By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Billions of devices worldwide have connected because of the Internet of Things (IoT) revolutionized the way we handle technology through its operations. The exceptional convenience and efficiency provided by IoT systems leads to critical security problems. This paper examines both the dangers of excessive connectivity and weaknesses within IoT devices and presents step-by-step security improvements. Human and organizational security can be safeguarded through risk awareness combined with the implementation of security practices that lead to a safe IoT environment.
Introduction:
Devices across the IoT ecosystem are growing in popularity at an exponential rate because smart home appliances now join industrial sensors in their ubiquity. The collection and processing and distribution of large data volumes by these devices allow organizations to make smarter choices which lead to automation. The enhanced connectivity produces more opportunities for cybercriminals to find entry points during attacks. The necessity of IoT security surpasses being an option because it has become an essential requirement. This research examines IoT security threats and presents a method to defend against vulnerabilities in addition to describing why securing these devices remains challenging[1].
Security Risks in IoT
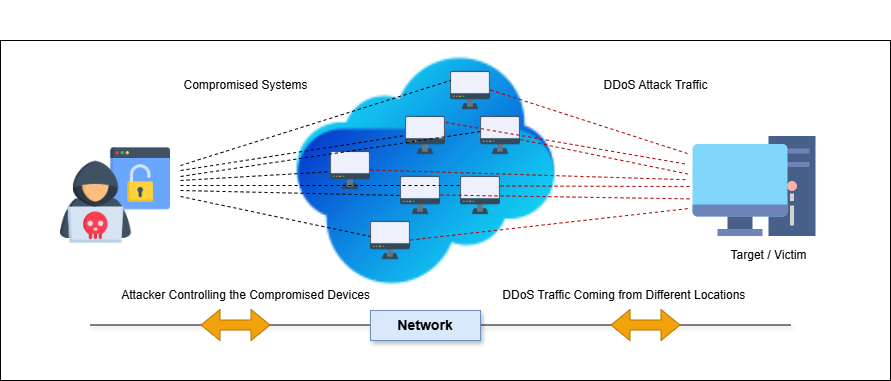
IoT security weaknesses develop from different sources like weak encryption together with bad authentication procedures and unfinished firmware updates. Various IoT devices do not incorporate strong security protocols because of which unauthorized parties can access them or breach data or launch cyberattacks[2]. The exposure of devices to cybercriminals occurs through the exploitation of passwords and authentication issues which lets them control devices over distance bringing major results such as industrial disruption and espionage activities. The collection of personal and corporate data by IoT devices makes them vulnerable to hackers who want to exploit vulnerable information for data breaches. Infected IoT devices run within botnet attacks that are used to perform Distributed Denial-of-Service (DDoS) strikes affecting online services at scale. IoT devices minimize user privacy when operated due to their limited built-in protection mechanisms that allow third parties to monitor or obtain sensitive data without authorization. Attacks against IoT firmware and the use of un-updated software make security risks worse because unaddressed vulnerabilities allow attackers to enter IoT systems directly. Security of the IoT infrastructure depends on actively handling all current risks[3].
Strategies for IoT Security
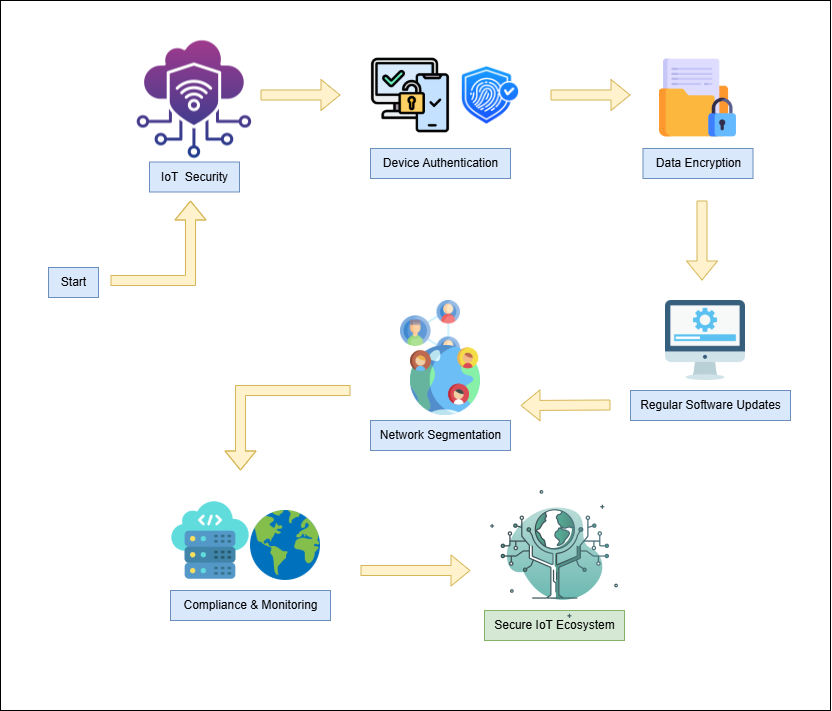
Security protection of IoT environments requires complete protective measures which organizations and individual users must implement. A leading method for IoT defense comprises authorization solution and authentication control strategies that incorporate multiple authentication elements (MFA) and biometrics and safe credential systems for blocking unapproved access attempts. Data encryption provides an advanced security measure that turns sensitive data into unintelligible codes so cybercriminals cannot understand intercepted information when it is moving from point to point[5]. To ensure IoT device security users and manufacturers must collaborate on quick security patch deployments because software updates combined with proper patch management help seal potential security holes. Network segmentation serves as a defense mechanism to split IoT networks into protective sections which stops trackless cyberattack spread and blocks unauthorized system access. The adherence to industry security standards including ISO/IEC 27001 as well as NIST guidelines and GDPR regulations enables IoT devices to follow best security practices. The implementation of these security strategies as a comprehensive whole will greatly improve IoT environment security positions while reducing risks for safe reliable operations[6].
