By: Nicko Cajes; Northern Bukidnon State College, Philippines
Abstract
A type of phishing which utilizes SMS is known as smishing, it is one of the rapidly growing cyber-threats that conduct illegal activities through mobile devices, resulting in a huge financial loss and data theft. Frequently used methods by the attackers are fake banking, delivery scams, and emotional manipulation to successfully disclose important information from the user. With the huge potential threat, effective mitigation techniques are needed to prevent being a victim by this attack.
Introduction
The most prevalent popular method of conversation nowadays is the Short Messaging Services (SMS) [1], as it is a vital part of modern online communication due to its extensive availability, affordability, dependability, and instantaneous information delivery [2]. The emergence of mobile devices has become a field of remarkable advancement and expansion alongside the emergence of smart cities and smart homes [3]. However, because of their extensive usage and persistent connectivity on the Internet, mobile devices are susceptible to smishing attacks [4]. A fast-expanding cyber threat which results with substantial monetary damage is Smishing [5]. The number of fraudulent SMS messages has significantly increased in the past few years due to the emergence of this novel security danger [1]. Conventional anti-phishing techniques including rule-based and blacklist methodologies tend to find it difficult to cope up with the constantly evolving attack strategies [6]. This paper aims to effectively understand and prevent SMS phishing attacks, in accordance to combat the rising record of smishing attacks.
What is Smishing?
Smishing is a renowned online security threat, which takes place whenever an attacker sends harmful messages via SMS to potential victims and is a fraudulent technique under Phishing attacks [4]. Smishing messages pretend to originate within financial institutions, trusted authorities, or prominent firms which contain links or contact information, tempting potential victims to reveal confidential data or open sites which are dangerous and fraudulent [2]. Together with the increasing use of mobile devices, things have gotten more complicated making it harder for people to tell the difference between harmful and harmless messages [6].
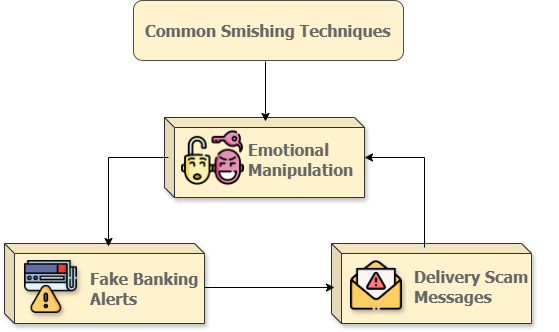
Common Smishing Techniques
Smishing attacks can get into various ways to effectively deceive victims. This includes social engineering tactics concerning data pertaining to personal and financial matters utilizing sentimental messages and a sense of panic to control the victim and increase the chance of the attack to be successful [7, 8]. The following are the most common techniques used by the smishing attackers and are shown in figure 2.
Fake Banking Alerts: This kind of fraud develops a sense of panic towards the victim, believing that they must complete the task immediately in order to access their account again. The message typically has a link which takes the victim straight to a fraudulent website where bank credentials could be collected [9].
Delivery Scam Messages: The attacker creates fake texts which notify and may inform the victim that the initial delivery was unsuccessful and request the victim to visit the link provided to change the date of delivery, which usually indicate that the victim should change the delivery settings even though the product was already set to be delivered, instilling a feel of hurry via threatening to give back the victims delivery to its seller the moment the victim don’t reply immediately [10].
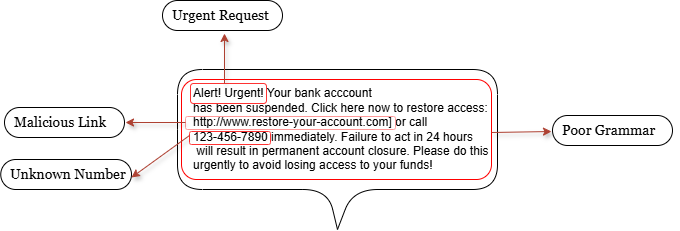
Warning Signs of a Smishing Attacks
Since it is easy to send and receive SMS, it is important to accurately judge what are legitimate and fraudulent messages based on their characteristics, as this will suggest an important area of effectively identifying smishing attacks. The following are some of the common signs of a smishing attack.
Suspicious Links and number: Smishing messages may have some questionable elements including links and URLs, however if it doesn’t include a URL that would take the recipient to a fraudulent website, it won’t be able to cause much damage if the recipient won’t call the number which the sender provides in the content of the message [3].
Poor Grammar: Grammar and typographical problems are recognized as warning signs in attacks involving smishing as it becomes one of concrete basis to identify smishing attack, this is quite important considering to the evolution of smishing attacks and to avoid the mistakes done by the participants of the study conducted by [5] which hardly ever focused on these mistakes, which could have led them to miss the important hint for spotting fraudulent texts.
Messages with Urgent Requests: Smishing messages frequently create an overall feeling of urgency, taking advantage of SMS’s quick characteristic making it more difficult for recipients to spot the fraud, keyword terms like “free”, “urgent”, and “click here” are few of the most frequently link words on a phishing attack and is an important marker [6]. This word encourages victims to engage in dangerous activities, such as opening harmful files or visiting suspicious links [5].
