By: Afeeza Ali and Surya Prakash
Modern user fingerprint authentication and verification systems have revolutionized ever since the use of biological properties of individuals became a part of identity management systems. The usage of intrinsic physiological or behavioural characteristics relieves an individual of remembering cumbersome passwords or tokens. Additionally, the usage of biometrics has rendered the duplication of the identity of a user more difficult than it was ever before. Although the involvement of biometric information has provided immense ease of use and effectiveness, their mismanagement and inefficient deployment may potentially cause permanent non-usability of an individual’s biometrics. Therefore, non-repudiation and the unique nature of biological features have made it imperative to ensure absolute resistance to being compromised. Consequently, although there have been various studies to propose techniques that improve recognition performance and strengthen the security of original biometric data, there exist a number of challenges that are currently under the scope of research.
Fingerprint authentication, face, iris and retina, keystroke dynamics, voice recognition, etc. are a few of the most prominently used biometrics for various applications worldwide. Among these, fingerprint biometric is the most popular means of user verification employed across popular biometric security applications including forensics, e-commerce, citizens’ registration applications used by governments, border control, etc. Fingerprint-based identification systems are largely used owing to the innate ease in collection and availability of multiple sources (10 fingers) for acquisition.
Fingerprints and Minutiae points
Patterns made by a collection of high peaking lines (ridges) and the space between these lines appearing as low shallow portions (valleys) on the surface of a fingertip represent a fingerprint. Ridge ending and ridge bifurcation are two of the most important minutia features of ridges. A ridge ending is a location where a singular ridge discontinues abruptly. A ridge bifurcation is a location where two ridges unite to form a single continuous ridge. Distinctive discontinuities in the ridge lines such as these are known as minutiae points. Fingerprint identification relies primarily on these minutiae points.
A fingerprint can be reconstructed if there is a leakage of precise information of minutiae points. This leads to the idea of securing raw fingerprint data by designing a one-way transformation of original minutiae points [1] so that a possible compromise of the database can be mitigated by a reissuance of the accorded template. This is the key idea behind one of the most popular means of biometric template protection i.e., cancellable biometrics [2] which employ the following steps.
- A digital image of a fingerprint is obtained at the sensor end and appropriate techniques are applied to extract the minutiae points.
- Unique, discriminatory features are computed from the minutiae points [3] that form a unique fingerprint template corresponding to its original biometric data.
- The template generated is irreversibly transformed in a manner that any degradation suffered does not affect the matching process adversely. This secure template is safely stored in the database.
- A probe template is transformed similarly and is matched (in the transformed domain) with the previously stored templates to validate the ingenuity.
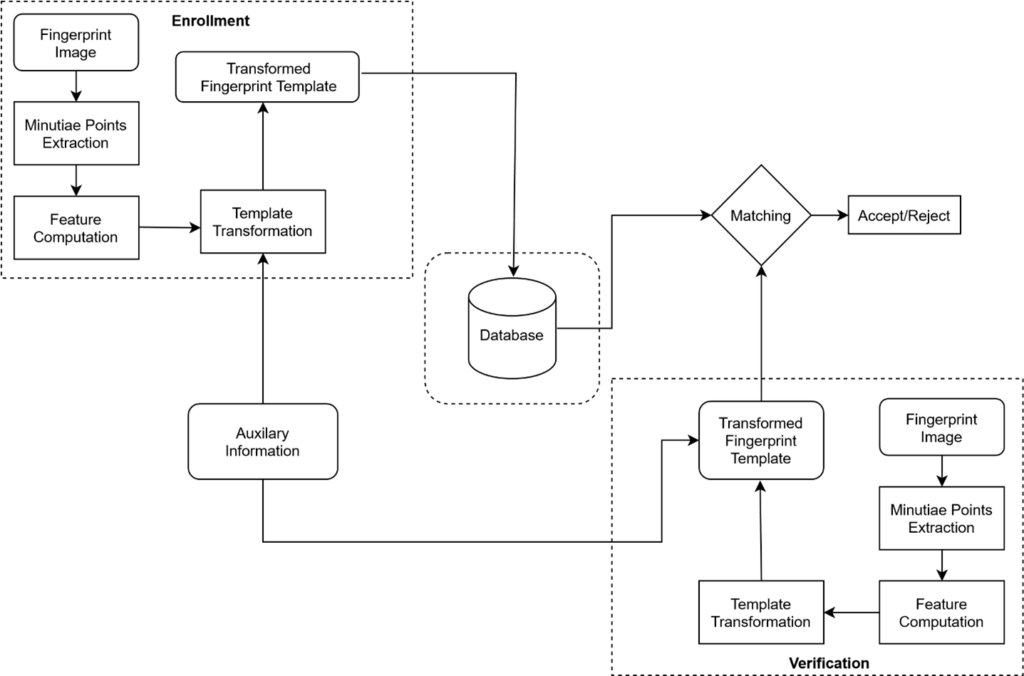
Several fingerprint template protection schemes such as [4], [5], among others have been proposed recently that incorporate the above-mentioned procedures to offer solutions to various new challenges faced in the scope of fingerprint biometrics [6].
