By: Praneeth
Due to the apparent resource, cost-effectiveness, widespread, and fluidity of nature, the application of cloud forensics has introduced in the forensic field. This form of cloud forensics contains private, hybrid, and public models such as well as multiple options including protection, database, as well as software and integration. Since more and more businesses and enterprises are using cloud-based capabilities such as high scalability, lower IT costs, backup, and fast deployment [1]. Also, several governments and corporations have adopted cloud infrastructure as a part of this. Similarly, vendors of telecommunications services in the cloud are placing data centres in diverse geographic locations that serve the needs of both low latency and scalability [2]. A more serious issue, though, is the increase of cybercrimes and the growth of the cloud world. Security experts are concerned that because forensics in a cloud setting is so challenging. Thus, cloud forensics is the prime target of the cybercrimes. An external study in a cloud-based environment may be defined as a possible application in digital forensics. This area combines academic standards, standard procedures, and state-of-the-art technologies for processing incidents cloudwise, such that the results can be retrieved. Also, cloud storage has different levels of virtualization, replicated, and multi-tenant features. More to the point, cloud forensics uses specific protocol related to cloud infrastructure models [3]. Also, the technique used in cloud forensics depends on the implementation and operating style of the software platform. Method and service monitoring is much more restricted in PaaS and SaaS deployments [4].
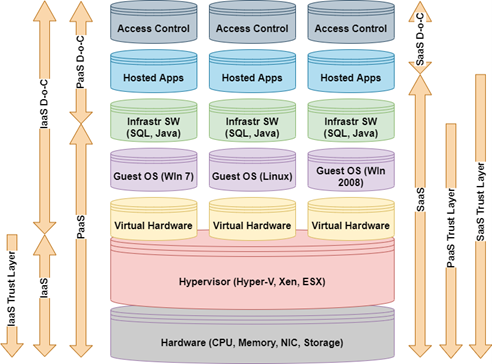
To be the fact that IaaS gives greater degrees of control (here) while additionally supporting forensic methods (See Fig. 1). Even though cloud forensics is complex, it’s undeniable that cloud advancement has given rise to privacy and protection issues. When anything like this was created, many modern forensics officers saw a massive uptick in their involvement in authorization, authentication, and accounting (AAA) because it highlighted many of those protocols at the same time that is, as well as their role in reconstruction, as digital evidence is used to investigate and find a non-malicious attack. It is not unlike conventional forensic methods that try to retrieve evidence from log data and is highly accurate and starkly contrasts with alternative forensics approaches to use the data. Yet, it distracts from the point of the show. The cloud is also defined as having three types of forensics: legal, organizational, and technical. Laws and agreements are created to ensure that digital forensic approaches do not transgress those regulating their use [5]. Instead, the organization of computer forensics covers various aspects of corporate policy”[6, 7]. Finally, the technological scope refers to the methods and techniques used to carry out a cloud investigation. As such, cloud forensics is standard in the digital forensic world. Since it incorporates the usage of cloud features, such as remote analysis, monitoring, and scale, such as the capacity to handle big workloads, it empowers the use of forensics as an investigation tool.
Cloud infrastructure has helped replacing most of the infrastructure like networking devices and servers with virtual servers’ applications that are set to meet the current businesses’ specific needs. One disadvantage is that third-party resources and information can be controlled and deployed by any party; another is that the customer can host them from anywhere. The information and applications are held on various hard drives in different places. Thus, there is a non-uniform feature of optical forensic artefacts. Another difference between automated investigation technologies and strategies is that they vary in price, sophistication, and accessibility. Almost all of the digital forensic instruments use a variety of hardware and software, and as a result, they are very incompatible, limiting what they can do. Besides that, target machines, such as mobile phones, have expanding storage space that forensic tools cannot accommodate. The larger the goal, the more technical analysis is needed. The technological threats placed in doubt the success and credibility of digital forensic activities, so it is reported.
Open Issues, Challenges and Future Research
- The availability of forensic data depends on the kind of cloud service used. infrastructure as a service (IaaS) clients have free access to the data they need for forensic investigations. At the same time, consumers who use SaaS may have no or limited access to such information.
- Time synchronisation is required for the construction of the chronology in forensics operations. Time synchronisation is difficult in a cloud context since the data of relevance is distributed across many physical computers and geographical locations.
- As a high number of resources are linked to the cloud, the expansion of endpoints are becoming more difficult.
- Virtualization allows multiple instances operating on a same physical system to be separated from one another in the cloud. As a result, it’s difficult to isolate resources during a forensics investigation without jeopardising the anonymity of other users that use the shared infrastructure.
References:
- Wazid, M., Katal, A., Goudar, R. H., & Rao, S. (2013, April). Hacktivism trends, digital forensic tools and challenges: A survey. In 2013 IEEE Conference on Information & Communication Technologies (pp. 138-144). IEEE.
- Sharma, B. K., Joseph, M. A., Jacob, B., & Miranda, L. C. B. (2019, November). Emerging trends in Digital Forensic and Cyber security-An Overview. In 2019 Sixth HCT Information Technology Trends (ITT) (pp. 309-313). IEEE.
- AlRikabi, H. T., Alaidi, A. H. M., Abdalrada, A. S., & Abed, F. T. (2019). Analysis of the Efficient Energy Prediction for 5G Wireless Communication Technologies. International Journal of Emerging Technologies in Learning, 14(8).
- Zawoad, S., & Hasan, R. (2013). Cloud forensics: a meta-study of challenges, approaches, and open problems. arXiv preprint arXiv:1302.6312.
- Aminnezhad, A., Dehghantanha, A., Abdullah, M. T., & Damshenas, M. (2013). Cloud forensics issues and opportunities. International Journal of Information Processing and Management, 4(4), 76.
- Al_Barazanchi, I., Shawkat, S. A., Hameed, M. H., & Al-Badri, K. S. L. (2019). Modified RSA-based algorithm: A double secure approach. TELKOMNIKA, 17(6), 2818-2825.
- Alabdulsalam, S., Schaefer, K., Kechadi, T., & Le-Khac, N. A. (2018, January). Internet of things forensics–challenges and a case study. In IFIP International Conference on Digital Forensics (pp. 35-48). Springer, Cham.
Cite As
Praneeth (2022) Cloud Forensics: Open Issues, Challenges and Future Research Opportunities, Insights2Techinfo, pp.1