By: 1Ankita Sharma & 2Mohd. Ashad
1,2 Chandigarh College of Engineering and Technology (Degree Wing), Chandigarh, India
Abstract:
Command-and-Control (C2) servers play a critical role in modern threat scenarios, serving as the communication hub between attackers and compromised systems. Analyzing C2 servers is essential for understanding cyber threats, identifying malicious activity, and devising effective defense strategies. This article examines the crucial function of command-and-control (C&C) servers in modern cybersecurity. It describes the critical roles of these servers as major centers for coordinating harmful operations, stressing their growth from basic, well-known vulnerability exploitation to complex, decentralized, and adaptive systems. C&C servers provide remote control, data collection, virus dissemination, and coordinated assaults, highlighting their importance in current threat scenarios. The report emphasizes the increasing complexity of cyber threats, which is supported by C&C server developments that elude detection, use AI, and exploit decentralized communication. Furthermore, it digs into state-sponsored assaults and sophisticated persistent threats, demonstrating the stealth and complexity inherent in C&C server operations.
KEYWORDS: Cybersecurity, Command-and-Control Servers, Malicious Actors, Cyber Threats, Cybersecurity Landscape.
- INTRODUCTION
In today’s rapidly evolving cybersecurity landscape, the analysis of Command-and-Control (C2) servers stands as a cornerstone in understanding, detecting, and mitigating modern threat scenarios. In the ever-changing cybersecurity world, understanding the complexities of command-and-control servers is critical. In the domain of cybersecurity, Command and Control (C&C) servers play a pivotal role in understanding and executing malicious activities [1]. These servers serve as centralized command hubs through which cybercriminals remotely control compromised devices or networks, known as botnets. Facilitating activities such as data exfiltration, remote control, and coordinated attacks C&C servers’ function similarly to organized cyber operations. As cyber threats become more complicated and sophisticated, so do C&C servers, which use evasion strategies such as encryption and decentralized communication channels to avoid detection [5]. The rise of state-sponsored cyberattacks and sophisticated persistent threats emphasizes the importance of command and control servers in modern cyber warfare.
In today’s digital age, cybersecurity is critical to protect important digital assets. Software engineers play a critical role in understanding and implementing strong cybersecurity solutions to protect software systems from a wide range of attacks. Cybersecurity refers to a set of strategies and instruments designed to fight hostile actions, prevent unauthorized access, and mitigate data breaches. Firewalls, safe coding approaches, encryption, and regular security audits are essential components for assuring the confidentiality, integrity, and availability of sensitive data.
- Servers for Command and Control:
A Command-and-Control (C&C) server is an important component within the realm of cyber threats, serving as the nerve center of malicious operations arranged by cybercriminals. At its core, a C&C server acts as a centralized hub that facilitates communication and control over a network of compromised devices, commonly referred to as a botnet. The primary purpose of a C&C server is to manage, command, and coordinate the activities of these compromised devices in a synchronized and often malicious manner [2] which is depicted in Figure 1.
The role of a C&C server can be likened to that of a conductor leading an orchestra, directing each instrument (compromised device) to play its part in harmony, albeit with nefarious intent. Here are key aspects of the definition:
Communication Hub: A C&C server acts as the main communication point between the malicious actor (often referred to as the controller or operator) and the compromised devices within the botnet. It provides a secure and covert channel through which commands and instructions are transmitted [10].
Control and Coordination: The primary function of a C&C server is to exercise control over the compromised devices, dictating their actions and orchestrating them to perform specific tasks. This could include launching attacks, stealing sensitive data, or participating in a coordinated assault on a target.
Botnet Management: A C&C server is instrumental in managing the botnet, ensuring its operational efficiency [9]. This involves tasks such as updating malware on compromised devices, adding or removing bots from the network, and maintaining persistence to evade detection and removal.
