By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Cyber threats are changing at a historic speed in the digital era because criminals use technology to exploit both people and organizations. The modern criminal technique known as Digital Arrest unites psychological manipulation with social engineering techniques along with technological means to exert control over victims. Research analyzes Digital Arrest as a criminal concept with its operational methods and actual cases while providing security measures to fight the emerging threat. Awareness of this digital danger enables both people and organizations to enhance their security posture in present-day connected environments.
Introduction
Modern technological progress provides massive conveniences to people yet creates new types of cyber-based criminal activities. The dangerous threat that has recently appeared is the method known as “Digital Arrest.” The method behind Digital Arrest differs completely from standard cyberattacks by employing psychological tactics to control victims while garnishing their helplessness and sense of entrapment[1]. The article investigates Digital Arrest methodology together with prevention methods aimed at controlling this threat.
What is Digital Arrest?
Cyber extortion using Digital Arrest requires attackers to utilize technology together with psychological intimidation strategies against their victims. Digital Arrest functions through metaphor since detention of the victim is purely figurative. The schemers construct various lies about digital surveillance to fool their victims by employing threats with fake legal authority combined with compromised devices and tampered evidence. The criminals use their victim’s panic and disorientation to force the extraction of financial payments and confidential data[2].
A victim experiences a harassment incident when someone contacts them via phone or text to warn that their device has been compromised which demands payment to avoid releasing their confidential information. Accidents often gain remote control of devices before delivering a substantive law enforcement warning notice to create panic in their victims.
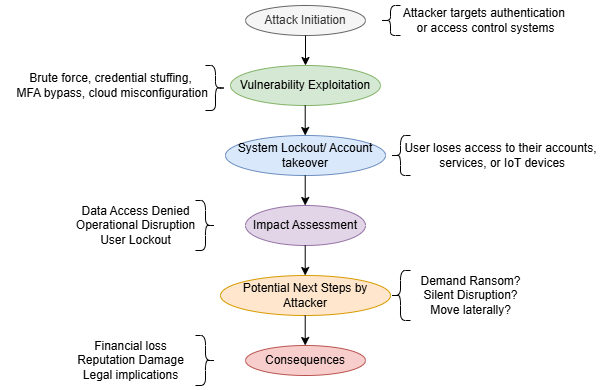
Fig : Digital Arrest Attack Process
How Does Digital Arrest Work[3]
A Digital Arrest attack follows a pattern which includes social engineering tactics together with malware distribution as well as psychological manipulation techniques.
1. Initial Contact: Armed attackers pretend to be either government officials or technological support personnel or law enforcement authorities for their attacks. Victims receive contact from criminals either through their phones or emails or messaging applications who pretend that the victims’ digital accounts and devices now show signs of compromise.
2. Creating Fear: The criminal elements employ pressure tactics by putting victims at risk through threats directed at their privacy protections. The attackers present false documentation which includes altered screenshots and fabricated legal documents in order to demonstrate their credibility to the victim.
3. Gaining Control: The attackers manage to obtain distant control of their victims’ devices by deploying harmful software. The attackers activate contingencies on the device that either screen-lock the system or show threatening messages to generate distress in the victim.
4. Extortion: The victim reaches a state of adequate intimidation which allows attackers to collect payments through cryptocurrency as a solution for their fake issue. Cyber attackers require victims to reveal personal details such as their banking information and password code secrets.
5. Continued Manipulation : Victims who manage to make their first payment can remain at risk because the attackers might launch further harassment attempts to obtain bigger payments or additional requested information.
Real-Life Examples of Digital Arrest[4]
Digital Arrest serves as a practical criminal tool which law enforcement authorities have implemented against offenders. For instance:
The police impersonator who contacted an Indian woman through phone appeared in 2022 to induce her into paying money to avoid arrest. A stranger phoned the woman to charge her with unlawful deeds before requesting funds to stay out of jail. The victim transferred a vast amount of money to scammers before understanding that the money request was the result of a scam.
