By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Phishing attacks have grown more complex, using cutting-edge tactics to trick users and get beyond established security protocols. Traditional detection and preventive techniques are frequently inadequate as these strategies change. A kind of artificial intelligence (AI) called deep learning has become a potent weapon in the battle against phishing. Deep learning algorithms can detect small trends and irregularities that are suggestive of phishing attempts by utilizing extensive datasets and deep neural networks. This paper examines the benefits, drawbacks, and prospects of deep learning in combating changing phishing techniques. We also look at case studies and real-world applications where deep learning has been effectively used to lessen phishing threats.
Introduction
Phishing is a type of cyberattack in which criminals pose as legitimate organization to get private data, including credit card numbers, usernames, and password. Phishing is still a serious threat despite decades of awareness campaigns and technological improvements[1]. The Anti-Phishing Working Group [2]claims that phishing attempts have been steadily rising as attackers contribute to improving their techniques to avoid detection.
Heuristic Based analysis and blacklisting known malicious URLs are two examples of traditional phishing detection techniques that are becoming less and less efficient against contemporary phishing techniques. These days, attackers develop incredibly tailored and convincing phishing operations by utilizing machine learning, social engineering, and dynamic content. Deep learning is a viable solution in this regard by making it possible to detect phishing efforts that are too subtle or intricate for conventional techniques to pick up on.
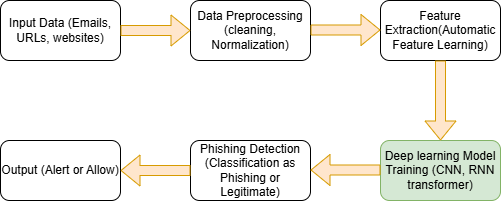
Fig : Deep Learning in Phishing Detection
The Evolution of Phishing Tactics[3]
Over time, phishing techniques have changed significantly. Phishing attempts in the past were frequently poor and simple to identify, with bad syntax and clearly fraudulent URLs. But contemporary phishing efforts are quite complex, using methods like
Spear phishing: Targeted attacks that deceive particular people or organizations by using tailored information.
Attackers use clone phishing to generate nearly exact duplicate of a genuine email, swapping malicious attachments or links for authentic ones.
Business Email Compromise (BEC): When attackers pose as executives or reliable partners, they ask for sensitive information or fraudulent transactions.
Dynamic Content: Phishing websites that alter their content to look more authentic depending on the victim’s device, location, or other variables.
AI-Generated Content: To trick victims, attackers employ AI to produce realistic text, graphics, and even audio communications.
Traditional detection techniques find it more and more challenging to stay up with these strategies. Deep learning provides a more reliable answer because of its capacity to examine enormous volumes of data and spot complex trends.
How Deep Learning Works
Deep learning is a type of machine learning that models intricate patterns in data using multi-layered neural networks. Large datasets are used to train these networks, which enables them to pick up characteristics that are frequently difficult for conventional algorithms or human analysts to pick up.
Key components of deep learning in Phishing detection[4]
Feature Extraction: From raw data, deep learning models can automatically extract important details like URLs, email content, and website structures. This removes the need for feature engineering by hand, which is frequently laborious and prone to mistakes.
Pattern Recognition: Pattern recognition in data is a strength of neural networks. This refers to identifying minute irregularities in email headers, language usage, or website layout that can point to a phishing attempt.
Adaptability: Deep learning models can adjust to changing phishing strategies because they can be updated with new data on a regular basis. This is especially crucial in an environment where attackers are always coming up with new ideas.
Types of Deep Learning models Used in phishing detection
Convolution Neural Network (CNN): By examining visual components like logos, layouts, and other design characteristics, CNNs which are frequently used for image analysis can be utilized to identify phishing websites[5].
Recurrent Neural Network (RNNs): RNNs are excellent at evaluating sequential data, such URL structures or email text. They can spot the language or URL path trends that can point to phishing[5].
Transformers : These models, which incorporate architectures such as BERT and GPT, are very good at recognizing textual context and semantics. By examining the message’s context and content, they can be utilized to identify phishing emails[5].
Advantages of Deep Learning in Phishing detection
High Accuracy: Deep learning models are frequently more accurate than conventional techniques at identifying phishing attempts.
Scalability: These models are appropriate for businesses with significant email traffic since they can process massive amounts of data in real time.
Proactive Detection: Deep learning offers a proactive defense against zero-day attacks by detecting phishing attempts that have never been seen before[6].
Reduced False Positives: Deep learning models can lower the number of false positives by learning from enormous volumes of data, preventing genuine emails from being incorrectly identified as phishing.
Challenges and limitations
Although deep learning has many benefits, there are drawbacks as well:
Data Requirements: For training, deep learning models need a lot of labeled data. Getting and classifying this data can be costly and time-consuming.
Computational Resources: Smaller businesses may find it difficult to train and implement deep learning models due to the high computational costs involved.
Adversarial Techniques: By quietly changing phishing emails or webpages, for example, attackers can trick deep learning models into incorrectly classifying them.
Interpretability: Since deep learning models are frequently seen as “black boxes,” it might be challenging to comprehend how they make their judgments. Explainability is necessary in regulated businesses, therefore this could be problematic.
