By: Aiyaan Hasan, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, rayhasan114@gmail.com
Abstract:
DDoS (Distributed Denial of Service) attacks pose a significant threat to the digital realm, as they aim to disrupt networks, websites, along with their services. We categorize DDoS attacks into amplification, network-centric, application layer, and protocol attacks, each requiring specific defence strategies. This article dives into the exploration of the DDoS attacks, their various forms, and the current evolving scenario in the world when it comes to mitigation of these DDoS attacks. Analysing a DDoS attack involves identifying and recognizing attack patterns, monitoring traffic, implementing security measures, and understanding the impact. Effective defence mechanisms are important to protect against these evolving threats in our interconnected online world. It is crucial as the digital realm evolves and expands, addressing these evolving DDoS attacks in order to protect and protect the online infrastructures in order to ensure connectivity for the users and safety.
Introduction:
We currently are living in a world where our lives are intertwined with the Internet in almost every aspect. Regardless there exists a menace that can affect our online existence and efficiency. It’s known as the DDoS (Distributed Denial of Service) [8]-[12]. A Cyber Threat that has the ability to ruin the functioning of websites, organizations and entire networks.
A DDoS attack is basically an unauthorized attempt to affect the regular functioning of a network, website or an organization in malicious ways by flooding it with traffic from countless resources.
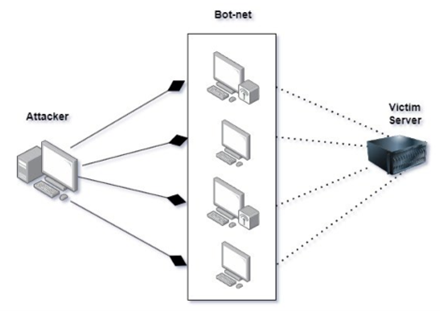
Figure 1. Shows a simple way of depicting a DDoS attack, and how it is carried out with the help of botnets on the targeted server.
DDoS attacks are quite complex when it comes to detecting them, currently existing tools enable us to identify these attacks, these tools are basically generating alerts. As most of the existing solutions for the DDoS attack mitigation involves the usage of datasets and the utilization of simulated scenarios their applicability may not be up to the mark due to lapses made in the assumptions while designing [1]. DDoS detection can be done in many different ways, but the new and complex attack types, however are making the “Conventional ones” obsolete [2]. In a DDoS attack one of the most important components is a botnet, these botnets are basically compromised systems which are in control of the attackers and therefore can be used to deploy huge amounts of traffic to cause harm to the target networks and servers. Botnets posse as a significant threat when it comes to cyber-security as they act as a platform for cybercrimes for purposes like theft of personal data, spam email sending and much more [3].
Types of DDoS attacks
- Amplification Attacks: The attackers start off by sending requests to servers that are vulnerable or to servers that respond in much larger responses. [4]
- Network-centric or volumetric attacks: This particular attack focuses on the target’s network infrastructure, such as switches, routers network links, rather than targeting any specific service that might be running on the servers. These attacks primarily focus on network connectivity which makes the network inaccessible. [5]
- Application layer: These attacks are often referred to as Layer 7 DDoS attacks, targeting the application layer specifically. It focuses on the vulnerabilities in the way applications or services handle genuine requests.
- Protocol attacks: These are the inefficiencies present in network protocols to enable disruption of the targeted service. These attacks focus on overloading the existing resources of the network devices by deploying large volumes of protocol-specific packets.
Components of DDoS attacks
The Key components of Distributed Denial of Service (DDoS) attack involves elements which aids in the execution and mitigation of such attacks.
- Attackers: These are the individuals, groups or organization responsible for the DDoS attacks. These attackers may have varying motivations.
- Botnets: These are a network of computers which are infected and controlled as a group without the owner possessing any knowledge about these undercover activities.
- Victim (Target): The primary target of the DDoS attack.
- Attack Traffic: The traffic that has been generated by the vulnerable devices in the botnet, Attack traffic is directed towards the server of the victim with the intent of disruption.
Analysing a Distributed Denial of Service (DDoS) attack involves understanding the characteristics of it, identifying/recognizing the attack traffic, and implementing strategies in order to mitigate its impact. [6]
Analysis of DDoS
Attack Type Identification:
- Traffic Pattern analysis: Analysing the network traffic in order to identify patterns which are consistent with DDoS attacks. Particularly looking for unusually high volumes of incoming traffic or specific patterns which are common to DDoS attacks.
