By: Dhanush Reddy Chinthaparthy Reddy, Department of Computer Science and Artificial Intelligence, Madanapalle Institute of Technology and Science, Angallu(517325), Andhra Pradesh
Abstract
With the constantly emerging technologies in the digital platform, more emphasis is placed on the roles of Artificial Intelligence (AI) and cybersecurity. With the help of its characteristics of processing big amounts of data, identifying trends and patterns, automating work AI has impacted traditional cybersecurity approaches both positively – by providing better tools to combat cyber threats – and negatively – by introducing new problems to resolve. The goal of this paper is to take the reader through an understanding of how the elements of AI work in cybersecurity and the general principles of AI that people should understand, to do with threat detection through to responsive measures and even the use of AI in threats to digital structures. The discussion also reviews the impact of AI usage on cybersecurity as well as the possible risks of AI proliferation within the investigations and applies efficient examination of the implementation of new technologies. From this paper, the readers will be in a position to comprehend how the future of cyber security is being impacted on by AI.
Keywords: Artificial Intelligence, Cybersecurity, Threat Detection
Introduction
CIS is an important concern in today’s digital world where Internet and other connected technologies are the part of almost all architectures of the modern world. Whether it concerns one’s own data, an enterprise’s data, or a nation’s critical infrastructure’s data – digital assets are as valuable as they are vulnerable. Yet with the growth of this technological environment, the threats and risks also increase significantly. As much as these measures remain useful, they are rapidly being overwhelmed by the kinds of risks that characterize today’s cyberspace. In this respect, Artificial Intelligence (AI) has become one of the hottest trends in the sphere of cybersecurity as it provides practitioners and theoreticians with new potent weapons against a rising diverse and sophisticated threat.
AI is neither inherently good or bad for the cybersecurity of a business but can help or hinder depending on how it is implemented. Some of the ways through which takes advantage of it includes; Its capacity to undertake large and complex analysis on data sets not seen before; thus giving it a higher analytical ability in terms of identifying trends, detecting uncommon occurrences or even responding to risks. Automated threat detection systems, such as AI based, can discover new threats and attack paths that may not be discernible to the human security specialist or the conventional security software. However, AI security can civil service the time-consuming security work daily and save time human for urgent serious and better conflict-solving decisions. This increases the effectiveness of the cybersecurity operations while also decreasing the Time to Attack for any attacker who wants to target a system.[1]
AI does not only provide improvement in the efficiency of cybersecurity but myriad more. It also has the feature of predicting threats before they start to become a issue and organizations can prepare a contingency plan. There is Akamai AI that can predict attack types that are most likely to occur and suggests procedures that can be taken to reduce likelihood. Such a change from a passive to an active protection model is now more necessary to combat a constantly adapting enemy in the cyber realm.
AI in Offensive Cyber Operations
the same tools that were created to secure the systems can be turned against them by their enemies. Cybercriminals as well as nation-state hackers are employing AI as a way of increasing the level of intelligence, quickness, and efficiency through which most of the attack methods are carried out[2]. For instance, AI can be employed to launch more efficient phishing attacks that are more convincing since the tool will analyse multiple sets of data for use in addressing potential victims. Automated malware is capable of learning based on events occurring in real time and alter its behaviour so that it shall not set off alarms with the software applications.[3] Furthermore, AI makes it possible to search for such weaknesses at a scale and speed that is impossible for any human, and thus allow the attackers to seize on them before they can be secured. The idea of involving AI to perform unaided cyber-attacks where the AI persists and selects its objectives and approach on its own is quite ethically and securely questionable. In the context of the constant growth of AI, the problem of its application in committing offences in the sphere of cyber security is becoming more and more actual, that.
