By: Pinaki Sahu, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, 0000pinaki1234.kv@gmail.com
Abstract
The article explores the important topic of reverse social engineering attacks against financial institutions, a complex and dynamic cybersecurity threat. Through the manipulation of individuals within organizations, reverse social engineering takes advantage of trust dynamics to compromise security mechanisms. Attackers use strategies including baiting, phishing, pretexting, and impersonation to get unauthorized access to private data. Financial institutions may experience losses in value, harm to their reputation, and regulatory repercussions. In order to successfully manage and reduce the effects of reverse social engineering assaults on the financial industry, the paper highlights the significance of staff training, sophisticated threat detection systems, and well-defined incident response strategies.
Introduction
Financial institutions have to deal with a clever but harmful enemy in the ever-changing field of cybersecurity: reverse social engineering. This approach, in contrast to traditional tactics, makes use of human weaknesses and trust dynamics to influence individuals within organizations to willingly violate security systems. The subtleties of reverse social engineering are examined in this article, along with its misleading tactics and possible repercussions for financial institutions. Our focus as we explore this complex cyber threat is to provide experts with knowledge that is essential for strengthening defences at a time when connectivity and trust are both advantages and disadvantages. Financial institutions need to be aware of the nuances of reverse social engineering in order to protect sensitive data from ever-changing online threats.
Reverse Social Engineering Definition
Reverse social engineering is a clever escape from traditional social engineering techniques. It is a tactic used by attackers to induce employees of an organization to voluntarily violate security procedures rather than the attacker attacking first. This type of assault preys on human weaknesses by obtaining unauthorized access to private data and by playing on social dynamics and trust1[1].
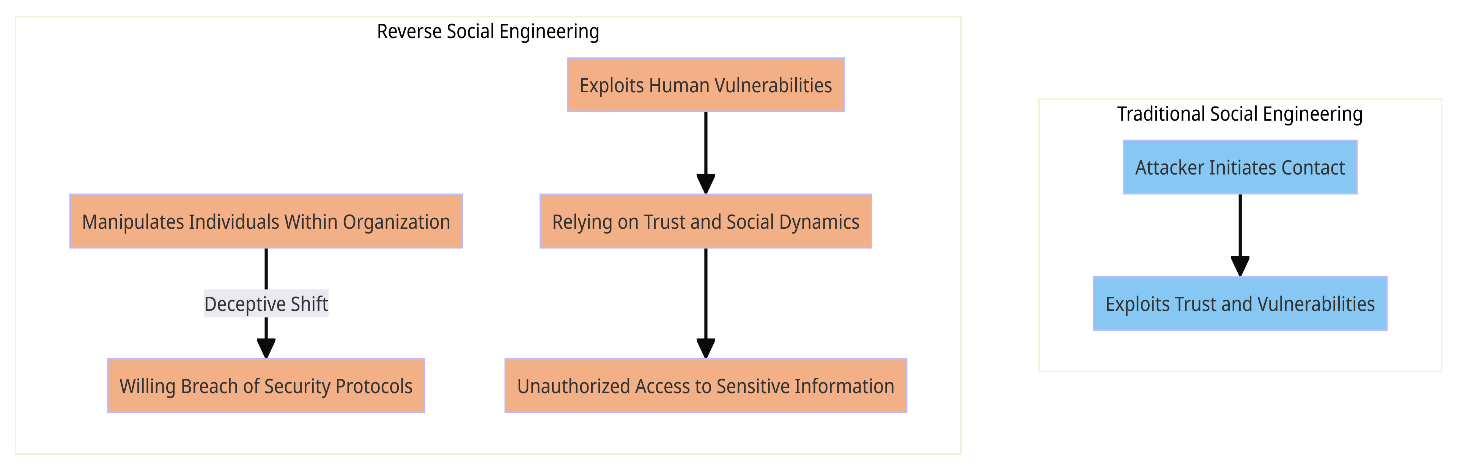
Methods Involved in Attacks Using Reverse Social Engineering
- Impersonation of Trusted Entities: Cybercriminals frequently take advantage of the faith that staff members have in their managers or law enforcement. The attacker pretends to be a trusted colleague or senior executive in an attempt to pressure others into disclosing private information[2].
- Phishing and spear phishing attacks: These are the two techniques where harmful links or prompts are included in emails and communications that are designed to look authentic. To increase their chances of success, spear phishing attackers personalize their messages to certain employees of the financial institution[2].
- Pretexting: By fabricating scenarios, attackers control staff members by establishing a pretext that prompts a reaction, including divulging private information or taking steps that compromise security[3].
- Baiting: Attackers use human curiosity to their advantage by purposefully hiding bait such as USB devices or innocent-looking files in accessible places. Curiosity may lead workers to engage with these components accidentally compromising security[3].