- Log and Alert Monitoring: Monitoring server and network logs for any signs of abnormal behaviour such as a sudden increase in connection requests, traffic spikes or any unusual error message.
2. Attack Traffic Profiling:
- Traffic Source Analysis: Identifying the sources of the traffic, via the examination of the IP addresses. In majority of the DDoS attacks the traffic usually originates from compromised devise also called Botnets.
- Traffic Type Analysis: Involves determining the type of traffic used in the attack and which particular protocol is being targeted.
3. Attack Mitigation:
- Traffic Filtering: It is necessary to introduce the traffic filtering at any network boundaries to keep a check on malicious traffic. Using access control lists (ACLs) to filter out packets from recognized attack sources.
- Rate Limiting: Applying rate limiting to control the flow of incoming traffic, which ensures that it stays within a manageable range.
- Content Delivery Networks (CDNs): In order to reduce the loads on server, utilize CDNs to distribute and absorb traffic.
- Anomaly detection: Implementation of anomaly detection systems in order to identify any incoming unusual traffic.
4. Packet Analysis:
- Packet Capture and Inspection: Using packet capture and network analysers to identify and inspect any malicious packets. This helps in understanding the attack patterns and payload contents.
- Signature Analysis: Identifying patterns or signatures in the traffic which can be used to create custom filters for blocking the attack.
5. Impact Assessment:
- Service availability: Assessing the impact of the DDoS attack on the availability of the services which were targeted by the attackers
- Resource utilization: Monitoring the utilization of the network and the server resources which includes bandwidth, CPU, memory etc during attack
6. Attack Source Tracing:
- Source IP Tracking: Attempt to trace the source IP addresses of the attack traffic.
7. Documentation:
- Report: Documentation and reporting the details of the DDoS attack, which includes the duration, attack type, the impact of the attack. This documentation can be valuable for post-attack analysis and reporting [7].
Challenges to detect DDoS attack
Detecting DDoS attacks poses significant challenges due to the evolving nature of these attacks and the use of various techniques to bypass detection mechanisms. One of the most challenging types of DDoS attacks to detect is application layer DDoS attacks, which utilize legitimate client connections to overwhelm web servers [13]. Traditional rule-based detection methods are ineffective against these attacks, as they cannot accurately identify genuine network traffic [15].
To address these challenges, researchers have proposed various detection techniques. One approach is the use of data mining algorithms, such as correlation-based methods and machine learning algorithms like decision trees, to detect DDoS attacks [14][16]. These methods analyze network traffic patterns and identify anomalies that indicate the presence of an attack. Another approach is the use of anomaly-based intrusion detection systems (IDS), which rely on statistical analysis and machine learning to detect and prevent new DDoS attacks [15][17]. These IDS systems can detect and mitigate even stealthy DDoS attacks with low attack sizes per source [17].
Furthermore, hybrid detection frameworks have been proposed to improve the accuracy of DDoS detection. These frameworks combine multiple detection methods, such as rate limiting at the intermediate network and accurate attack traffic detection at the victim end, to enhance the overall effectiveness of DDoS detection and mitigation [18]. Additionally, the use of matching pursuit algorithms has shown promise in detecting TCP SYN flood attacks, a common type of DDoS attack [19]. These algorithms generate dictionaries from normal and attack traffic and use residual analysis to produce alarms for attack detection.Overall, detecting DDoS attacks is a complex task due to the sophisticated techniques employed by attackers. However, researchers have made significant progress in developing detection methods that utilize data mining, anomaly-based IDS, and hybrid frameworks to accurately identify and mitigate DDoS attacks. These approaches leverage statistical analysis, machine learning, and traffic pattern analysis to detect anomalies and distinguish between legitimate and malicious network traffic.
Conclusion
DDoS attacks can vary widely in terms of scale, complexities and impact. Effective analysis and response require a combination of real-time monitoring, traffic inspection, and crucial security measures to mitigate the attack and minimize its impact on network services. It’s also essential to stay updated on emerging DDoS attack trends and techniques to enhance defence mechanisms. DDoS attack is an issue and a challenge that is ongoing, which requires innovation to mitigate. As the internet keeps on growing along with the services provided online, understanding DDoS attack becomes really crucial to maintain and ensure the availability and reliability of the internet along with the safety of servers to avoid any attacks as such. As the cyber threats rise, so should our defence to ensure the safety as it is of paramount importance.
References
- Physical Assessment of an SDN-Based Security Framework for DDoS Attack Mitigation: Introducing the SDN-SlowRate-DDoS Dataset. (n.d.). Physical Assessment of an SDN-Based Security Framework for DDoS Attack Mitigation: Introducing the SDN-SlowRate-DDoS Dataset | IEEE Journals & Magazine | IEEE Xplore.