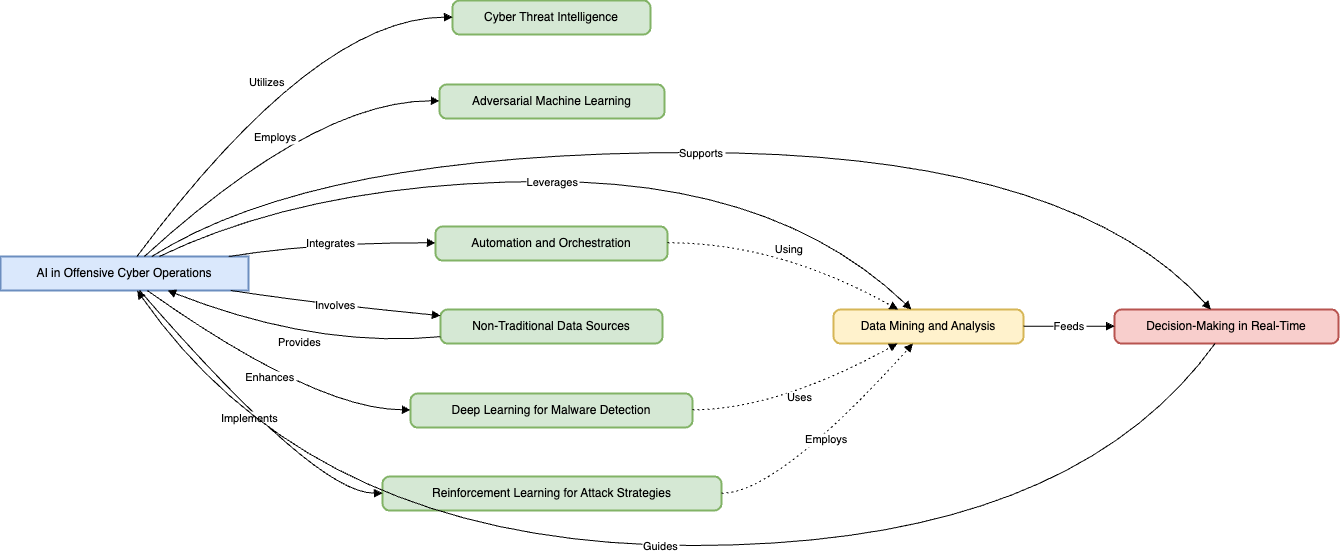
As a capability for applying offensive cyber operations, AI is yet another sign of a shift in threats, where
AI-Driven Threat Detection
AI as a threat detection mechanism is a revolution in cybersecurity as it involves use of algorithms to detect and prevent cyber threats with incredible efficiency and accuracy. Foremost traditional systems for threat detection utilize predefined patterns or formulas of identified threats, such that the systems are powerless in front of unique threats[4]. On the other hand, AI systems apply machine learning approaches that help in analysing large amount of data in real time to help detect unusual behaviours that may depict a possible hackers’ attack. These systems are designed to enhance their capability to learn from previous mishaps thus enhancing the identification of such systems. In AI threat detection, through constant network traffic, user behaviour, and system activity analysis, threats are detected as they occur and not when they fully evolve and portray major threats hence improving on the cybersecurity. It not only improves the general security of an organization but also slightly decreases the burden of human analysts’ work, letting them work on more essential activities.
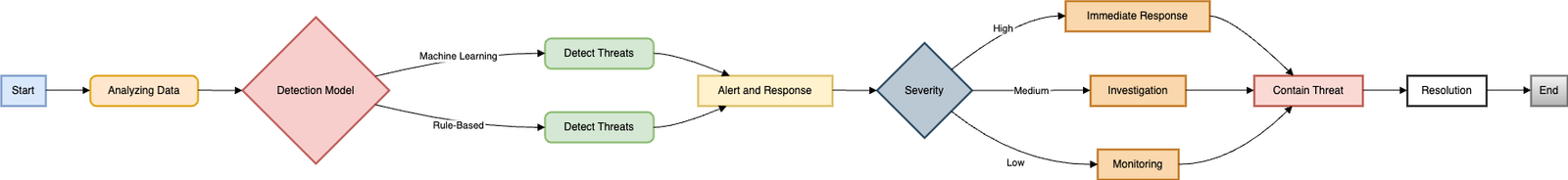
Automated Response Mechanisms
Automated response mechanisms powered by AI are revolutionizing the way organizations handle cyber threats, offering a swift and efficient means of neutralizing attacks. Traditionally, responding to cyber incidents required human intervention, which could delay critical actions, allowing threats to proliferate and cause more damage. With AI-driven automation, once a threat is detected, the system can immediately initiate pre-defined responses, such as isolating compromised systems, blocking malicious IP addresses, or deploying patches to vulnerable software[5]. These automated actions are crucial in mitigating the impact of attacks, particularly in large and complex networks where manual responses might be too slow to prevent escalation. Additionally, automation reduces the risk of human error in crisis situations, ensuring a consistent and effective defence. While automated response mechanisms greatly enhance cybersecurity operations, they must be carefully configured and monitored to avoid unintended disruptions or overreactions, highlighting the need for a balance between automation and human oversight.[6]
Conclusion
The incorporation of Artificial Intelligence in cybersecurity enhances this long-standing struggle against cyber criminals. Integrated systems like threats detectors and automation of responses have enhanced the rate of detecting and responding to more elaborative attacks hence increasing the speed of security’s performance. With AI’s use of machine learning and predictive analytical tools not only does it fortify the possibility of threat identification in real-time but it changes the entire cybersecurity tactic from ‘firefighting,’ or simply responding to breaches as