By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Zero-day DDoS attacks drive network disruption operations by utilizing unreported system vulnerabilities against networks and systems. These attacks differ from standard DDoS operations by using unacknowledged software and hardware and protocol vulnerabilities that prove extremely challenging for detection and mitigation. This article discusses how zero-day DDoS attacks have increased in popularity while examining their specific traits that create difficulties for organizations. The text presents resistance-building approaches to modern security threats coupled with strong defense techniques alongside community coordination in cybersecurity.
Introduction
Distributed Denial of Service (DDoS) attacks function as preferred weapons for attackers who want to stop online services in the continually transforming cybersecurity landscape. Zero-day DDoS attacks introduced sophisticated capabilities that make these network disruptors harder to predict during attacks[1]. Pre-existing unknown system weaknesses provide attackers with the opportunity to strike unsuspecting organizations who must then respond in short order. Protecting network infrastructure demands both the understanding of zero-day DDoS attack mechanisms and the creation of effective defense systems because these attacks are now appearing more frequently[2].
What are Zero-Day DDoS Attacks?
The term zero-day vulnerability applies to undiscovered software or hardware weaknesses which vendors along with the public are unaware of. Users who use unknown software defects to launch DDoS attacks through these defects are performing zero-day DDoS attacks. Zero-day DDoS attacks differ from standard DDoS attacks by exploiting unreported weaknesses found in system code and network protocols or application infrastructure[1].
Network protocols such as TCP/IP represent examples of DDoS attack targets along with popular web server software vulnerabilities during zero-day attacks. Attackers remain successful when using undisclosed vulnerabilities because standard security measures show no effectiveness until protective measures can be set in place.
The Growing Threat of Zero-Day DDoS
Multiple elements have led to the rising incidence of zero-day DDoS attacks.
1. Modern networks have advanced to such high complexity that they contain multiple devices and various network protocols in addition to multiple applications. Complicated networks leave numerous potential risks exposed because the expanded system area boosts the chances of unidentified vulnerabilities[3].
2. Modern cybercriminals and governmental entities refine their zero-day vulnerability identification abilities to such degrees that they can find these covert weaknesses effectively. Fuzz testing and reverse engineering methods let attackers find undiscovered flaws through their advanced tools and techniques[3].
3. Attackers have established significant valuations in the illicit market for zero-day vulnerabilities since they aim to deploy these exploits during DDoS attacks along with various other malicious operations[4].
4. The expansion of Internet of Things (IoT) devices has added various network vulnerabilities because of increased adoption rates. Security faults in numerous IoT devices attract zero-day DDoS attack targets because these devices do not possess acceptable security capabilities[4].
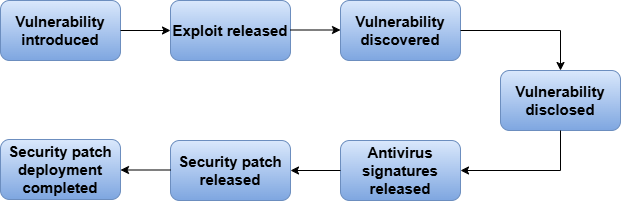
Challenges in Mitigating Zero-Day DDoS Attacks[5]
The protection of organizations and security experts becomes difficult in the face of zero-day DDoS attacks because of specific obstacles they encounter.
1. Organizations must operate without prior attack information because zero-day vulnerabilities remain unknown to detection tools and preconfigured mitigation strategies. Organizations face difficulties when detecting and reacting to attacks in real-time because they lack knowledge about such attacks.
2. Attackers can immediately use zero-day vulnerabilities because they spot them before platform providers create necessary patches and protection solutions. The fast pace of exploitation provides organizations with minimal reaction time.
3. New vulnerability exploits known as zero-day DDoS attacks extend their destructive impact by wrecking the infrastructure shared by multiple organizations including the intended target.
4. The process of defending against zero-day DDoS attacks necessitates intense resources that involve sophisticated threat intelligence together with trained staff members along with specialized toolsets. Companies with limited size find it difficult to match the resource requirements of these demands.