A computer user based in the United States saw an FBI claiming his system was under their control through unlawful activities. A pop-up on the device ordered Bitcoin payment to receive access back.
These scenarios demonstrate how Digital Arrest manifests psychologically and prove the necessity of raising public understanding of such risks.
How to Protect Yourself from Digital Arrest [5]
To prevent Digital Arrest, you must adopt three essential components including caution measures and educational training along with technological protection systems. Protection against Digital Arrest requires you to follow these steps:
1. Take all unsolicited contacts from people who claim to represent law enforcement or tech support seriously. Check their identity through official channels as a necessary first step before taking any action.
2. Protect your system by refraining from clicking on uncertain links and downloading attachments which come from unfamiliar sources since malware could be contained within them.
3. Install dependable antivirus programs with two-factor authentication to maintain complete security by keeping all software and devices at their latest updates.
4. Obtaining knowledge about recent cybersecurity dangers along with passing this information to your friends and relatives helps maintain their online safety.
5. Record all course Nance of Digital Arrest scams by informing both your local police department and cybercrime agencies. Such reports can stop further attacks directed at other individuals.
Conclusion
The criminal technique called Digital Arrest combines modern technology with human psychology to establish domination over victims. Digital technology usage expansion leads directly to increased vulnerability to digital threats. Awareness about how Digital Arrest functions along with appropriate protection steps enables people to minimize their vulnerability to attac ks. The best way to protect ourselves from changing cyber threats exists in both awareness and alertness in an interconnected digital environment.
References
- “5076535.pdf.” Accessed: Feb. 24, 2025. [Online]. Digital Arrest Scam in India- Challenges and Solutions
- “What is ‘digital arrest scam’ and how can you protect yourself? – The Hindu.” Accessed: Feb. 24, 2025. [Online]. Available: https://www.thehindu.com/news/national/digital-arrest-scam-how-to-protect-yourself/article68806494.ece
- “Protect Yourself from Digital Arrest Scam: How It Works & Warning Signs.” Accessed: Feb. 24, 2025. [Online]. Available: https://www.hdfcbank.com/personal/resources/learning-centre/vigil-aunty/how-digital-arrest-fraud-works
- V. Kandari, “What is Digital Arrest? Real-Life Cases and Prevention Tips !,” SurePass. Accessed: Feb. 24, 2025. [Online]. Available: https://surepass.io/blog/what-is-digital-arrest-real-life-cases-and-prevention-tips/
- “Understanding Digital Arrest: Protect Yourself from Cybercrimes | RBL Bank.” Accessed: Feb. 24, 2025. [Online]. Available: https://www.rblbank.com/blog/banking/safe-banking/the-rise-of-digital-arrest
- SAPD: Secure Authentication Protocol Development for Smart Healthcare Management Using IoT. (n.d.). IEEE Conference Publication | IEEE Xplore. https://ieeexplore.ieee.org/abstract/document/10315475
- Kumar, A., Shankar, A., Behl, A., Gupta, B. B., & Mavuri, S. (2023). Lights, camera, metaverse!: eliciting intention to use industrial metaverse, organizational agility, and firm performance. Journal of Global Information Management (JGIM), 31(8), 1-20.
- Liu, R. W., Guo, Y., Lu, Y., Chui, K. T., & Gupta, B. B. (2022). Deep network-enabled haze visibility enhancement for visual IoT-driven intelligent transportation systems. IEEE Transactions on Industrial Informatics, 19(2), 1581-1591.
- Zhou, Z., Li, Y., Li, J., Yu, K., Kou, G., Wang, M., & Gupta, B. B. (2022). Gan-siamese network for cross-domain vehicle re-identification in intelligent transport systems. IEEE transactions on network science and engineering, 10(5), 2779-2790.
- Katiyar A. (2024) Enhancing Cloud Computing Security Through Quantum-Inspired Evolutionary Approaches, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) What is Digital Arrest ? Understanding The New Cyber Threats, Insights2techinfo pp.1