smartphones have options that allow users to block such calls as those from unidentified numbers or unwanted callers. Furthermore, it is necessary to mention that there are many applications and services for call filtering. In this case, applications such as Hiya, True Caller, as well as Nanorobot will be useful since they can help identify the scam numbers. These tools can dramatically minimize the probability of falling victim to vishing since these calls do not get through to you.
Report Vishing Attempts: Hence, it is helpful to report vishing attempts to the right authorities in fighting such scams. If the call was from a scammer, the identity of the caller together with details of the call should be forwarded to the FTC via the internet or the helpline. Also, contact your telephone line service provider, they will safeguard you by blocking the number used in the scams. Reporting vishing attempts prevents scammers as authorities are alerted to shut down such activities, hence saving more people[9].
8. AI-Related Mitigation Techniques
AI-Powered Call Screening: Real-time analysis of incoming calls by AI-powered call screening systems finds vishing signals. These instruments assess many facets of a call, including caller number, call history, and voice patterns, using sophisticated algorithms. AI can flag dubious calls and notify the user by matching this data with known vishing traits. Real-time analysis, which enables instantaneous identification and intervention, and voice recognition which can find irregularities or inconsistencies in the caller’s speech are features of AI-based call screening. To improve their detecting powers, these systems can also interact with databases containing known fraud figures.
Natural Language Processing (NLP): NLP is a great tool in identifying vishing efforts since it helps artificial intelligence to grasp and analyze human language. Through language pattern analysis of a call, NLP can find often-used suspect phrases or scripts connected to fraud. NLP can highlight, for example, calls including urgent demands for personal information or legal action threats. Using natural language processing, identify scam calls by tracking customer service contacts for possible fraud and red flag scanning of recorded calls suggestive of vishing. This feature helps to spot and stop vishing attempts before they may damage the victim.
Behavioral Analytics: Behavioral analytics is the application of artificial intelligence to examine caller behavior and identify anomalies suggestive of a vishing effort. This approach looks at calls’ frequency and caller interaction with the recipient. An artificial intelligence system might, for instance, detect whether a caller deviates from usual conversation patterns, is too persistent, or employs manipulative strategies. AI can assist find and stop vishing scams by spotting certain behavioral warning flags. In call centers, where it can track interactions and notify workers to real-time possible risks, behavioral analytics is especially helpful.
Automated Threat Intelligence: Using artificial intelligence, automated threat intelligence systems compile, examine, and share knowledge on recognized vishing methods. These systems regularly update databases with the newest vishing trends and techniques, which can subsequently be applied to improve call screening instruments. Threat intelligence combined with call screening lets one create a more complete security since artificial intelligence can use current data to find and stop developing dangers. Faster response times, better detection accuracy, and the capacity to change with new vishing techniques as they develop are advantages of this strategy.
Voice Biometrics: Through analysis of distinctive vocal traits including pitch, tone, and speech patterns, voice biometrics authenticates callers. By matching the caller’s voice to a pre-recorded voice print, this technology can separate between genuine callers and frauds. Using voice biometrics to guard against vishing means confirming callers’ identities before sensitive data distribution. Voice biometrics, for example, allow financial organizations to verify the identity of a caller asserting to be a customer. This extra layer of protection helps stop illegal access and lowers the possibility of vishing schemes[10-13].
AI Techniques in Vishing Detection:
Technique | Application |
AI-Powered Call Screening | Real-time call analysis to detect vishing indicators |
Natural Language Processing | Identifying suspicious language patterns in calls |
Behavioral Analytics | Analyzing caller behavior for anomalies |
Automated Threat Intelligence | Using updated threat data to improve call screening |
Voice Biometrics | Authenticating callers based on unique voice characteristics |
Conclusion
It is of utmost importance to acknowledge and prevent vishing scams at a time when hackers are increasingly taking advantage of the trust that is naturally associated with voice communication. To enhance the security of their personal and financial information, individuals might acquire a better grasp of the typical methods and warning signs related to vishing. Common strategies employed by vishers include techniques such as caller ID spoofing, pretexting, social engineering, and the utilization of robocalls. AI-driven technologies, including call screening, natural language processing, behavioral analytics, and voice biometrics, provide sophisticated techniques for identifying and stopping these fraudulent activities. Remaining attentive and well-informed is crucial for protecting oneself against the substantial financial and personal dangers presented by vishing.
References:
- “What is Vishing?” Accessed: Jul. 26, 2024. [Online]. Available: https://www.terranovasecurity.com/solutions/security-awareness-training/what-is-vishing
- “Phishing—A Cyber Fraud: The Types, Implications and Governance – Mazurina Mohd Ali, Nur Farhana Mohd Zaharon, 2024.” Accessed: Jul. 28, 2024. [Online]. Available: https://journals.sagepub.com/doi/abs/10.1177/10567879221082966
- “Smishing vs. Phishing vs. Vishing | HP® Tech Takes.” Accessed: Jul. 28, 2024. [Online]. Available: https://www.hp.com/us-en/shop/tech-takes/smishing-vs-phishing-vs-vishing
- N. L. Shete, M. Maddel, and Z. Shaikh, “A Comparative Analysis of Cybersecurity Scams: Unveiling the Evolution from Past to Present,” in 2024 IEEE 9th International Conference for Convergence in Technology (I2CT), Apr. 2024, pp. 1–8. doi: 10.1109/I2CT61223.2024.10543498.
- M. Spinapolice, “Mitigating the risk of social engineering attacks,” Theses, Jan. 2011, [Online]. Available: https://repository.rit.edu/theses/394
- “Defining Social Engineering in Cybersecurity | IEEE Journals & Magazine | IEEE Xplore.” Accessed: Jul. 28, 2024. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9087851
- “Online frauds: Learning from victims why they fall for these scams – Mark Button, Carol McNaughton Nicholls, Jane Kerr, Rachael Owen, 2014.” Accessed: Jul. 28, 2024. [Online]. Available: https://journals.sagepub.com/doi/abs/10.1177/0004865814521224
- “8 Examples of Vishing and How to Beat Them | Terranova Security.” Accessed: Jul. 28, 2024. [Online]. Available: https://www.terranovasecurity.com/blog/examples-vishing
- R. Amond, “How to recognize a vishing scam and protect yourself from attack,” CNBC. Accessed: Jul. 28, 2024. [Online]. Available: https://www.cnbc.com/select/what-is-vishing-and-how-to-prevent/
- J. Cox, “What Is Voice Biometrics?,” Plum Voice. Accessed: Jul. 28, 2024. [Online]. Available: https://www.plumvoice.com/resources/blog/voice-biometrics/
- Vajrobol, V., et al. (2024). Mutual information based logistic regression for phishing URL detection. Cyber Security and Applications, 2, 100044.
- Gaurav, A., et al. (2024, January). Enhancing Email Security in Consumer Electronics with a Hybrid Deep Learning Approach. In 2024 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-5). IEEE.
- Gupta, B. B., Gaurav, A., & Chui, K. T. (2023). Convolution neural network (CNN) based phishing attack detection model for e-business in enterprise information systems.
Cite Aa
Sravanthi B,S, (2024) Understanding Vishing: The Tactics Behind Voice Phishing Scams, Insights2Techifo