The Role of AI and Machine Learning
Zero-day DDoS attacks receive greater combat effectiveness from the rising application of artificial intelligence (AI) and the use of machine learning (ML) technologies. The analysis of large network traffic data by these technologies detects abnormal behavior which allows them to forecast upcoming security concerns. Organizations that implement AI and ML solutions for their defense increasing gain the ability to find and react immediately to zero-day attacks[6].
AI-powered networks function to track system activities that identify abnormal conduct through patterns of traffic changes or unexpected request sequences. Such monitoring systems help organizations execute automated response techniques which include traffic redirection alongside blocking unwanted IP addresses thus decreasing attack response times[7].
Conclusion
Zero-day DDoS attacks pose a substantial and increasing menace to businesses of any scope. Such attacks exploit previously unheard-of vulnerabilities to create massive damage throughout networks. With proper recognition of the distinct features in zero-day DDoS attacks and active defense preparation organizations can improve their network safety capabilities.
Security against zero-day DDoS attacks depends on teamwork between organizations and their continuous development of new security solutions and readiness against attacks. Security intelligence sharing serves with advanced technology implementations and secure security protocols to help the cyber community monitor and counter forthcoming network disruption approaches.
References
- A. B. De Neira, B. Kantarci, and M. Nogueira, “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Comput. Netw., vol. 222, p. 109553, Feb. 2023, doi: 10.1016/j.comnet.2022.109553.
- M. Roopak, S. Parkinson, G. Y. Tian, Y. Ran, S. Khan, and B. Chandrasekaran, “An unsupervised approach for the detection of zero-day distributed denial of service attacks in Internet of Things networks,” IET Netw., vol. 13, no. 5–6, pp. 513–527, 2024, doi: 10.1049/ntw2.12134.
- K. Hamid, M. W. Iqbal, M. Aqeel, X. Liu, and M. Arif, “Analysis of Techniques for Detection and Removal of Zero-Day Attacks (ZDA),” in Ubiquitous Security, G. Wang, K.-K. R. Choo, J. Wu, and E. Damiani, Eds., Singapore: Springer Nature, 2023, pp. 248–262. doi: 10.1007/978-981-99-0272-9_17.
- L. Yee Por et al., “A Systematic Literature Review on AI-Based Methods and Challenges in Detecting Zero-Day Attacks,” IEEE Access, vol. 12, pp. 144150–144163, 2024, doi: 10.1109/ACCESS.2024.3455410.
- Y. Guo, “A review of Machine Learning-based zero-day attack detection: Challenges and future directions,” Comput. Commun., vol. 198, pp. 175–185, Jan. 2023, doi: 10.1016/j.comcom.2022.11.001.
- V. Vajrobol et al., “Identify spoofing attacks in Internet of Things (IoT) environments using machine learning algorithms,” J. High Speed Netw., p. 09266801241295886, Dec. 2024,.
- M. Rahaman, P. Pappachan, S. M. Orozco, S. Bansal, and V. Arya, “AI Safety and Security,” in Challenges in Large Language Model Development and AI Ethics, IGI Global Scientific Publishing, 2024, pp. 354–383.
- Liu, R. W., Guo, Y., Lu, Y., Chui, K. T., & Gupta, B. B. (2022). Deep network-enabled haze visibility enhancement for visual IoT-driven intelligent transportation systems. IEEE Transactions on Industrial Informatics, 19(2), 1581-1591.
- Zhou, Z., Li, Y., Li, J., Yu, K., Kou, G., Wang, M., & Gupta, B. B. (2022). Gan-siamese network for cross-domain vehicle re-identification in intelligent transport systems. IEEE transactions on network science and engineering, 10(5), 2779-2790.
- Cajes N. (2025) Predicting and Preventing DDoS Attacks with Deep Learning, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) Zero Day DDoS : Unmasking the Next Generation of Network Disruption, Insights2techinfo pp.1