Impact of Smishing Attack
The fast expansion of smishing security threats results in a major financial loss, theft of personal information, and privacy issues [5, 11]. By using psychological deception and social engineering techniques to send misleading texts, the increasing danger of smishing attacks have not gone unnoticed [11]. The importance of solving this problem has been reflected in the real-life incidents involving a huge financial loss and other privacy issues which happened in the past. Recent frauds involving COVID-19, insurance, meals delivery, and government-funded projects have caused major damage specifically on finance was determined by the UK Finance, highlighting how urgent it is to solve this problem [12]. One of the major problems in SMS platform that made this attack prominent is the absence of graphical information which can be seen easily in an email message, which might help determined the validity of the messages, absence of these variable causes a financial loss to skyrocket from $86 million in 2020 into $330 million in 2023 [13] indicating a huge leap.
Conclusion
The huge threat posed by smishing and the escalation of mobile device users have been noticed, together with attackers utilizing different attack methods such as emotional exploitation. With data privacy and financial status together with traditional smishing detection approaches being incapable of detecting novel types of attack, the necessity to develop a sophisticated detection mechanism against phishing is at high stake.
Reference
- Mambina, I. S., Ndibwile, J. D., Uwimpuhwe, D., & Michael, K. F. (2024). Uncovering SMS spam in Swahili text using deep learning approaches. IEEE Access, 12, 25164–25175. https://doi.org/10.1109/access.2024.3365193
- Samad, S. R. A., Ganesan, P., Thangam, S., Balasubramaniyan, S., Rajiakodi, S., & Al Kaabi, A. S. R. (2024, May). SMS-Shield: A Lightweight Approach for Smishing Detection using Machine Learning. In 2024 1st International Conference on Innovative Engineering Sciences and Technological Research (ICIESTR) (pp. 1-6). IEEE.
- Mishra, S., & Soni, D. (2023). Dsmishsms-a system to detect smishing sms. Neural Computing and Applications, 35(7), 4975-4992.
- Mehmood, M. K., Arshad, H., Alawida, M., & Mehmood, A. (2024). Enhancing Smishing Detection: A Deep Learning Approach for Improved Accuracy and Reduced False Positives. IEEE Access.
- Katsarakes, E. A., Edwards, M., & Still, J. D. (2024, September). Where Do Users Look When Deciding If a Text Message is Safe or Malicious?. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting (Vol. 68, No. 1, pp. 221-225). Sage CA: Los Angeles, CA: SAGE Publications.
- Mahmud, T., Prince, M. A. H., Ali, M. H., Hossain, M. S., & Andersson, K. (2024). Enhancing Cybersecurity: Hybrid Deep Learning Approaches to Smishing Attack Detection. Systems, 12(11), 490.
- Difference Between Spam and Phishing Mail. Available online: https://www.tutorialspoint.com/difference-between-spam-andphishing-mail (accessed on 11 August 2024).
- Mishra, S.; Soni, D. Smishing Detector: A security model to detect smishing through SMS content analysis and URL behavior analysis. Future Gener. Comput. Syst. 2020, 108, 803–815. [CrossRef]
- What is Smishing (SMS Phishing)? Examples & Tactics. (2024, December 3). SentinelOne. https://www.sentinelone.com/cybersecurity-101/cybersecurity/what-is-smishing/
- Fake shipping notification emails and text messages: What you need to know this holiday season. (2024, October 22). Consumer Advice. https://consumer.ftc.gov/consumer-alerts/2023/12/fake-shipping-notification-emails-and-text-messages-what-you-need-know-holiday-season
- Kanaoka, Isohara, Beyond Mobile Devices: A Cross-Device Solution for Smishing Detection and Prevention, USENIX Symposium on Usable Privacy and Security, pp. 6–8, 2023.
- McLennan, M. The Global Risks Report 2022, 17th ed.;World Economic Forum: Cologny, Switzerland, 2022.
- Fletcher, E. (2023). IYKYK: The top text scams of 2022. Federal Trade Commission. https://www.ftc.gov/news-events/datavisualizations/data-spotlight/2023/06/iykyk-top-text-scams- 2022
- Bhatti, M. H., Khan, J., Khan, M. U. G., Iqbal, R., Aloqaily, M., Jararweh, Y., & Gupta, B. (2019). Soft computing-based EEG classification by optimal feature selection and neural networks. IEEE Transactions on Industrial Informatics, 15(10), 5747-5754.
- Srivastava, A., Gupta, B. B., Tyagi, A., Sharma, A., & Mishra, A. (2011, September). A recent survey on DDoS attacks and defense mechanisms. In International Conference on Parallel Distributed Computing Technologies and Applications (pp. 570-580). Berlin, Heidelberg: Springer Berlin Heidelberg.
- Bharath G. (2025) Real-Life Phishing Cases: Insights and Lessons for Awareness, Insights2Techinfo, pp.1
Cite As
Cajes N. (2025) The Rise of Smishing: Understanding and Preventing SMS Phishing Attack, Insights2Techinfo, pp.1