By: Gonipalli Bharath, Vel Tech University, Chennai, India & International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Online services face major threats from Distributed Denial-of-Service (DDoS) attacks that lead to operational disruptions while causing financial expenses to organizations. Many companies rely on cloud-based solutions since they adopted cloud computing technology as their main defense system against these attacks. This paper investigates whether cloud defense systems have enough power to combat DDoS threats. The article examines how DDoS attacks function along with existing defense systems while explaining cloud-based security solutions that enable organizations to remain resilient against such threats. The conclusion examines both the advantages and drawbacks of cloud security together with extra methods for comprehensive DDoS defense strategies.
Introduction:
Modern IT infrastructure has undergone a paradigm shift through cloud computing because it delivers improved security and flexibility together with convenient scalability. Enterprise operational challenges have decreased because cloud-based services provide automated threat detection systems along with managed security services to businesses. Organizations that move their services into the cloud still face continuous threats from DDoS attacks despite utilizing cloud-based migration. The sophistication and size of DDoS attacks continue to increase throughout successive years[1]. The use of AI along with botnets by attackers has rendered standard security systems ineffective since they can circumvent previous defense strategies. Organizations need to thoroughly assess how cloud-based solutions protect their infrastructure from all potential DDoS attacks[2]. This article examines how DDoS attacks work along with the position of cloud-based security and their ability to protect digital assets.
Understanding DDoS Attacks:
The malicious method of disrupting target servers through network services relies on sending excessive internet traffic to create disruptions. The usage of big computer systems known as botnets enables attackers to increase the magnitude of their attacks through the same infrastructure. Different forms of DDoS attacks exist in the following varieties:
- Volumetric Attacks: An attack target gets overwhelmed with massive traffic flooding that works to saturate its bandwidth. Attackers make use of different techniques which include UDP floods and ICMP floods together with DNS amplification attacks that produce immense responses while working with small requests to create systems-wide capacity overload[3].
- Protocol Attacks: Network protocols such as TCP/IP contain vulnerabilities that attackers exploit through protocols attacks such as SYN floods together with Ping of Death and Smurf attacks. The exploitation of connection-management vulnerabilities through these methods leads to resource depletion that results in disruption of network operations[4].
- Application-Layer Attacks: These attacks focus on specific applications rather than the entire network. These attacks bring about slowdowns or complete outages by causing application process overload using HTTP requests in web servers. It becomes complicated to identify these attacks because their traffic patterns resemble normal activities[5].
- Reflection and Amplification Attacks: Attackers take advantage of servers with public access to create traffic amplification which sends redirected traffic to their targets. DNS reflection and NTP amplification represent two reflection and amplification attack types that convert minimal queries into overwhelmed responses at the target[6].
- Multi-Vector Attacks: This multi vector attacks use multiple attack methods to fight traditional security systems which makes defense approaches very difficult to implement. Adversaries use three attack approaches which consist of volumetric and protocol and application-layer methods to circumvent standard defense systems necessitating strong new protection methods[7].
Cloud-Based DDoS Protection Mechanism:
Cloud-based security providers combat DDoS attacks by implementing different defense methods which include:
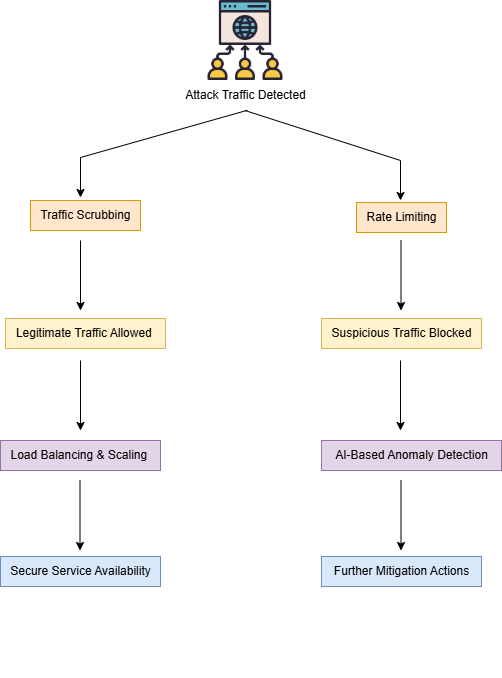
- Traffic Scrubbing: A detection system known as Traffic Scrubbing permits authentic traffic because it utilizes complex packet examination algorithms which study network patterns and traffic movements to block attacks.
- Auto- Scaling and Load Balancing: The combination of Auto-Scaling and Load Balancing allows transport of incoming traffic between several servers to maintain service availability and defend against attack effects.
- Rate Limiting and AI-Based Detection: The implementation of rate limiting systems and artificial intelligence for detection helps identify unusual behavior while stopping large numbers of harmful requests from compromised sources through artificial intelligence-based detection of new attack approaches.
- Anycast Network Firewalls: Attack traffic is distributed through Anycast Network Routing among several worldwide data centers to reduce the effect on single locations.