Real World Applications and case studies
Case Study 1: Google’s Phishing Detection System Based on Deep Learning
Deep learning models have been used by Google to identify phishing emails in Gmail. These models can accurately detect phishing attempts by examining billions of emails. As part of its strategy, Google uses CNNs to identify dangerous attachments and RNNs to evaluate the content of emails. The quantity of phishing emails that get up in users’ inboxes has been greatly decreased by this system[7].
Case Study 2: Anti-Phishing Solutions from Microsoft
To counteract phishing, Microsoft has incorporated deep learning into Office 365 Advanced Threat Protection (ATP). By using transformers to examine email context and content, the system can identify complex phishing attempts that conventional techniques could overlook. According to Microsoft, this strategy has reduced successful phishing attacks by 90%[8].
Future Directions
Deep learning in phishing detection appears to have a bright future thanks to several new trends:
Federated Learning: Using this method, several firms can work together to build deep learning models without disclosing private information. Because it makes it possible to combine resources and expertise, this could be very helpful in the battle against phishing.
Explainable AI (XAI): To allay worries about deep learning models’ “black box” character, researchers are trying to make them easier to understand.
Integration with Other Technologies: To develop more effective anti-phishing systems, deep learning can be integrated with other technologies like blockchain and behavioral analytics.
Real-Time Adaptation: New phishing techniques might be able to be instantly adjusted by future models, offering even more proactive defense.
Conclusion
Traditional detection techniques are becoming less, and less effective as phishing strategies continue to change. A strong substitute is provided by deep learning, which makes use of its capacity to recognize intricate patterns and adjust to emerging risks. Deep learning has enormous promise to tackle phishing, even though there are still obstacles to overcome. We can build a more secure digital environment for both individuals and corporations by further improving these models and incorporating them with other technologies.
Deep learning is a vital instrument in the continuous fight against phishing; it is not only successful now but also has the potential to keep one step ahead of future attackers. Deep learning will only become more important in cybersecurity as we develop and enhance these models, giving us hope for a safer online environment.
References
- R. Tadayoni, S. Sparviero, and M. Falch, “Department of Communication Studies”.
- “APWG | Phishing Activity Trends Reports.” Accessed: Mar. 19, 2025. [Online]. Available: https://apwg.org/trendsreports/
- “View of Exploring Phishing Attacks in the AI Age: A Comprehensive Literature Review.” Accessed: Mar. 19, 2025. [Online]. Available: https://www.jcbi.org/index.php/Main/article/view/567/534
- C. Catal, G. Giray, B. Tekinerdogan, S. Kumar, and S. Shukla, “Applications of deep learning for phishing detection: a systematic literature review,” Knowl. Inf. Syst., vol. 64, no. 6, pp. 1457–1500, Jun. 2022, doi: 10.1007/s10115-022-01672-x.
- N. Q. Do, A. Selamat, H. Fujita, and O. Krejcar, “An integrated model based on deep learning classifiers and pre-trained transformer for phishing URL detection,” Future Gener. Comput. Syst., vol. 161, pp. 269–285, Dec. 2024, doi: 10.1016/j.future.2024.06.031.
- Z. Alshingiti, R. Alaqel, J. Al-Muhtadi, Q. E. U. Haq, K. Saleem, and M. H. Faheem, “A Deep Learning-Based Phishing Detection System Using CNN, LSTM, and LSTM-CNN,” Electronics, vol. 12, no. 1, Art. no. 1, Jan. 2023, doi: 10.3390/electronics12010232.
- P. Yi, Y. Guan, F. Zou, Y. Yao, W. Wang, and T. Zhu, “Web Phishing Detection Using a Deep Learning Framework,” Wirel. Commun. Mob. Comput., vol. 2018, no. 1, p. 4678746, 2018, doi: 10.1155/2018/4678746.
- U. A. Butt, R. Amin, H. Aldabbas, S. Mohan, B. Alouffi, and A. Ahmadian, “Cloud-based email phishing attack using machine and deep learning algorithm,” Complex Intell. Syst., vol. 9, no. 3, pp. 3043–3070, Jun. 2023, doi: 10.1007/s40747-022-00760-3.
- “Deep Learning-Based forensics and Anti-Forensics,” Taylor & Francis, Oct. 2024, doi: 10.1201/9781003207573-11.
- M. Moslehpour, P. R. Dwikesumasari, P. Pappachan, P.-K. Lin, N. Sakina, and M. Rahaman, “Incorporating web semantics, the technology acceptance model, and the theory of planned behavior for analyzing user intentions on dating apps,” International Journal on Semantic Web and Information Systems, vol. 20, no. 1, pp. 1–20, Oct. 2024, doi: 10.4018/ijswis.356388.
- Gaurav, A., Gupta, B. B., & Panigrahi, P. K. (2023). A comprehensive survey on machine learning approaches for malware detection in IoT-based enterprise information system. Enterprise Information Systems, 17(3), 2023764.
- Almomani, A., Alauthman, M., Shatnawi, M. T., Alweshah, M., Alrosan, A., Alomoush, W., & Gupta, B. B. (2022). Phishing website detection with semantic features based on machine learning classifiers: a comparative study. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-24.
- Cvitić, I., Peraković, D., Periša, M., & Gupta, B. (2021). Ensemble machine learning approach for classification of IoT devices in smart home. International Journal of Machine Learning and Cybernetics, 12(11), 3179-3202.
- REDDY K.T (2023) Unveiling the Power of Naive Bayes in Phishing Detection, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) The Role of Deep Learning in Combating Evolving Phishing tactics, Insights2techinfo pp.1