By: KUKUTLA TEJONATH REDDY, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, tejonath45@gmail.com
Abstract:
A pervasive threat in the digital landscape, phishing attacks continue to evolve to bypass security measures and fool unsuspecting users. This article examines the sophisticated “blacklist technique” used by cybercriminals in phishing campaigns. This approach requires careful research to identify the most widely used security solutions, and allows for the customization of phishing scenarios specifically designed to circumvent these tools This article explores complex techniques if are taken through the blacklist methods, and reveals its nuances, implementation mechanisms and its deep impact on cybersecurity real -Based on examples and situations from around the world, the article emphasizes the critical importance of understanding this method under for individual and institutional emphasis. Through comprehensive approaches, this article aims to raise awareness and empower readers to identify and combat the dangers posed by blacklist strategies in phishing attacks.
Introduction:
In today’s digital age, where the internet plays an important role in our daily lives, cybersecurity is crucial. Phishing attacks is one of the most common and deceptive cyber threats, continue to target unsuspecting users. cybercriminals will use a various technique to trick individuals to get sensitive information, which resulting in financial losses and security breaches. Among these techniques, the blacklist technique stands out as an effective tactic used by cybercriminals. This article takes a deeper look at the blacklist approach, shedding light on its complexity, applications, and cybersecurity implications.
Understanding Phishing and Its Significance:
Phishing is a type of cyber-attack where attackers pose with trustworthy identities to trick individuals to get sensitive data like passwords, and credit card numbers. Because phishing attack is so dangerous for individuals, companies and organizations, it is important to understand how hackers will get successful and take advantage of them.
The Blacklist Technique in Phishing:
The blacklist technique is a sophisticated method which is used by hackers to bypass security measures and deliver malicious content to unsuspecting users. Unlike traditional phishing attacks that target broad audience, the blacklist technique will gather security tools, antivirus software and email filters commonly will use by potential victims and then attackers will create phishing content specifically designed to evade these security solutions to the intended targets Successful delivery is ensured.
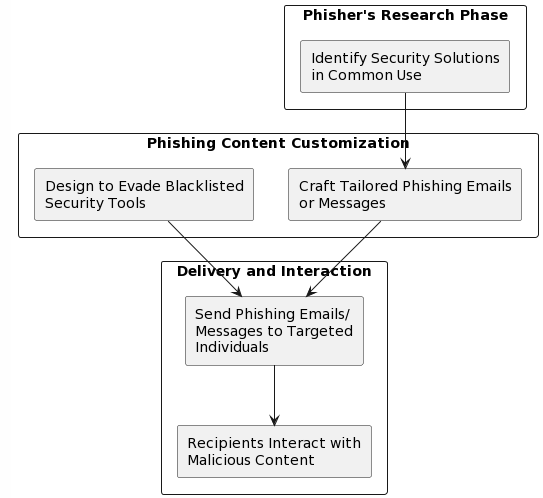
Blacklist strategies to be implemented:
Analysis and collection: Cybercriminals will conduct extensive research to identify widely used security tools, firewalls and email filters used by individual persons and organizations.
Customized phishing texts: Hackers will create customized phishing emails or text messages which contains malicious links or attachments in that which will bypass specific security measures.
Evasion and Delivery: By circumventing the blacklisted security tools, phishing message will reach targeted persons, who are more likely to interact with malicious content and unknowingly compromising their data.
Impact on Cybersecurity:
Blacklist technique will pose significant risk to cybersecurity for several reasons:
Increased Success Rate: By circumventing widely implemented security measures, phishing attacker will use blacklisting techniques for more likely to succeed, which resulting in more successful data breaches.
Targeted Attacks: Cybercriminals will target specific individuals or organizations to match their attack efforts, which makes attacks more accurate and harder to detect.
Reputation Damage: Phishing attacks will damage reputations of a popular businesses and organizations, which causes clients and customers lose their trust.
Mitigating the risks Associated with the Blacklist technique:
User Education: Educating the users about phishing techniques and about blacklisting techniques, which helps to them identifying suspicious emails or messages and avoid being with potential targets evil will communicate.
Multi-layered security: We need to use multi-layered security solutions like advanced threat detections, email filters, and firewalls with that solutions we can enhance the overall level of security and reduce the impact of blacklist-based phishing attacks.
Conclusion:
Blacklist techniques in phishing represents sophisticated and targeted approach for cybercriminals to compromise security systems and deceive user. Understanding the complexity of this process is important for individuals, businesses and organizations to strengthen their cybersecurity defences. By combining user education, awareness and advanced security solutions. We can mitigate these risks associated with blacklisting methods and ensure a secure digital environment for everyone. Stay vigilant, stay informed then we can combat phishing threats.
References:
- Nadar, V. K., Patel, B., Devmane, V., & Bhave, U. (2021, October). Detection of Phishing Websites Using Machine Learning Approach. In 2021 2nd Global Conference for Advancement in Technology (GCAT) (pp. 1-8). IEEE.
- Shankar, S. (2018). Review of various methods for phishing detection. EAI Endorsed Transactions on Energy Web and Information Technologies, 5(20).
- Nadar, V. K., Patel, B., Devmane, V., & Bhave, U. (2021, October). Detection of Phishing Websites Using Machine Learning Approach. In 2021 2nd Global Conference for Advancement in Technology (GCAT) (pp. 1-8). IEEE.
- Sharifi, M., & Siadati, S. H. (2008, March). A phishing sites blacklist generator. In 2008 IEEE/ACS international conference on computer systems and applications (pp. 840-843). IEEE.
- Oest, A., Safaei, Y., Doupé, A., Ahn, G. J., Wardman, B., & Tyers, K. (2019, May). Phishfarm: A scalable framework for measuring the effectiveness of evasion techniques against browser phishing blacklists. In 2019 IEEE Symposium on Security and Privacy (SP) (pp. 1344-1361). IEEE.
- Prakash, P., Kumar, M., Kompella, R. R., & Gupta, M. (2010, March). Phishnet: predictive blacklisting to detect phishing attacks. In 2010 Proceedings IEEE INFOCOM (pp. 1-5). IEEE.
- Wang, L., Li, L., Li, J., Li, J., Gupta, B. B., & Liu, X. (2018). Compressive sensing of medical images with confidentially homomorphic aggregations. IEEE Internet of Things Journal, 6(2), 1402-1409.
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). InFeMo: flexible big data management through a federated cloud system. ACM Transactions on Internet Technology (TOIT), 22(2), 1-22.
- Gupta, B. B., Perez, G. M., Agrawal, D. P., & Gupta, D. (2020). Handbook of computer networks and cyber security. Springer, 10, 978-3.
- Bhushan, K., & Gupta, B. B. (2017). Security challenges in cloud computing: state-of-art. International Journal of Big Data Intelligence, 4(2), 81-107.
Cite As
REDDY K.T (2024) Understanding the Blacklist Technique in Modern Phishing, Insights2Techinfo, pp.1