Effects on Finance Institutions
- Financial Losses: Institutions may sustain significant financial losses as a result of successful reverse social engineering attacks. Attackers can access money, tamper with transactions, or start sending money without authorization[4].
- Reputational Damage: Stakeholders and clients must have trust in financial institutions. This trust may be violated by a successful reverse social engineering attack, resulting in reputational harm that might take years to heal.
- Regulatory Repercussions: Strict rules regulating the security of private data apply to financial organizations. Reverse social engineering breaches may give rise to serious legal and regulatory implications.
Addressing the Threats
- Employee Education: It is important to teach staff members about the strategies used in reverse social engineering. Regular training sessions may increase worker awareness and provide them with the tools they need to identify and report such risks[4].
- Advanced Threat Detection Systems: Implementing strong threat detection systems in place allows you to identify questionable activity instantly. These tools can examine communication patterns and spot irregularities that can point to a reverse social engineering scam[4].
- IDPS(Intrusion detection and Prevention System) for monitoring network and system activities for malicious behaviour.
- User Behavior Analytics (UBA) tools for analysing user behaviour to detect deviations from normal patterns. Unusual interactions or access attempts can trigger alerts, potentially indicating a reverse social engineering attempt.
- Chatbot assistance with NLP features to keep an eye on communication channels and quickly identify abnormalities or possible social engineering efforts in real time[5].
- Incident Response Plans: Having clear plans for handling incidents guarantees a prompt and efficient response to any threats that are discovered. This involves dividing the affected systems, reducing the effects, and doing retrospective evaluation for ongoing improvement.
Conclusion
A proactive and comprehensive strategy is needed to protect financial institutions from the growing threat of reverse social engineering. The first line of defence is employee education, which raises awareness and gives employees the authority to identify and report any hazards. In addition, modern threat detection systems, which include UBA tools, chatbots with natural language processing capabilities, and IDPS, are essential for anomaly detection and real-time monitoring. Plans for incident response guarantee a prompt and effective response to mitigate the effects of threats that have been detected. Financial institutions need to adopt dynamic strategies that combine technical solutions and human intelligence in order to keep up with evolving cyber attackers. In an ever-evolving digital ecosystem, this cooperation not only strengthens present defences but also predicts and reduces potential cyber threats, protecting the integrity and confidence of clients and stakeholders.
References
- Irani, D., Balduzzi, M., Balzarotti, D., Kirda, E., & Pu, C. (2011). Reverse social engineering attacks in online social networks. In Detection of Intrusions and Malware, and Vulnerability Assessment: 8th International Conference; DIMVA 2011, Amsterdam, The Netherlands, July 7-8, 2011. Proceedings 8 (pp. 55-74). Springer Berlin Heidelberg.
- Salahdine, F., & Kaabouch, N. (2019). Social engineering attacks: A survey. Future internet, 11(4), 89.
- Kilavo, H., J. Mselle, L., I. Rais, R., & Mrutu, S. I. (2023). Reverse Social Engineering to Counter Social Engineering in Mobile Money Theft: A Tanzanian Context. Journal of Applied Security Research, 18(3), 546-558.
- Shughart II, W. F., & Smith, J. T. (2020). The broken bridge of public finance: majority rule, earmarked taxes and social engineering. Public Choice, 183, 315-338.
- Sahu, P. Natural Language Processing Chatbots Assistance for Strengthening Cybersecurity in Messaging Applications.
- Gupta, B. B., Gaurav, A., & Panigrahi, P. K. (2023). Analysis of the development of sustainable entrepreneurship practices through knowledge and smart innovative based education system. International Entrepreneurship and Management Journal, 19(2), 923-940.
- Chui, K. T., Gupta, B. B., Jhaveri, R. H., Chi, H. R., Arya, V., Almomani, A., & Nauman, A. (2023). Multiround transfer learning and modified generative adversarial network for lung cancer detection. International Journal of Intelligent Systems, 2023, 1-14.
- Ahvanooey, M. T., Zhu, M. X., Li, Q., Mazurczyk, W., Choo, K. K. R., Gupta, B. B., & Conti, M. (2021). Modern authentication schemes in smartphones and IoT devices: An empirical survey. IEEE Internet of Things Journal, 9(10), 7639-7663.
- Chui, K. T., Gupta, B. B., Jhaveri, R. H., Chi, H. R., Arya, V., Almomani, A., & Nauman, A. (2023). Multiround transfer learning and modified generative adversarial network for lung cancer detection. International Journal of Intelligent Systems, 2023, 1-14.
Cite As
Sahu P. (2023) Understanding Reverse Social Engineering Attacks on Financial Institutions, Insights2Techinfo, pp.1