By: Himanshu Tiwari, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, nomails1337@gmail.com
A strong and adaptable Linux firewall program, iptables, is examined in this research study. By filtering and managing network traffic, iptables protects the network perimeter. Iptables’ architecture, functions, and uses are covered in this article. We examine its skills in packet filtering, Network Address Translation (NAT), and connection tracing to protect systems from illegal access and cyberattacks.
1. Intro
As cyber dangers develop, network security must be strong. iptables, a user-space utility software that lets system administrators define Linux kernel firewall IP packet filter rules, guards the network boundary. This section discusses iptables and its importance in cybersecurity[1].
2. iptables Architecture
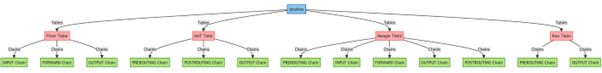
This section analyzes the iptables architecture and its main components. Tables, chains, and rules are discussed to explain how iptables handles packets hierarchically. A diagram of the iptables architecture will be included[2].
Iptables is made up of tables, chains, and rules. Tables organize chains, which are lists of packet-handling rules. Understanding this architecture is essential for configuring iptables for security.
The primary tables in iptables are:
– Filter table: Responsible for packet filtering.
– NAT table: Manages Network Address Translation.
– Mangle table: Alters packet header information.
– Raw table: Bypasses connection tracking.
3. Packet Filtering with iptables

Iptables’ packet filtering lets administrators set rules for incoming and outgoing network packets. This section discusses iptables rule syntax, packet matching criteria, and rule-based actions[3].
Iptables rules provide criteria, targets, and optional matches. Criteria determine when a rule applies, whereas targets dictate what happens when it does. Matching conditions refine rule applicability[4].
Real-world examples:
1. Allow SSH Access:
| iptables -A INPUT -p tcp –dport 22 -j ACCEPT |
2. Block Incoming HTTP Traffic:
| iptables -A INPUT -p tcp –dport 80 -j DROP |
4. Network Address Translation (NAT) using iptables
Iptables’ Network Address Translation (NAT) capabilities are crucial for mapping private IP addresses to public ones, facilitating the efficient use of limited IPv4 addresses. This section elucidates how iptables can be employed for NAT, covering techniques such as source NAT (SNAT) and destination NAT (DNAT)[5].
Practical examples:
1. SNAT (Source NAT):
| iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth0 -j SNAT –to-source <public_ip> |
2. DNAT (Destination NAT):
| iptables -t nat -A PREROUTING -i eth0 -p tcp –dport 80 -j DNAT –to-destination <private_ip>:80 |
5. Connection Tracking
Iptables tracks active network connections to retain state. Connection tracking allows the firewall to decide whether to allow or refuse packets based on their relationship to existing connections, improving security[6].
Connection tracking helps iptables recognize existing connections, preventing illegal access and improving network security.
6. Practical Applications
To provide a real-world perspective, this section presents diverse applications of iptables in securing Linux systems. Examples include setting up a basic firewall, creating rules for specific services, and implementing port forwarding.
Advanced use cases:
1. Intrusion Detection and Prevention:
Utilizing iptables in conjunction with tools like Snort for intrusion detection and prevention.
| iptables -A INPUT -p tcp –dport 22 -m recent –update –seconds 60 –hitcount 4 -j LOG –log-prefix “SSH Brute Force” iptables -A INPUT -p tcp –dport 22 -m recent –set -j ACCEPT |
7. Challenges and Considerations
Although robust, iptables has its drawbacks. This section discusses iptables deployment difficulties such rule order, specificity, and performance.
Considerations:
1. Rule Order:
The order of rules in iptables is crucial, as rules are processed sequentially. Careful consideration must be given to rule placement to avoid unintended consequences.
2. Performance Impacts:
Extensive rule sets and complex configurations can impact system performance. Regular optimization and monitoring are essential for maintaining optimal firewall performance.
8. Conclusion
In conclusion, this research study examines iptables’ architecture, functions, and network security applications. Iptables, a Linux administrator’s essential utility, protects systems from growing cyberthreats. Building resilient and secure network perimeters requires understanding its complexities.
References
- Purdy GN. Linux iptables Pocket Reference: Firewalls, NAT & Accounting. ” O’Reilly Media, Inc.”; 2004 Aug 25.
- Miano S, Bertrone M, Risso F, Bernal MV, Lu Y, Pi J. Securing Linux with a faster and scalable iptables. ACM SIGCOMM Computer Communication Review. 2019 Nov 8;49(3):2-17.
- Hoffman D, Prabhakar D, Strooper P. Testing iptables. InProceedings of the 2003 conference of the Centre for Advanced Studies on Collaborative research 2003 Oct 6 (pp. 80-91).
- Bertrone M, Miano S, Risso F, Tumolo M. Accelerating linux security with ebpf iptables. InProceedings of the ACM SIGCOMM 2018 Conference on Posters and Demos 2018 Aug 7 (pp. 108-110).
- Šimon M, Huraj L, Čerňanský M. Performance evaluations of IPTables firewall solutions under DDoS attacks. Journal of Applied Mathematics, Statistics and Informatics. 2015;11(2):35-45.
- Diekmann C, Michaelis J, Haslbeck M, Carle G. Verified iptables firewall analysis. In2016 IFIP Networking Conference (IFIP Networking) and Workshops 2016 May 17 (pp. 252-260). IEEE.
- Kumar, A., Shankar, A., Behl, A., Arya, V., & Gupta, N. (2023). Should I share it? Factors influencing fake news-sharing behaviour: A behavioural reasoning theory perspective. Technological Forecasting and Social Change, 193, 122647.
- Sharma, A., Singh, S. K., Badwal, E., Kumar, S., Gupta, B. B., Arya, V., … & Santaniello, D. (2023, January). Fuzzy Based Clustering of Consumers’ Big Data in Industrial Applications. In 2023 IEEE International Conference on Consumer Electronics (ICCE) (pp. 01-03). IEEE.
- Zhou, Y., Song, L., Liu, Y., Vijayakumar, P., Gupta, B. B., Alhalabi, W., & Alsharif, H. (2023). A privacy-preserving logistic regression-based diagnosis scheme for digital healthcare. Future Generation Computer Systems, 144, 63-73.
- Sharma, A., Singh, S. K., Badwal, E., Kumar, S., Gupta, B. B., Arya, V., … & Santaniello, D. (2023, January). Fuzzy Based Clustering of Consumers’ Big Data in Industrial Applications. In 2023 IEEE International Conference on Consumer Electronics (ICCE) (pp. 01-03). IEEE.
Cite As
Tiwari H. (2023) An In-Depth Analysis of iptables: Security at the Network Perimeter, Insights2Techinfo, pp.1