Emerging Trends in IoT Security
Technology development creates new IoT security patterns which will define its future direction. The detection of cyber threats together with their prevention happens in real time through the implementation of AI and ML technologies. Modern IoT systems leverage these technologies to process large amounts of data thus discovering security breach indicators[7]. The emerging trend in IoT security investigates blockchain technology to build distributed tamper-protection solutions for IoT networks. The Zero Trust Architecture (ZTA) has started to increase in popularity because it continuously verifies device and user identities before granting permission. These advancing trends indicate that safety frameworks in IoT networks will become reactive and flexible security approaches[8].
Regulatory and Compliance Considerations
The global community of governments together with their regulatory bodies has started to implement strict security protocols for the Internet of Things domain. Multiple regulations together with compliance frameworks exist to enforce proper best security practices upon both IoT manufacturers and users. Customers can find guidelines for IoT security protections through the GDPR of the European Union together with the Cybersecurity Improvement Act in the United States and ISO standards. Data safety and user privacy together with operational integrity depends heavily on strict adherence to these privacy rules because IoT security risks reduce effectively. Businesses need to update their knowledge about developing regulatory standards and deploy proper protection steps to maintain compliance[9].
Conclusion:
More evolution occurs in IoT because security challenges also increase. IOT security depends on a preventive strategy which requires authentication techniques together with encryption methods and system upgrade protocols and security standard compliance. Futuristic digital security depends upon organizations along with individuals understanding their essential role to protect their IoT devices from harm. IoT security measures enable us to access its entire potential while reducing hazards within the modern interconnected ecosystem.
References:
- A. Ayub Khan, A. A. Laghari, Z. A. Shaikh, Z. Dacko-Pikiewicz, and S. Kot, “Internet of Things (IoT) Security With Blockchain Technology: A State-of-the-Art Review,” IEEE Access, vol. 10, pp. 122679–122695, 2022, doi: 10.1109/ACCESS.2022.3223370.
- N. M. Karie, N. M. Sahri, W. Yang, C. Valli, and V. R. Kebande, “A Review of Security Standards and Frameworks for IoT-Based Smart Environments,” IEEE Access, vol. 9, pp. 121975–121995, 2021, doi: 10.1109/ACCESS.2021.3109886.
- P. Kumari and A. K. Jain, “A comprehensive study of DDoS attacks over IoT network and their countermeasures,” Comput. Secur., vol. 127, p. 103096, Apr. 2023, doi: 10.1016/j.cose.2023.103096.
- P. Kumari and A. K. Jain, “A comprehensive study of DDoS attacks over IoT network and their countermeasures,” Comput. Secur., vol. 127, p. 103096, Apr. 2023, doi: 10.1016/j.cose.2023.103096.
- S. P. Otta, S. Panda, M. Gupta, and C. Hota, “A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure,” Future Internet, vol. 15, no. 4, Art. no. 4, Apr. 2023, doi: 10.3390/fi15040146.
- N. M. Karie, N. M. Sahri, W. Yang, C. Valli, and V. R. Kebande, “A Review of Security Standards and Frameworks for IoT-Based Smart Environments,” IEEE Access, vol. 9, pp. 121975–121995, 2021, doi: 10.1109/ACCESS.2021.3109886.
- P. Radanliev, D. De Roure, C. Maple, J. R. C. Nurse, R. Nicolescu, and U. Ani, “AI security and cyber risk in IoT systems,” Front. Big Data, vol. 7, Oct. 2024, doi: 10.3389/fdata.2024.1402745.
- P. Dhiman et al., “A Review and Comparative Analysis of Relevant Approaches of Zero Trust Network Model,” Sensors, vol. 24, no. 4, Art. no. 4, Jan. 2024, doi: 10.3390/s24041328.
- S. Fischer-Hübner et al., “Stakeholder perspectives and requirements on cybersecurity in Europe,” J. Inf. Secur. Appl., vol. 61, p. 102916, Sep. 2021, doi: 10.1016/j.jisa.2021.102916.
- Poonia, V., Goyal, M. K., Gupta, B. B., Gupta, A. K., Jha, S., & Das, J. (2021). Drought occurrence in different river basins of India and blockchain technology based framework for disaster management. Journal of Cleaner Production, 312, 127737.
- Ajmal, M. S., Iqbal, Z., Khan, F. Z., Ahmad, M., Ahmad, I., & Gupta, B. B. (2021). Hybrid ant genetic algorithm for efficient task scheduling in cloud data centers. Computers and Electrical Engineering, 95, 107419.
- Kasa A.S. (2024) AI Strategies for Phishing Email Detection, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) IoT Security: Navigating the Risks of a Hyper-Connected World, Insights2Techinfo, pp.1