Issuing Commands: The C&C server issues commands to the compromised devices, specifying the actions they should take. These commands can be diverse, ranging from simple tasks like sending spam emails to more sophisticated activities like participating in a distributed denial-of-service (DDoS) attack.
Data Exfiltration: In addition to issuing commands, a C&C server often serves as the conduit for data exfiltration. It facilitates the transfer of stolen information from the compromised devices to a location controlled by the cybercriminal.
Emphasizing the ability of a C&C server to control and coordinate compromised devices in a botnet underscores its critical role in enabling cyber threats to scale and execute attacks with greater impact. The covert nature of C&C communication and the centralized control it provides make these servers a key focus in cybersecurity efforts, necessitating robust detection, prevention, and mitigation strategies to counter their malicious activities.
- Participation of C&C in planning of cyberattacks
The Command and Control (C&C) [8] servers serve as a central command center for malicious actions, which is a crucial part in creating cyber threats. Among its primary duties are:
Remote Control: Threat actors can remotely take control of hacked networks or devices thanks to C&C servers. This enables them to perform a variety of nefarious tasks without having direct physical access, including executing commands and manipulating systems.
Communication: Attackers and compromised computers can communicate with each other using C&C servers. They make it easier for the threat actor and the compromised devices to share instructions, updates, and data—often discreetly and encrypted.
Malware Deployment: C&C servers play a key role in the distribution and control of malware throughout a hacked device network [14]. To adjust to changing security protocols, they can disseminate updates, modify their attack methods, or introduce new dangerous payloads [6].
Data Exfiltration: In order to extract sensitive data from infiltrated networks, C&C servers are essential. They make it easier for data to be transferred illegally back to the attackers, including login credentials, intellectual property, and personal information.
Coordination of Attacks: C&C servers are used to orchestrate attacks on several fronts when faced with more complex cyber threats. This could entail coordinated efforts on several targets in order to accomplish a certain goal, such interfering with services or pilfering confidential information [2].
- The Cyber Threat Evolution:
Technology breakthroughs and malevolent actors have interacted dynamically to shape the evolution of cyber dangers. With the quick advancement of technology over the years, the sophistication of cyber threats has also increased, especially in the area of Command-and-Control (C&C) servers [12]. Comprehending this development is essential to realizing the increasing complexity of contemporary cybersecurity threats and emphasizes the need for a thorough examination of C&C servers [8].
Early cyberattacks were frequently quite straightforward and concentrated on taking advantage of weaknesses that were already known [15]. The main focus of malicious actors was on specific systems, and their strategies were frequently simple and opportunistic. But just as technology developed, so did cybercriminals’ tactics and tools[9]. The development of the internet and the spread of networked devices opened the door for increasingly intelligent and well-planned cyberattacks[16]. As the brains behind these attacks, C&C servers have developed into extremely versatile and robust systems [9]. To make discovery and attribution more difficult, attackers started using decentralized systems, encryption, and obfuscation techniques. An important change was the emergence of botnets, which are vast networks of infected devices under the direction of a C&C server. Attackers were able to plan massive operations, such distributed denial-of-service (DDoS) campaigns, with previously unheard-of scope and impact thanks to these botnets. The use of malware that can dynamically alter its code to avoid detection—known as polymorphic malware—further demonstrated the increasing intricacy of C&C server operations. the integration of hardware-supported security measures underscores the multidimensional approach required to combat emerging cyber threats effectively [15].
As shown in Figure 1, for a C&C attack to take place, a malicious remote server known as a C&C server must get access to an already infected machine. Most devices, including laptops, desktop computers, tablets, smartphones, and Internet of Things devices, are susceptible to this type of attack.
Command-and-control server attacks frequently occur using the following channels:
- Phishing emails try to trick users into opening hazardous links or attachments.
- Malvertising is the technique of spreading malware by embedding harmful code in digital advertisements.
- Vulnerable browser extensions and plugins can inject malicious scripts into interactive webpages, diverting, blocking, and stealing data submitted into online forms.
