By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Through IoT, many gadgets spread across hundreds of millions of the Internet of Things and destinations have enhanced personal as well as business activities. The network advantages come with substantial security risks created by connected devices. The absence of secure protection features in IoT devices leads to increased vulnerability against cybercriminals. The article conducts a study of IoT security risks starting with case study analysis of real incidents then proposes strategies to protect against such threats. A flowchart demonstrates the complete process which helps secure IoT environments by presenting an essential security framework.
Introduction:
The growth of IoT devices transformed various sectors including residential automation along with medical care services and the transportation industry together with industrial production lines. IoT devices remain vulnerable because their convenient features including universal connection and distance-based usage and information sharing capacity. Security is frequently overlooked during the design phase of IoT devices because makers of these devices do not place security as their main concern. Inadequate security measures during the development stage have resulted in a dramatic increase of cyber threats which includes data breaches alongside unauthorized access and extensive Distributed Denial of Service (DDoS) attacks[1].
Understanding IoT Security Risks:
Device Vulnerabilities: Attackers find IoT devices vulnerable because they include default passwords and outdated firmware and minimal processing capacity[2].
Data Privacy Concerns: The data collection process by IoT devices creates serious privacy issues because they gather extensive amounts of private information. An absence of encryption allows cyber thieves to capture genuine device information through interception events thus leading to privacy violations[3].
Insecure Communication Channels: Attacks on security channels occur due to vulnerable unencrypted protocols which make data flowing between devices open to interception and malicious operations[2].
Botnet Exploitation: An attack system monitors IoT devices through exploit-based botnets that provide attackers with control of numerous infected systems[2].
Physical Security Risks: Public and remote IoT devices face physical security risks because intruders can physically tamper with them which leads to device manipulation together with unauthorized access[4].
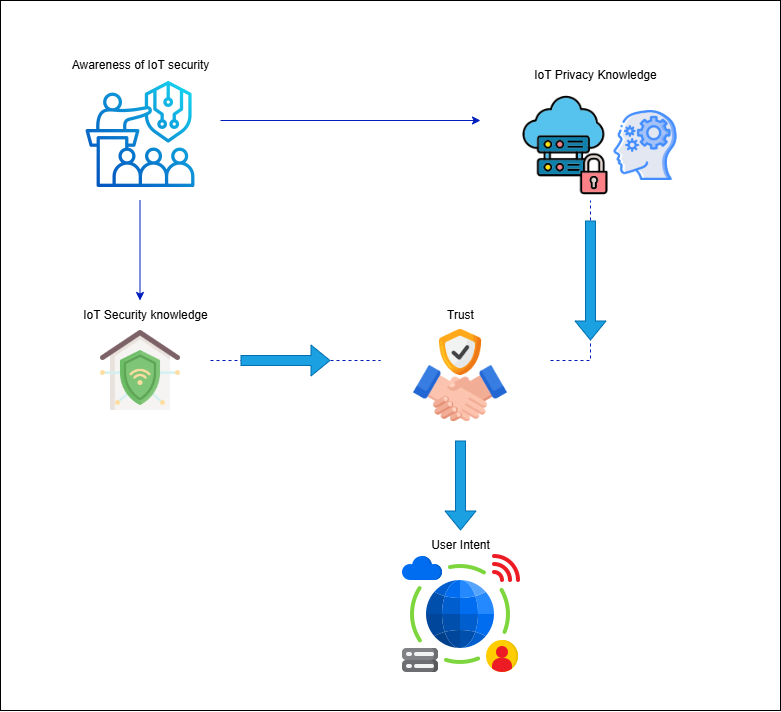
Strategies to Mitigate IoT Security Risks:
- Secure Device Configuration: Devices should receive security by design through password replacement of defaults and service disabling of unneeded features along with authentication power-ups.
- Regular Software Updates: Early-release software updates should be enabled to execute the most recent security fixes automatically.
- Data encryption: Data protection against unauthorized access becomes possible through encryption of data both when it rests within storage systems and during data transfers.
- Network Segmentation: IoT devices should exist inside their own separate network domain to prevent damage from a security breach for core network components.
