By: KUKUTLA TEJONATH REDDY, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, tejonath45@gmail.com
Abstract
Phishing is a common social engineering attack where the attacker creates a replica of a web page to tick the users and gather there personal, financial data [1]. From the first few decades of the cyber age phishing attack is a major threat till today. Day by day phishing attacks has been evolved and the attacker became more creative in their attack. This article is based on various techniques in phishing and some of the preventions to safeguard against these phishing attacks.
Introduction
Now a days in the world technology play a crucial role in our daily lives the threat of phishing attacks is getting greater than ever. Phishing is a form of cybercrime that continuously will develop and making organizations and individuals to stay lookout. This article aims to let you know about Phishing and the various techniques that used by cybercriminals and how to prevent yourself against these attacks
What is Phishing?
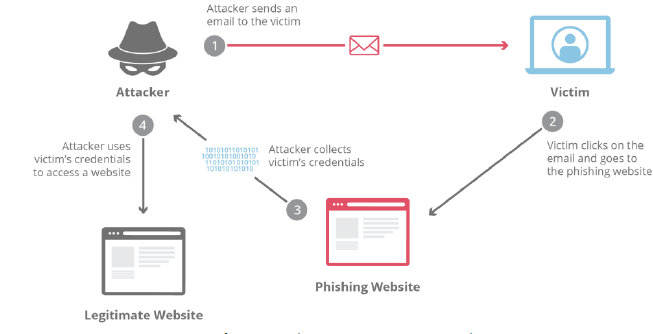
Phishing is one of the cyberattack. In this attack that tricking on individuals to obtain their sensitive information, such as login credentials, personal details, card details, etc..,. Phishing is like tricking on individuals by pretending to a trustworthy person or agencies just like fishermen use bait to catch fish. In phishing they use the fake message or fake websites to steal important information from people.
Common Phishing techniques:
- Email Phishing: Email Phishing is one of the most common form of phishing. Email Phishing involves sending fraud email that just look like trustworthy sources for example: banks, social media platforms and government agencies. These mails usually have urgent messages or attractive offers to make the people click on malicious link or download harmful attachments.[5,6]
- Spear Phishing: In spear phishing, cybercriminals will select specific target like individual person or organizations. They will do research on the target in order to make the attack more personalized. They will gather all the information from various sources like social media and they will create a convincing email by that target may not able to determine the fraudulent nature of the message[7,8].
- Clone Phishing: In clone phishing cybercriminals will duplicate copy of email or website and changes little part of that website or email to trick people. They will send the fake message to the target which will just looks like real one but it has malicious links [9-11].
- Pharming: In Pharming attack cybercriminals will compromise the DNS settings of a website so when the target try to open the real site it will automatically redirects to fraud website without their knowledge. The target might think he is work on real site but he is working on fraud website.
- Whaling Phishing: Whaling Phishing is a common type cyber attack where the cybercriminals will target high-profile individuals, like top executives or board persons of the organization. They will use different fraud techniques to tick these individuals to get their sensitive information or performing actions that can harm their organization or themselves. It’s just like phishing but the target is high-profile person so he is a “whale” in the organization, so it is called “whaling”.
- Smishing and vishing: phishing is not only permitted for mails. Phishing can also may done by text messages or phone calls. In smishing victim will receive a text message with a malicious link, and in vishing victim will get a phone call from the cybercriminals will act like trustworthy organization or an institution, and seeking our sensitive information.
Prevention Against Phishing attack
- Verify Senders: Conform the sender identity before responding or opening any link in the email or messages. Check email addresses and verify the sender information.
- Educate Yourself: Learn about common phishing techniques and be aware of latest cyber frauds. Training and awareness will help you to recognize the phishing attack easily.
- Install Security Software’s: Use high recommended antivirus and anti-malware software that can detect and block the phishing attack.
- Enable Two-Factor Authentication(2FA): Activate the 2 Factor authentication for your online accounts like social media, banking applications. This adds an extra layer of security which sends a security code to your phone.
- Use Email Filters: Activate the spam filters and email validation tools to decrease the chances of phishing emails to reach your inbox.
- Protect Personal information: Be careful about sharing your personal and financial details on online or on phone call. Only provide such details if the website secure only.
- Report Suspicious Emails: If you receive any malicious phishing emails report it to your email provider. This will help to prevent others from falling into trap which is created by cybercriminals
Conclusion
Phishing attacks are done by the cybercriminals to obtain sensitive information like financial details, login details, and other personal information form the people. These attacks are usually happened through emails, text message and phone calls by using any trustworthy agenesis. Cybercriminal’s goal is to trick the victim and get their confidential information or downloading malware into victim device. To prevent yourself from these attacks it’s important to be alert and informed. We can educate our friends about verifying senders, enabling two factor authentication, email filters …etc. By that we can reduce the Phishing attacks and safeguard our personal and financial data.
References
- J. Chen and C. Guo, “Online Detection and Prevention of Phishing Attacks,” 2006 First International Conference on Communications and Networking in China, Beijing, China, 2006, pp. 1-7.
- Bhavsar, Vaishnavi & Kadlak, Aditya & Sharma, Shabnam. (2018). Study on Phishing Attacks. International Journal of Computer Applications. .
- Chiew, Kang Leng & Yong, Kelvin & Tan, Colin Choon Lin. (2018). A Survey of Phishing Attacks: Their Types, Vectors and Technical Approaches. Expert Systems with Applications. 106. .
- Banu, Dr. M. Nazreen and S. Munawara Banu. “A Comprehensive Study of Phishing Attacks.” (2013).
- Alabdan R. Phishing Attacks Survey: Types, Vectors, and Technical Approaches. Future Internet. 2020; 12(10):168.
- Almomani, A., Gupta, B. B., Wan, T. C., Altaher, A., & Manickam, S. (2013). Phishing dynamic evolving neural fuzzy framework for online detection zero-day phishing email. arXiv preprint arXiv:1302.0629.
- Gupta, B. B., Yadav, K., Razzak, I., Psannis, K., Castiglione, A., & Chang, X. (2021). A novel approach for phishing URLs detection using lexical based machine learning in a real-time environment. Computer Communications, 175, 47-57.
- Almomani, A., Alauthman, M., Shatnawi, M. T., Alweshah, M., Alrosan, A., Alomoush, W., & Gupta, B. B. (2022). Phishing Website Detection With Semantic Features Based on Machine Learning Classifiers: A Comparative Study. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-24.
- Jain, A. K., Gupta, B. B., Kaur, K., Bhutani, P., Alhalabi, W., & Almomani, A. (2022). A content and URL analysis‐based efficient approach to detect smishing SMS in intelligent systems. International Journal of Intelligent Systems, 37(12), 11117-11141.
- Gupta, B. B., & Sheng, Q. Z. (Eds.). (2019). Machine learning for computer and cyber security: principle, algorithms, and practices. CRC Press.
- Gupta, B. B., Perez, G. M., Agrawal, D. P., & Gupta, D. (2020). Handbook of computer networks and cyber security. Springer, 10, 978-3.
Cite As
REDDY K.T (2023) Understanding and Preventing Phishing Attacks, Insights2Techinfo, pp.1