Open challenges in fingerprint authentication:
Although fingerprints have remained dominant among biometric-based authentication systems in terms of convenience and low error rates, a steady increase in their deployment across various environments presents new challenges.
The first and most critical step in automated fingerprint authentication technologies is the acquisition of raw data. The quality of the fingerprint image substantially affects the overall system performance [7]. However, the acquisition of precise quality impressions is a challenging job owing to physical distortions and translation/rotation while capturing the digital image of a fingerprint. Low quality, partial/arch type fingerprints still need to be worked on to ensure that the system manages to perform satisfactorily.
The possibility of fingerprint reconstruction from the information of minutiae negates the feasibility of storing raw minutiae points as a biometric template [8], [9]. Consequently, several biometric protection schemes put forth ways to replace the biometric data by applying a suitable transformation that is unique to a user without affecting the recognition performance. Nonetheless, it is still a challenging job among the biometric research community to fully quantize the information obtained from original data and produce an absolutely irreversible template that doesn’t give away any information of the original minutiae points it was constructed from. It is a significant threat to the user identity if template non-invertibility is unmet.
Rampant use of biometrics in multifaceted applications has increased the risk of identity theft significantly. The past decade has seen a surge in malicious attempts of identity fraud by forging biometrics. For instance, dummy fingerprints constructed using gelatine, clay, and silicone molds are common means of spoof attacks by identity forgers to fabricate fingerprints [10]. Existing spoof detection methods suffer from a bottleneck of dealing with low accuracy rates.
As a result, designing an algorithm that encompasses all the discussed challenges and more arguably stands as the biggest challenge among researchers studying human independent recognition systems.
Scope of future research for fingerprint authentication
Increasing penetration of fingerprint technology for high-security transactions in the market opens up the scope of research in the area that needs renewed attention to the recent challenges. Following are some of the buzzing areas that need research attention:
- Design of anti-spoof algorithms that detect fingerprint forgery or any other presentation attacks along with ensuring low error rate in recognition.
- Incorporating image processing techniques that offer enhanced image quality to facilitate high-quality feature extraction. This can help handle partial/arch type, low-quality input images.
- Design of rotation/translation invariant and alignment-free feature extraction algorithms.
- Design of techniques that employ many-to-one feature mapping to ensure non-invertibility of stored templates.
- Development of algorithms that fully quantize raw templates to allow perfect distortion of minutiae distribution and yet retain the discriminative property.
- Development of secure non-invertible template generation techniques with lesser computation cost and higher performance.
References:
[1] Baghel Vivek Singh, Syed Sadaf Ali, and Surya Prakash. “A non‐invertible transformation-based technique to protect a fingerprint template.” IET Image Processing, 2021. DOI: https://doi.org/10.1049/ipr2.12130
[2] Sandhya, Mulagala, and Munaga VNK Prasad. “Biometric template protection: A systematic literature review of approaches and modalities. Biometric Security and Privacy, pp. 323-370, 2017.
[3] Ali, Syed Sadaf, Iyyakutti Iyappan Ganapathi, and Surya Prakash. “Robust technique for fingerprint template protection.” IET Biometrics, 7(6), pp. 536-549, 2018.
[4] Ali, Syed Sadaf, and Surya Prakash. “3-Dimensional secured fingerprint shell.” Pattern Recognition Letters, 126, pp. 68-77, 2019.
[5] Ali, Syed Sadaf, Iyyakuti Iyappan Ganapathi, and Surya Prakash. “Fingerprint Shell with impregnable features.” Journal of Intelligent & Fuzzy Systems 36(5), pp 4091-4104, 2019.
[6] Jain, Anil K., Karthik Nandakumar, and Abhishek Nagar. “Fingerprint template protection: From theory to practice.” Security and privacy in Biometrics. Springer, London, pp. 187-214, 2013.
[7] Win, Zin Mar, and Myint Myint Sein. “Texture feature-based fingerprint recognition for low quality images.” 2011 International Symposium on Micro-Nano Mechatronics and Human Science, IEEE, 2011.
[8] Cappelli, Raffaele, et al. “Fingerprint image reconstruction from standard templates.” IEEE transactions on pattern analysis and machine intelligence, 29(9), pp. 1489-1503, 2007.
[9] Feng, Jianjiang, and Anil K. Jain. “Fingerprint reconstruction: from minutiae to phase.” IEEE transactions on pattern analysis and machine intelligence, 33(2), pp. 209-223, 2010.
[10] Uliyan, Diaa M., Somayeh Sadeghi, and Hamid A. Jalab. ‘Anti-spoofing method for fingerprint recognition using patch based deep learning machine.’ Engineering Science and Technology, an International Journal, 23(2), pp. 264-273, 2020.
Cite this article:
Afeeza Ali and Surya Prakash (2021) Biometric Fingerprint Authentication: Challenges and Future Research Directions, Insights2Techinfo, pp1
Great article, informative and well written.
Thank you
Good and informative Article !!!!!
Thank you for your support
Really great article. Very insightful and well summarised. Commendable work.
Thank you
Wonderful article very insightful and informative. Well summarised commendable work.
Thank you for your appreciation
I just started exploring biometric security and found this interesting. Well written and easy to understand. Good job
Thank you
Very informative article about fingerprint authentication.
Thank you for your support