they occur, to actually preventing them before they occur. However, this has also brought about other problems – ethical issues apart from the fact that AI can be employed on the wrong side that is in the cyber-attacks. When it comes to using the primary drivers of the future for cybersecurity, people should be ready for advances in AI and able to respond adequately, so that technologies are used only for good purposes, and not vice versa. It is only when one examines AI’s strengths and weaknesses as an instrument in the sphere of cyberspace that one can safely unlock the opportunities characteristic of said technology, all the while steering through the ethically fraught terrain of such possibilities. Cybersecurity of the future will be a subject of integrating new technological solutions in the context of protecting human values.
References
- K. T. Putra, A. Z. Arrayyan, R. Z. Syahputra, Y. A. Pamungkas, and M. Rahaman, “Design a Two-Axis Sensorless Solar Tracker Based on Real Time Clock Using MicroPython,” Emerg. Inf. Sci. Technol., vol. 4, no. 1, Art. no. 1, May 2023, doi: 10.18196/eist.v4i1.18697.
- K. Helkala, J. Cook, G. Lucas, F. Pasquale, G. Reichberg, and H. Syse, “AI in Cyber Operations: Ethical and Legal Considerations for End-Users,” in Artificial Intelligence and Cybersecurity: Theory and Applications, T. Sipola, T. Kokkonen, and M. Karjalainen, Eds., Cham: Springer International Publishing, 2023, pp. 185–206. doi: 10.1007/978-3-031-15030-2_9.
- T. Eze, ECCWS 2022 21st European Conference on Cyber Warfare and Security. Academic Conferences and publishing limited, 2022.
- A. Yaseen, “AI-DRIVEN THREAT DETECTION AND RESPONSE: A PARADIGM SHIFT IN CYBERSECURITY Asad Yaseen,” Dec. 2023.
- T. Toth and C. Kruegel, “Evaluating the impact of automated intrusion response mechanisms,” in 18th Annual Computer Security Applications Conference, 2002. Proceedings., Dec. 2002, pp. 301–310. doi: 10.1109/CSAC.2002.1176302.
- B. D. Alfia, A. Asroni, S. Riyadi, and M. Rahaman, “Development of Desktop-Based Employee Payroll: A Case Study on PT. Bio Pilar Utama,” Emerg. Inf. Sci. Technol., vol. 4, no. 2, Art. no. 2, Dec. 2023, doi: 10.18196/eist.v4i2.20732.
- Gupta, B. B., Gaurav, A., & Panigrahi, P. K. (2023). Analysis of retail sector research evolution and trends during COVID-19. Technological Forecasting and Social Change, 194, 122671.
- Aldweesh, A., Alauthman, M., Al Khaldy, M., Ishtaiwi, A., Al-Qerem, A., Almoman, A., & Gupta, B. B. (2023). The meta-fusion: A cloud-integrated study on blockchain technology enabling secure and efficient virtual worlds. International Journal of Cloud Applications and Computing (IJCAC), 13(1), 1-24.
- M. Casillo, F. Colace, B. B. Gupta, A. Lorusso, F. Marongiu and D. Santaniello, “Blockchain and NFT: a novel approach to support BIM and Architectural Design,” 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakheer, Bahrain, 2022, pp. 616-620, doi: 10.1109/3ICT56508.2022.9990815.
Cite As
Reddy D.R.C (2024) AI and Cybersecurity: What Everyone Should Know, Insights2Techinfo, pp.1