- Malware that is installed directly on a device and performs destructive actions.
After successfully infiltrating a device, a threat actor communicates with the malicious C&C server to relay instructions to the infected host and build a malicious network. A botnet is a malicious network that is controlled by a C&C server, and the network nodes that make up the botnet are also known as zombies. Beaconing can also be used to send instructions or additional payloads from the infected device to the C&C server. Peer-to-peer (P2P) networks and other advancements in communication protocols allowed C&C servers to function in a more decentralized way, making it challenging for cybersecurity experts to locate and neutralize them.
Once the infected host begins executing the orders given by the C&C server, more malware is installed, giving the threat actor complete control over the compromised machine. To escape detection by firewalls, threat actors may attempt to combine C&C traffic with other types of normal traffic, such as HTTP.
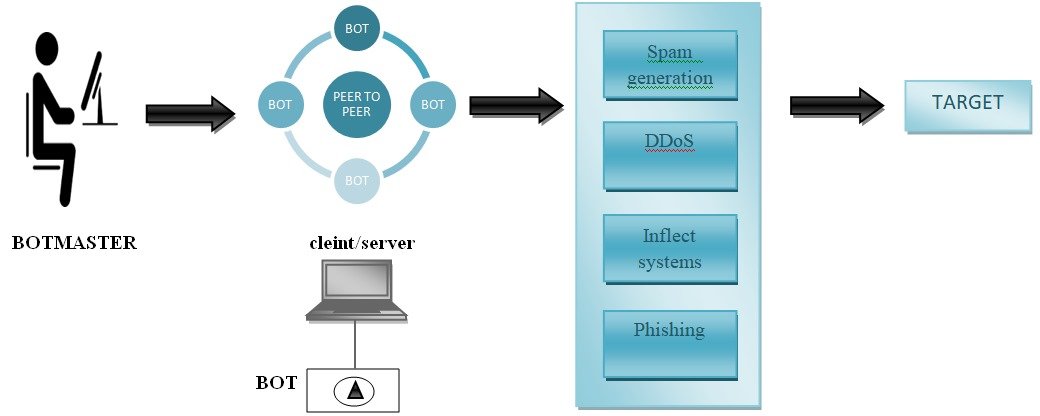
Inflect systems
COMMAND AND CONTROL MALICIOUS
NETWORKS ACTIVITIES
FIGURE 1: BOTNET COMMAND AND CONTROL ARCHITECTURE
Cybersecurity measures gained additional sophistication with the use of artificial intelligence and machine learning, while C&C servers modified their strategies to instantly exploit holes.
The frequency of nation-state-sponsored cyberattacks is rising, which further enhances C&C servers’ capabilities. Advanced persistent threats (APTs) were created by state-sponsored entities and were typified by sophisticated C&C infrastructure, stealthy operations, and long-term objectives. These attacks aimed at espionage, data theft, and disruption of critical infrastructure demonstrated the need for a deeper understanding of the intricacies of C&C server functionality [11].
- The C&C server’s functionality and purpose
- Issue of Commands:
- Centralized Control: Hackers can transmit commands to the hacked devices in a botnet by using C&C servers, which function as a central command center. Coordinated activities over a vast network of compromised computers require this centralized control [5].
- Real-time Commands: C&C servers make it possible to issue commands in real-time, which allows hackers to modify their tactics on the go. Commands can be used for a variety of functions, from straightforward ones like upgrading malware or switching up attack vectors to more intricate ones like reconnaissance or moving laterally within a network [4].
- Data Infiltration and Reception:
- Gathering of Data: C&C servers act as a central location for gathering information from infected devices. Sensitive data, login passwords, private information, and any other information important to the attacker.
- Data Exfiltration: Once collected, the C&C server facilitates the exfiltration of stolen data to a location controlled by the attacker. This process often occurs covertly, making it challenging for security systems to detect and block the unauthorized transfer of information [5].
