By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
People now use the Internet of Things technology to manage everyday items with embedded smart technology such as refrigerators as well as security cameras. The benefits of IoT devices through convenience and efficiency come with substantial security dangers. This paper investigates the secret threats posed by IoT devices as it explains how hackers can access these gadgets and examines what happens when systems get compromised along with offering protection methods for users and producers. Knowing the natural flaws within IoT technology lets people defend their systems effectively against the rising cyber security threats. The article first reviews literature about IoT security before explaining both the analysis approach for IoT vulnerabilities and suggested solutions.
Introduction
Modern society depends on the Internet of Things technology to connect billions of devices that operate within the global domain. The devices under the Internet of Things umbrella gather and distribute information which then gets processed to enhance economic performance and operation efficiency and user comfort. IoT devices become accessible targets for cyberattacks because of their networked nature. Other than standard computing tools, IoT products normally operate without effective security protocols that increase their exposure to cyber criminals[1]. Criminals who hurt IoT devices can exploit them to access networks and steal information and cause physical damage. This paper investigates hidden security risks of IoT devices while explaining hacking methods and protective measures against such threats. The research consists of a literature examination of current work in addition to a method to evaluate IoT security flaws.
Literature Review
The accelerating adoption of IoT devices has prompted extensive research interest that brought forward many securities problem reports regarding this technology. This report analyzes vital pieces of research identified in current scholarly works.
1. IoT Security Vulnerabilities:
The findings of [2] showed that IoT devices remain defenseless because their authentication protocols are weak, and they lack encryption keys and insufficient firmware update processes. The research demonstrated how manufacturers choose cost-efficient functionality together with security and this practice leaves devices unprotected against attacks.
2. Botnet Attacks:
Expert analysis by [3] found that compromised IoT devices could be turned into weapons for strong Distributed Denial of Service (DDoS) attacks in the Mirai botnet assault during 2016. Default logos combined with unapplied security updates proved to be the fundamental entry points through which the botnet penetrated systems.
3. Privacy Concerns:
Research conducted by [4] that IoT device data remains unprotected despite its collection through numerous devices. The study pointed out examples which demonstrated how health data from wearable devices ended up in unsafe scenarios because of defective security practices.
4. Physical Safety Risks:
[5] conducted research to establish how devices from the Internet of Things system might endanger physical human health through security breaches. Medical devices that fall under compromise present dangerous risks that threaten patient survival because compromised insulin pumps along with pacemakers create life-threatening situations.
5. Mitigation Strategies:
The research by [6] presented different security solutions that depended on machine learning detection systems and blockchain-based data protection and universal IoT device security standards.
The review indicates that IoT devices require better security solutions because their risks emerge from multiple dimensions.
Methodology
The research design uses a mixed-methods analysis of IoT device problems to create solution recommendations. The given methodology includes multiple sequential steps.
1. Data Collection:
The analysis included assessment of information from academic journals, industry reports and case studies as part of secondary data collection activities.
Surveys together with interviews served as primary data collection methods to examine the actual IoT challenges and solutions through interactions with cybersecurity experts, IoT manufacturers and end-users.
2. Vulnerability Analysis:
A research group tested different kinds of IoT devices consisting of smart appliances and wearables and industrial sensors to identify vulnerabilities through weak passwords and uninstalled firmware updates and hazardous communication methods.
Test experts used Nmap and Metasploit tools as penetration testing instruments to conduct simulated attacks which exposed possible hacker access points.
3. Risk Assessment:
Various researchers evaluated IoT hack consequences through assessing their impact severity which involved privacy breaches and financial losses as well as physical harm.
A risk matrix enabled prioritization of vulnerabilities while directing the path toward implementing necessary risk control measures.
4. Solution Development:
The analysis enabled researchers to create recommended manufacturing procedures as well as user guidelines and policy recommendations.
Advanced technologies which include blockchain along with machine learning were investigated for improving IoT security.
5. Validation:
Security experts examined the proposed solutions before testing them in a simulated environment for measuring their efficiency.
The recommendations underwent changes after stakeholders’ input was received for improvement.
How IoT Devices Are Hacked
Hackers employ various techniques to compromise IoT devices, including:
1. Hacking tools known as brute force attack systems make attempts to decrypt weak passwords of default entries to infiltrate devices without authorization.
2. Security vulnerabilities in firmware become accessible to hackers whenever firmware stays outdated or remains unsecured.
3. An attack known as Man-in-the-Middle (MITM) allows hackers to intercept IoT device communication with control systems whereas they steal information or force the system with harmful instructions.
4. Botnet Recruitment uses compromised IoT devices to create botnets with Distributed Denial of Service (DDoS) and similar large-scale attacks as their main function.