- Security by Design: The security measures should be incorporated into devices before their design phase through secure coding practices with rigorous testing measures.
- Continuous Monitoring: This Continuous Monitoring uses technologies for ongoing surveillance in conjunction with detection systems for intrusions to quickly identify and address security risks.
- User Awareness and Training: Users should receive awareness training regarding IoT security challenges combined with practical suggestions which protect against standard mistakes.
Real-World IoT Security Incidents:
- The Mirai Botnet Attack (2016): A massive botnet operated by the Mirai Botnet Attack targeted vulnerable IoT devices (2016) to perform DDoS attacks against major internet services[6].
- Stuxnet Worm: Stuxnet Worm appeared as a complex cyber weapon that hit industrial control systems to show that IoT weaknesses could damage essential infrastructure[7].
- Smart Home Breaches: Hacker attacks on smart home devices produced two severe outcomes by controlling both cameras and thermostats which threatened personal privacy[8].
- The Jeep Cherokee Hack (2014): Security experts demonstrated the Jeep Cherokee Hack (2015) by taking over essential vehicle operations like steering direction and transmission and braking methods through the car’s infotainment system. Contemporary vehicle systems revealed problematic security weaknesses after a compromising incident occurred[9].
- Verkada Camera Breach (2021): In the 2021 Verkada Camera Breach attackers seized control of more than 150,000 surveillance cameras that Verkada operated for various institutions including hospitals and prison facilities and business headquarters. The attack exposed the security dangers of maintaining Internet-of-Things management services at one central location[10].
Flow chart of IoT security Framework:
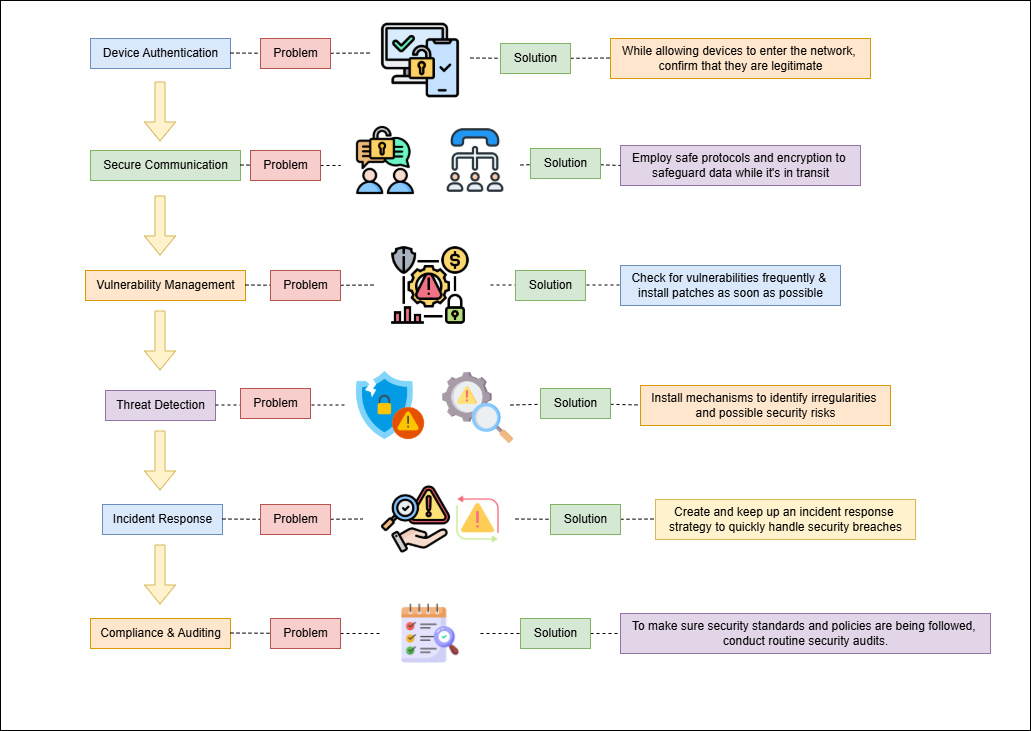
Conclusion:
The increase in IoT landscape development brings about escalating security challenges. Establishing secure IoT operations needs a complete method based on strong device defenses and protected network protocols alongside system update routines and continual monitoring activities. A resilient IoT ecosystem requires efforts of collaboration between device manufacturers and service providers and policymakers who work with end-users. Security measures that break vulnerabilities create a protected IoT system which emits both safety and security benefits for the connected world.
