By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
5G technology unites with IoT functions to create an era of hyper-connectivity because it delivers improved speeds together with reduced delays and enhances network capabilities. The extensive deployment of IoT devices comes hand in hand with important security challenges because these devices expand the potential targets for cyber attackers. This paper discusses how 5G technology creates IoT security opportunities by using better encryption methods and network slicing functions in combination with artificial intelligence for threat identification. The security analysis includes identification of three critical threats which involve DDoS attacks escalating and unauthorized access attempts and supply chain security weaknesses. A flowchart combined with a table structure enables better comprehension of security risks along with their solutions within 5G-powered IoT systems.
Introduction:
The merger between IoT expansion and 5G network deployment creates revolutionary industrial changes that transform healthcare systems, smart city operations and provides ground for autonomous vehicles. The 5G technology standards which incorporate ultra-low latency and high-speed data transfer capabilities together with massive device connectivity allows unprecedented real-time applications and automation of systems. The 5G promise extends past speed enhancement because it reshapes device communication which leads to complete connectivity realization[1].
The advancement of technologies through 5G creates fresh protection risks for users. Security models that existed in the past fall short of Stopping attackers from breaching sensitive infrastructure and data when the total number of connected devices reaches huge proportions. The nature and intensity of security threats change according to the basic or advanced capabilities of IoT devices which may include sensors or autonomous systems. A security failure within 5G networks with their capacity to link millions of devices per square-kilo meter will produce massive data breaches alongside operational disruptions as well as data theft. A resilient digital ecosystem needs robust security protocols that should be integrated with the development of 5G and IoT technology for its successful implementation[2].
Flow chart of 5G-IoT Communication:
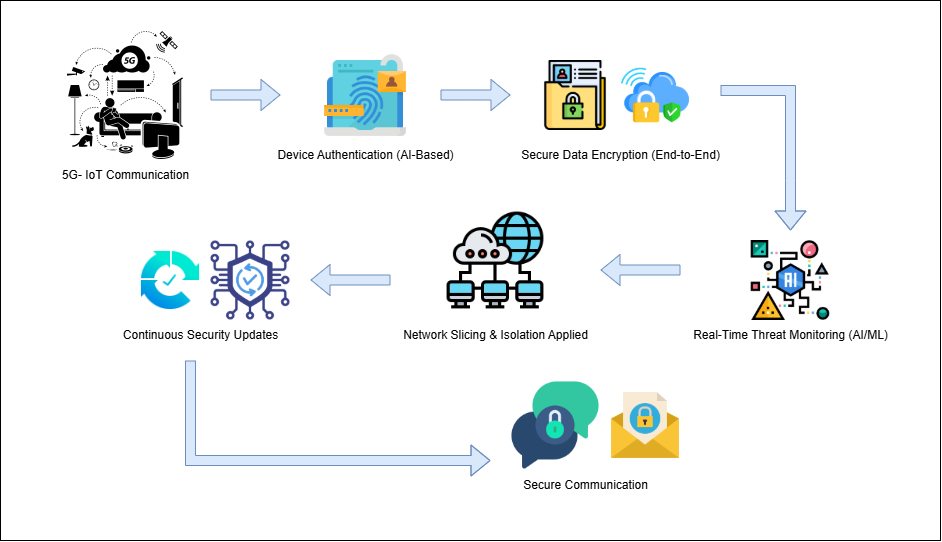
Opportunities in 5G for IoT Security
5G technology establishes multiple security enhancements which enable better IoT protection measures. The major advantage that network slicing delivers is the ability to form detached network partitions. The isolated network segments through network slicing operate as independent units so a security breach in one segment stays confined to itself thereby safeguarding IoT applications. The implementation of cryptographic encryption methods within 5G communications using 256-bit encryption together with advanced security mechanics has proven to strengthen IoT system security by providing better data protection[3]. AI and Machine Learning (ML) have proved to be essential elements for increasing IoT security because of their ability to integrate with IoT systems. Artificial intelligence (AI) safety measures monitor web traffic and identify anomalies and prevent digital assaults instantly. Security operations gain through automation result in immediate threat identification along with swift responses that establish essential defense in highly connected systems[4].
The security mechanisms used for authentication make significant improvements throughout 5G network systems. IoT security receives protection against unauthorized access through three security solutions including biometric authentication and blockchain identities and AI-managed access protocols[5]. The security of edge computing enhances total security performance because it processes information directly at the device level which decreases vulnerability to outside attacks and minimizes data transport security risks[6]. AI-based advanced intrusion detection systems (IDPS), which are introduced with 5G implementation, strengthen the security of networks against cyberattacks[7]. New detection frameworks and neutralization mechanisms located in 5G infrastructure operate to protect IoT devices from escalating cyber threats before they affect the systems’ security status.
Security Threats in 5G-Enabled IoT Networks
5G technology brings forth fresh security points of weakness into IoT structures despite its many positive aspects. Security threats exist mostly because of the wider exposure that 5G generates. The numerous connected devices create more opportunities for cyberattacks to occur at an increased rate. Attacking IoT devices is possible through easily exploitable weak security configurations since unauthorized access and data manipulation as well as large-scale cyberattacks become feasible[8]. The existing security problem space is worsened by Distributed Denial-of-Service (DDoS) attacks. The powerful speed capabilities of 5G networks help attackers to expand the impact of their attacks through massive traffic overload that disables server and network infrastructure. IoT devices lack robust security standards that make such devices vulnerable to exploitation by hackers who can use them as botnet tools in massive DDoS attacks[9].