5. Some hackers gain access to devices in physical form to implement malware or steal sensitive information.
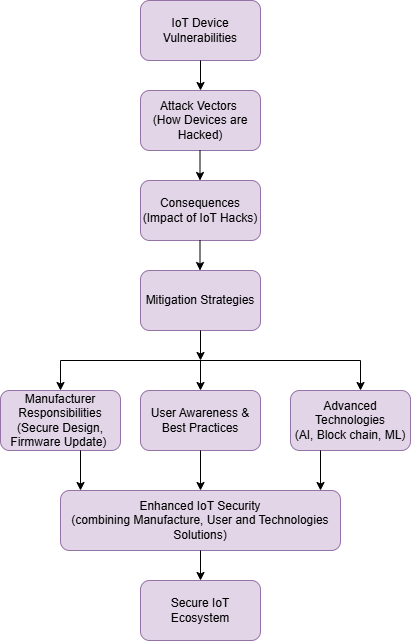
Mitigating the Risks
To address the hidden dangers of IoT devices, a multi-faceted approach is required:
1. Manufacturer Responsibility: Secure manufacturing should include the incorporation of strong encryption alongside security boot procedures. Devices need to receive planned firmware improvements together with system maintenance updates. Manufacturers must create original default passwords which users need to modify after device setup begins.
2. Network Security: The monitoring of IoT traffic requires deployment of both firewalls as well as intrusion detection systems. A breach impact minimization approach can be achieved by putting IoT devices into their distinct network segment.
3. Advanced Technologies: Potent artificial intelligence (AI) and machine learning (ML) systems operate in real time for threat detection and response. Blockchain technology implementation will improve device authentication processes and maintain data authenticity in the network.
Conclusion
The Internet of Things revolutionized our lifestyles as well as our work environments, yet it brought new security threats into the world. Computers designed with ease of use rather than security receive priority status because hackers focus on these items as their main targets. IoT hacks lead to devastating consequences that include both privacy violations and physical damage thus requiring effective security protection. Manufacturers should be held responsible for making IoT devices secure and users need education along with implementing powerful technologies to maintain the positive impact of these devices. All stakeholders should make addressing hidden IoT risks their principal concern because the IoT ecosystem shows no signs of slowing its growth.
References
- S. Prajapati and A. Singh, “Cyber-Attacks on Internet of Things (IoT) Devices, Attack Vectors, and Remedies: A Position Paper,” in IoT and Cloud Computing for Societal Good, J. K. Verma, D. Saxena, and V. González-Prida, Eds., Cham: Springer International Publishing, 2022, pp. 277–295. doi: 10.1007/978-3-030-73885-3_17.
- H. Pourrahmani, A. Yavarinasab, A. M. H. Monazzah, and J. Van Herle, “A review of the security vulnerabilities and countermeasures in the Internet of Things solutions: A bright future for the Blockchain,” Internet Things, vol. 23, p. 100888, Oct. 2023, doi: 10.1016/j.iot.2023.100888.
- B. Tushir, H. Sehgal, R. Nair, B. Dezfouli, and Y. Liu, “The Impact of DoS Attacks onResource-constrained IoT Devices:A Study on the Mirai Attack,” Apr. 19, 2021, arXiv: arXiv:2104.09041. doi: 10.48550/arXiv.2104.09041.
- S. Rizvi, R. Pipetti, N. McIntyre, J. Todd, and I. Williams, “Threat model for securing internet of things (IoT) network at device-level,” Internet Things, vol. 11, p. 100240, Sep. 2020, doi: 10.1016/j.iot.2020.100240.
- N. M. Thomasian and E. Y. Adashi, “Cybersecurity in the Internet of Medical Things,” Health Policy Technol., vol. 10, no. 3, p. 100549, Sep. 2021, doi: 10.1016/j.hlpt.2021.100549.
- H. Vargas, C. Lozano-Garzon, G. A. Montoya, and Y. Donoso, “Detection of Security Attacks in Industrial IoT Networks: A Blockchain and Machine Learning Approach,” Electronics, vol. 10, no. 21, Art. no. 21, Jan. 2021, doi: 10.3390/electronics10212662.
- Vajrobol, V., Saxena, G. J., Pundir, A., Singh, S., Gupta, B. B., Gaurav, A., & Rahaman, M. (2024). Identify spoofing attacks in Internet of Things (IoT) environments using machine learning algorithms. Journal of High Speed Networks.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
Cite As
Karthik V. (2025) When Your IoT Device Hacks You : The Hidden Danger of IoT Devices, Insights2techinfo pp.1