References:
- M. H. Ali et al., “Threat Analysis and Distributed Denial of Service (DDoS) Attack Recognition in the Internet of Things (IoT),” Electronics, vol. 11, no. 3, Art. no. 3, Jan. 2022, doi: 10.3390/electronics11030494.
- S. Rizvi, R. Orr, A. Cox, P. Ashokkumar, and M. R. Rizvi, “Identifying the attack surface for IoT network,” Internet Things, vol. 9, p. 100162, Mar. 2020, doi: 10.1016/j.iot.2020.100162.
- M. A. Obaidat, S. Obeidat, J. Holst, A. Al Hayajneh, and J. Brown, “A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures,” Computers, vol. 9, no. 2, Art. no. 2, Jun. 2020, doi: 10.3390/computers9020044.
- H. A. Khattak, M. A. Shah, S. Khan, I. Ali, and M. Imran, “Perception layer security in Internet of Things,” Future Gener. Comput. Syst., vol. 100, pp. 144–164, Nov. 2019, doi: 10.1016/j.future.2019.04.038.
- A. Koohang, C. S. Sargent, J. H. Nord, and J. Paliszkiewicz, “Internet of Things (IoT): From awareness to continued use,” Int. J. Inf. Manag., vol. 62, p. 102442, Feb. 2022, doi: 10.1016/j.ijinfomgt.2021.102442.
- A. Affinito, S. Zinno, G. Stanco, A. Botta, and G. Ventre, “The evolution of Mirai botnet scans over a six-year period,” J. Inf. Secur. Appl., vol. 79, p. 103629, Dec. 2023, doi: 10.1016/j.jisa.2023.103629.
- S. Gajek, M. Lees, and C. Jansen, “IIoT and cyber-resilience,” AI Soc., vol. 36, no. 3, pp. 725–735, Sep. 2021, doi: 10.1007/s00146-020-01023-w.
- B. Hammi, S. Zeadally, R. Khatoun, and J. Nebhen, “Survey on smart homes: Vulnerabilities, risks, and countermeasures,” Comput. Secur., vol. 117, p. 102677, Jun. 2022, doi: 10.1016/j.cose.2022.102677.
- Y. Usman, P. K. Gyawali, S. Gyawali, and R. Chataut, “The Dark Side of AI: Large Language Models as Tools for Cyber Attacks on Vehicle Systems,” in 2024 IEEE 15th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), Oct. 2024, pp. 169–175. doi: 10.1109/UEMCON62879.2024.10754676.
- A. Pawlicka, D. Puchalski, M. Pawlicki, R. Kozik, and M. Choraś, “How to secure the IoT-based surveillance systems in an ELEGANT way,” in 2023 IEEE International Conference on Cyber Security and Resilience (CSR), Jul. 2023, pp. 636–640. doi: 10.1109/CSR57506.2023.10224938.
- Gokasar, I., Pamucar, D., Deveci, M., Gupta, B. B., Martinez, L., & Castillo, O. (2023). Metaverse integration alternatives of connected autonomous vehicles with self-powered sensors using fuzzy decision making model. Information Sciences, 642, 119192.
- Zhou, Z., Li, Y., Li, J., Yu, K., Kou, G., Wang, M., & Gupta, B. B. (2022). Gan-siamese network for cross-domain vehicle re-identification in intelligent transport systems. IEEE transactions on network science and engineering, 10(5), 2779-2790.
- Neelapareddigari P. (2024) Machine Learning for Phishing detection, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Breaking the Chain: Mitigating IoT Security Risks in a Connected World, Insights2Techinfo, pp.1