Changes to IoT security would benefit from enhanced measures against unauthorized system entry. Companies find their traditional authentication approaches ineffective for controlling massive numbers of attached devices. When security protocols remain incomplete or unsecured APIs exist with weak default credentials the attackers can take unauthorized control of essential infrastructure together with individual devices. Attackers exploit vulnerable weaknesses that allow them to take control of industrial systems and individual devices which include smart homes and healthcare control points because the consequences from these intrusions are grave. A major security concern stems from the practice of eavesdropping while data interception takes place. The increasing number of devices engaging in wireless communication makes man-in-the-middle (MITM) attacks a more relevant threat[10]. When encryption is absent sensitive data passing between devices remains at risk since attackers could steal and misuse this information that includes personal information together with financial transactions and business-confidential communications.
Comparison table of Traditional IoT vs. 5G-Enabled IoT Security Features:
Feature | Traditional IoT Security | 5G-Enabled IoT security |
Data Transmission Speed | Moderate | Ultra-Fast |
Network Latency | High | Low |
Encryption Standards | Basic | Advanced |
Attack Surface | Limited | Expanded |
Authentication | Less Secure | Stronger Biometric & AI- Based |
Mitigation Strategies for 5G-IoT Security Risks
Organizations should enact these countermeasures against security threats:
- Mathematical approaches to Zero-Trust Architecture (ZTA) determine ongoing authentication for every user and device.
- Secure Communication along with Strong Encryption requires implementation of end-to-end protection for data transmission.
- Regular Firmware and Software Updates: Addressing vulnerabilities in IoT devices.
- AI-Based Threat Detection: Using real-time monitoring and AI-powered security solutions.
- Regulatory Compliance: Adhering to international security standards for IoT and 5G networks.
Conclusion:
The security potential of IoT through the 5G connectivity remains significant although it delivers notable security vulnerabilities. Organizations prevent security risks through the use of threat detection managed by AI and encryption and authenticated systems with robust mechanisms. Security measures must be proactively implemented to protect the robustness of an IoT infrastructure as 5G deployment progresses.
References:
- K. V. Sakhare, V. Vyas, and A. S. Shastri, Metaheuristics for Enterprise Data Intelligence. CRC Press, 2024.
- B. Singh and C. Kaunert, “Integration of Cutting-Edge Technologies such as Internet of Things (IoT) and 5G in Health Monitoring Systems: A Comprehensive Legal Analysis and Futuristic Outcomes,” GLS Law J., vol. 6, no. 1, Art. no. 1, Jan. 2024, doi: 10.69974/glslawjournal.v6i1.123.
- S. Selvakumar, A. Ahilan, B. Ben Sujitha, and N. Muthukumaran, “Crystals kyber cryptographic algorithm for efficient IoT D2d communication,” Wirel. Netw., Jul. 2024, doi: 10.1007/s11276-024-03790-6.
- “Identify spoofing attacks in Internet of Things (IoT) environments using machine learning algorithms – Vajratiya Vajrobol, Geetika Jain Saxena, Amit Pundir, Sanjeev Singh, Brij B. Gupta, Akshat Gaurav, Mosiur Rahaman, 2024.” Accessed: Feb. 07, 2025. [Online]. Available: https://journals.sagepub.com/doi/full/10.1177/09266801241295886
- C. Zheng et al., “Decentralized artificial intelligence in construction using blockchain,” Autom. Constr., vol. 166, p. 105669, Oct. 2024, doi: 10.1016/j.autcon.2024.105669.
- M. Rahaman, C.-Y. Lin, P. Pappachan, B. B. Gupta, and C.-H. Hsu, “Privacy-Centric AI and IoT Solutions for Smart Rural Farm Monitoring and Control,” Sensors, vol. 24, no. 13, Art. no. 13, Jan. 2024, doi: 10.3390/s24134157.
- V. Vajrobol et al., “Identify spoofing attacks in Internet of Things (IoT) environments using machine learning algorithms,” J. High Speed Netw., p. 09266801241295886, Dec. 2024, doi: 10.1177/09266801241295886.
- I. Stellios, P. Kotzanikolaou, M. Psarakis, C. Alcaraz, and J. Lopez, “A Survey of IoT-Enabled Cyberattacks: Assessing Attack Paths to Critical Infrastructures and Services,” IEEE Commun. Surv. Tutor., vol. 20, no. 4, pp. 3453–3495, 2018, doi: 10.1109/COMST.2018.2855563.
- P. Kumari and A. K. Jain, “A comprehensive study of DDoS attacks over IoT network and their countermeasures,” Comput. Secur., vol. 127, p. 103096, Apr. 2023, doi: 10.1016/j.cose.2023.103096.
- “A Survey of Man In The Middle Attacks | IEEE Journals & Magazine | IEEE Xplore.” Accessed: Feb. 07, 2025. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/7442758
- Sedik, A., Hammad, M., Abd El-Samie, F. E., Gupta, B. B., & Abd El-Latif, A. A. (2022). Efficient deep learning approach for augmented detection of Coronavirus disease. Neural Computing and Applications, 1-18.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- REDDY K.T (2023) Unveiling the Power of Naive Bayes in Phishing Detection, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) 5G and IoT Security: Opportunities and Threats in the Hyper-Connected Era, Insights2Techinfo, pp.1