- Investigation on Efficient Machine Learning Algorithm for DDoS Attack Detection. (n.d.). Investigation on Efficient Machine Learning Algorithm for DDoS Attack Detection | IEEE Conference Publication | IEEE Xplore.
- Sonawane, S. (2018, July 30). A Survey of Botnet and Botnet Detection Methods – IJERT. A Survey of Botnet and Botnet Detection Methods – IJERT.
- Guo, R., & Wang, D. (2014, February 1). Distributed Denial-of-Service Attack Packet Filtering and Control Mechanisms. Sensor Letters, 12(2), 358–363.
- Verma, V., & Kumar, V. (2021). DOS/DDOS Attack Detection using Machine Learning: A Review. SSRN Electronic Journal.
- P. Narode, M. P., & Shaikh, P. I. (2018, January 10). Review on EM-CURE Algorithm for Detection DDOS Attack. International Journal of Engineering and Computer Science, 7(01), 23386–23489.
- An, X., Su, J., Lü, X., & Lin, F. (2018, October 22). Hypergraph clustering model-based association analysis of DDOS attacks in fog computing intrusion detection system. EURASIP Journal on Wireless Communications and Networking, 2018(1).
- Tripathi, S., Gupta, B., Almomani, A., Mishra, A., & Veluru, S. (2013). Hadoop based defense solution to handle distributed denial of service (ddos) attacks.
- Gupta, B. B., Joshi, R. C., & Misra, M. (2012). ANN based scheme to predict number of zombies in a DDoS attack. Int. J. Netw. Secur., 14(2), 61-70.
- Cvitić, I., Perakovic, D., Gupta, B. B., & Choo, K. K. R. (2021). Boosting-based DDoS detection in internet of things systems. IEEE Internet of Things Journal, 9(3), 2109-2123.
- Singh, A., & Gupta, B. B. (2022). Distributed Denial-of-Service (DDoS) Attacks and Defense Mechanisms in Various Web-Enabled Computing Platforms: Issues, Challenges, and Future Research Directions. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-43.
- Mishra, A., Gupta, N., & Gupta, B. B. (2021). Defense mechanisms against DDoS attack based on entropy in SDN-cloud using POX controller. Telecommunication systems, 77(1), 47-62.
- S. Zeebaree, K. Sharif, & R. Amin, “Application layer distributed denial of service attacks defense techniques : a review“, Academic Journal of Nawroz University, vol. 7, no. 4, p. 113, 2018. https://doi.org/10.25007/ajnu.v7n4a279
- D. Ayyamuthukumar and S. Karthik, “Correlation based approach with a sliding window model to detect and mitigate ddos attacks“, Journal of Computer Science, vol. 11, no. 2, p. 438-442, 2015. https://doi.org/10.3844/jcssp.2015.438.442
- W. Bhaya and M. Manaa, “Review clustering mechanisms of distributed denial of service attacks“, Journal of Computer Science, vol. 10, no. 10, p. 2037-2046, 2014.
- M. Alyas, M. Noor, & H. Hassan, “Ddos attack detection strategies in cloud a comparative stud“, Vfast Transactions on Software Engineering, p. 35-42, 2017.
- K. Doshi, Y. Yilmaz, & S. Uludag, “Timely detection and mitigation of stealthy ddos attacks via iot networks“, International Research Journal of Modernization in Engineering Technology and Science, 2022.
- “Detection and prevention algorithm of ddos attack over the iot networks“, Tem Journal, p. 899-906, 2020.
- D. Erhan, E. Anarim, & G. Kurt, “Ddos attack detection using matching pursuit algorithm“, 2016 24th Signal Processing and Communication Application Conference (SIU), 2016.
- Gupta, B. B., & Sheng, Q. Z. (Eds.). (2019). Machine learning for computer and cyber security: principle, algorithms, and practices. CRC Press.
- Gupta, B. B., Perez, G. M., Agrawal, D. P., & Gupta, D. (2020). Handbook of computer networks and cyber security. Springer, 10, 978-3.
- Mishra, A., Gupta, N., & Gupta, B. B. (2023). Defensive mechanism against DDoS attack based on feature selection and multi-classifier algorithms. Telecommunication Systems, 82(2), 229-244.
Cite As
Hasan A. (2023) Understanding Distributed Denial of Service (DDoS) Attacks and its analysis, Insights2Techinfo, pp.1