- Botnet Management:
- Updating and Maintaining: By updating the malware on compromised devices, C&C servers take care of the botnet [3]. This guarantees that the malicious program will continue to function and be able to withstand security measures.
- Adding or Removing Bots: By adding new infected devices or deleting old ones, hackers can change the botnet’s composition. The size and capabilities of the botnet can be dynamically altered thanks to its versatility.
- Launching Coordinated Attacks:
- Distributed Denial-of-Service (DDoS) attacks: DDoS attacks, in which a large number of hacked devices bombard a target system with traffic, overloading its capacity and rendering it unusable, are commonly launched using C&C servers [6].
- Coordinated Attacks: In addition to DDoS attacks, C&C servers enable coordinated attacks against specific targets. This could entail breaking into networks, taking advantage of weaknesses, or executing other malicious actions for financial gain, political motives, or espionage.
CONCLUSION
Finally, this article discusses the importance of command-and-control (C&C) servers in shaping today’s cybersecurity landscape. As hostile actors adapt to technology improvements, command and control servers have developed from simple vulnerability exploitation to complex, decentralized, and adaptable systems. C&C servers’ multiple functionalities, which include remote control, data collection, virus dissemination, and coordinated attacks, highlight their critical position in modern threat scenarios[7].
The report highlights the growing complexity of cyber threats, with C&C server developments evading detection via encryption, obfuscation, and AI integration[8]. State-sponsored assaults and advanced persistent threats (APTs) highlight the stealth and sophistication of C&C server operations. As nation-state-sponsored cyberattacks become more common, the capabilities of command and control servers improve, stressing the importance of a thorough understanding of their functions. The investigation of command and control servers indicates botnet orchestration, involvement in cyberattack planning, and contribution to the evolution of cyber threats. The study emphasizes the centralization of control, real-time command issuing, data invasion, botnet administration, and participation in launching coordinated attacks as critical features of C&C servers. When navigating the cybersecurity landscape, it is critical to realize the critical role of command and control servers and establish strong detection, prevention, and mitigation methods[3].
As technology and cyber risks evolve in tandem, companies must prioritize a proactive awareness of C&C server operations to protect digital assets from more complex cyber threats[12]. This report lays the groundwork for informed cybersecurity strategies, highlighting the need of staying ahead in the continuing fight against evolving cyber threats.
REFERENCES
- G Mengi, SK Singh, S Kumar, D Mahto, A Sharma (2023) .Automated Machine Learning (AutoML): The Future of Computational Intelligence. International Conference on Cyber Security, Privacy and Networking (ICSPN 2022) (309-317).
- K Aggarwal, SK Singh, M Chopra, S Kumar, F Colace(2022). Deep Learning in Robotics for Strengthening Industry 4.0.: Opportunities, Challenges and Future Directions. Robotics and AI for Cybersecurity and Critical Infrastructure in Smart Cities (1-19).
- M Singh, SK Singh, S Kumar, U Madan, T Maan(2023). Sustainable Framework for Metaverse Security and Privacy: Opportunities and Challenges. International Conference on Cyber Security, Privacy and Networking (ICSPN 2022) (329-340).
- A Sharma, SK Singh, S Kumar, A Chhabra, S Gupta(2023). Security of Android Banking Mobile Apps: Challenges and Opportunities. International Conference on Cyber Security, Privacy and Networking (ICSPN 2022) (406-416)
- T A l George Theodorakopoulos,P Reinecke,A Javed and E Anthi (2023).Abuse of Cloud-Based and Public Legitimate Services as Command-and-Control (C&C) Infrastructure: A Systematic Literature Review. J. Cybersecur. Priv. 2023, 3(3), 558-590; https://doi.org/10.3390/jcp3030027
- J Koo, SR Oh, SH Lee, YG Kim (2020) Security architecture for cloud-based command and control system in IoT environment . Appl. Sci. 2020, 10(3), 1035; https://doi.org/10.3390/app10031035
- Yury Zhauniarovich et al. (July 2018). “A Survey on MaliciousDomains Detection through DNS Data Analysis”. In:ACM Comput. Surv. 51.4 ISSN: 0360-0300.DOI: 10.1145/3191329. URL: https://doi.org/10.1145/3191329.