- Web Application Firewalls(WAFs): White Application Firewalls (WAFs) protect servers by evaluating HTTP/S traffic to stop dangerous requests through security rule implementation.
Flowchart illustrates the cloud-based DDoS mitigation mechanism:
Fig(1)
Do Cloud based Solutions are sufficient?
Cloud-based solutions contain drawbacks even though they grant strong distributed denial of service protection:
Strengths:
- Large-scale attacks receive better management from cloud providers through scattered data facilities and adaptable computing capacities.
- Cloud-based solutions rely on distributed networks to divide traffic across different servers which protects your single main server and allows continuous business operation.
- AI-powered tools through automated threat detection systems analyze network traffic while they search for doubtful activities which they respond to without delays.
- Cloud security services unite different protection mechanisms to detect threats through a combination of firewalls and intrusion detection systems while using behavioral analytics for complete defense against threats.
- Cloud security providers operate security infrastructure which enables enterprises to reduce their expenses for on-site security hardware and staff personnel maintenance.
Limitations:
- Cloud security providers control all security measures when organizations depend on them which results in organizations losing authority over response times and policy enforcement.
- Security systems controlled by Cloud providers remain exposed to new attack methods referred to as Zero-Day Exploits because these methods successfully circumvent traditional security measures.
- Traffic delays occur when traffic is re-directed to cloud-based scrubbing centers because this process creates time-based disruptions which negatively impact critical real-time applications and user experience.
- The ongoing DDoS protection from the cloud costs organizations a significant amount in fees according to their data processing needs and bandwidth utilization rates.
- The need for strict data protection regulations in certain industries creates risks when cloud security methods cannot meet requirements about data location laws and privacy standards.
Conclusion:
The protection of networks against DDoS attacks by cloud-based security systems remains essential however other defense mechanisms must also be implemented. Organizations need to execute a security strategy which merges cloud-based security together with on-premise solutions alongside AI-driven anomaly identification and threat information obtained in advance. A dual approach between cloud-based and on-site protection methods delivers organizations the best possible resistance to developing DDoS security threats. Businesses that enact a complete cybersecurity strategy provide protection for their digital resources as well as continuous service operations while cyber threats continue to ascend.
References:
- G. Somani, M. S. Gaur, D. Sanghi, M. Conti, and R. Buyya, “DDoS attacks in cloud computing: Issues, taxonomy, and future directions,” Comput. Commun., vol. 107, pp. 30–48, Jul. 2017, doi: 10.1016/j.comcom.2017.03.010.
- S. Kumar, M. Dwivedi, M. Kumar, and S. S. Gill, “A comprehensive review of vulnerabilities and AI-enabled defense against DDoS attacks for securing cloud services,” Comput. Sci. Rev., vol. 53, p. 100661, Aug. 2024, doi: 10.1016/j.cosrev.2024.100661.
- A. Bhardwaj, V. Mangat, R. Vig, S. Halder, and M. Conti, “Distributed denial of service attacks in cloud: State-of-the-art of scientific and commercial solutions,” Comput. Sci. Rev., vol. 39, p. 100332, Feb. 2021, doi: 10.1016/j.cosrev.2020.100332.
- M. Rahaman, S. S. Bakkireddygari, S. Chattopadhyay, A. L. Gomez, V. Arya, and S. Bansal, “Infrastructure and Network Security,” in Metaverse Security Paradigms, IGI Global Scientific Publishing, 2024, pp. 108–144. doi: 10.4018/979-8-3693-3824-7.ch005.
- N. Tripathi and N. Hubballi, “Application Layer Denial-of-Service Attacks and Defense Mechanisms: A Survey,” ACM Comput Surv, vol. 54, no. 4, p. 86:1-86:33, May 2021, doi: 10.1145/3448291.
- A. K. Soliman, C. Salama, and H. K. Mohamed, “Detecting DNS Reflection Amplification DDoS Attack Originating from the Cloud,” in 2018 13th International Conference on Computer Engineering and Systems (ICCES), Dec. 2018, pp. 145–150. doi: 10.1109/ICCES.2018.8639414.
- M. Dimolianis, A. Pavlidis, D. Kalogeras, and V. Maglaris, “Mitigation of Multi-vector Network Attacks via Orchestration of Distributed Rule Placement,” in 2019 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Apr. 2019, pp. 162–170. Accessed: Feb. 13, 2025. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/8717838
- Mirsadeghi, F., Rafsanjani, M. K., & Gupta, B. B. (2021). A trust infrastructure based authentication method for clustered vehicular ad hoc networks. Peer-to-Peer Networking and Applications, 14, 2537-2553.
- AlZu’bi, S., Shehab, M., Al-Ayyoub, M., Jararweh, Y., & Gupta, B. (2020). Parallel implementation for 3d medical volume fuzzy segmentation. Pattern Recognition Letters, 130, 312-318.
- Hasan A. (2023) Understanding Distributed Denial of Service (DDoS) Attacks and its analysis, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Cloud Computing vs. DDoS: Are Cloud-Based Solutions Enough?, Insights2Techinfo, pp.1