- G. Vormayr, T. Zseby, and J. Fabini. (September 2017), “Botnet Communication Patterns”. In: IEEE Communications Surveys Tutorials 19.4 pp. 2768–2796. ISSN: 1553-877X. DOI: 10.1109/COMST.2017.2749442. URL: https://doi.org/10.1109/COMST.2017.2749442
- A Rana, S Gupta, B Gupta – International Conference on Cybersecurity …, 2022 A Dual Attack Tree Approach to Assist Command and Control Server Analysis of the Red Teaming Activity
- Andrew John Poulter and Simon J.(2021) Cox Enabling Secure Guest Access for Command-and-Control of Internet of Things Devices IoT 2021, 2(2), 236-248; https://doi.org/10.3390/iot2020013
- AJ Poulter, SJ Cox (2021)Enabling Secure Guest Access for Command-and-Control of Internet of Things Devices . IoT 2021, 2(2), 236-248; https://doi.org/10.3390/iot2020013
- The CTU-13 Dataset.(2020) A Labeled Dataset with Botnet, Normal and Background traffic. — Stratosphere IPS. URL: https://www. stratosphereips. org/ datasets – ctu13 APPENDIX A
- C. E. Shannon.(1999) “A mathematical theory of communication”. In: The Bell System Technical Journal 27.3 pp. 379–423. ISSN: 0005-8580. DOI: 10.1002/j.1538-7305.1948.tb01338.x.
- Kaur, P., Singh, S. K., Singh, I., & Kumar, S. (2021, December). Exploring Convolutional Neural Network in Computer Vision-based Image Classification. In International Conference on Smart Systems and Advanced Computing (Syscom-2021).
- Kumar, S., Singh, S. K., Aggarwal, N., Gupta, B. B., Alhalabi, W., & Band, S. S. (2022). An efficient hardware supported and parallelization architecture for intelligent systems to overcome speculative overheads. International Journal of Intelligent Systems, 37(12), 11764-11790.
- Peñalvo, F. J. G., Sharma, A., Chhabra, A., Singh, S. K., Kumar, S., Arya, V., & Gaurav, A. (2022). Mobile cloud computing and sustainable development: Opportunities, challenges, and future directions. International Journal of Cloud Applications and Computing (IJCAC), 12(1), 1-20.
- Alhalabi, W., Gaurav, A., Arya, V., Zamzami, I. F., & Aboalela, R. A. (2023). Machine learning-based distributed denial of services (DDoS) attack detection in intelligent information systems. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-17.
- Lin, C. Y., Rahaman, M., Moslehpour, M., Chattopadhyay, S., & Arya, V. (2023). Web semantic-based MOOP algorithm for facilitating allocation problems in the supply chain domain. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-23.
- Li, Q., Li, X., Chui, K. T., & Arya, V. (2023). Exploring the Intersection of Athletic Psychology and Emerging Technologies. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-15.
- Sun, N., Li, J., Liu, Y., & Arya, V. (2023). A Scalable Sharding Protocol Based on Cross-Shard Dynamic Transaction Confirmation for Alliance Chain in Intelligent Systems. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-30.
- Zhang, T., Zhang, Z., Zhao, K., Gupta, B. B., & Arya, V. (2023). A Lightweight Cross-Domain Authentication Protocol for Trusted Access to Industrial Internet. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-25.
Cite As
Sharma A; Mohd. Ashad (2024) Analysis of Command-and-Control Servers in Modern Threat Scenarios, Insighs2Techinfo, pp.1