By: Ivan Cvitić, G. Praneeth, D. Peraković
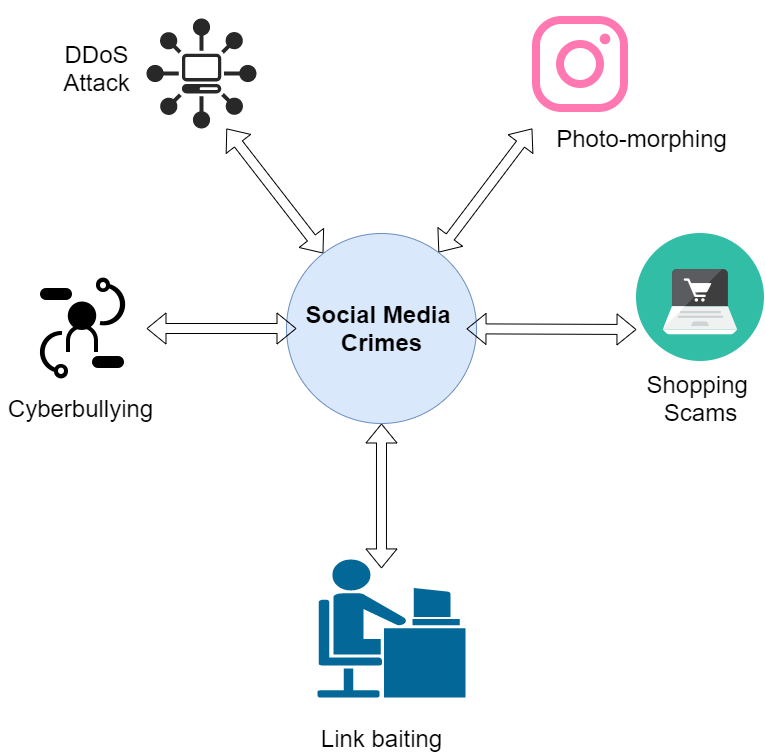
Industry 4.0 and Web 2.0 advances have made social networking acceptable and commonplace in many workplaces. These social networks are easy to operate; users on social networks can freely share knowledge, create profiles, and make active participants. However, social network accounts contain personal and private information; therefore, hackers try to steal users’ personal and confidential information [1]. Hence, social networking platforms such as LinkedIn, Facebook, and Twitter have been vulnerable to various online attacks. The attack may occur outside or within the system/on the network. A hacker either used denial of service (DoS) attacks to bring down a social network site or use cookie stealing to access users’ personal and confidential information. In order to protect the users from different types of cybercrimes, researchers proposed various kinds of forensics methods for social media networking. Digital Forensics techniques in social media networking are used to detect many types of cyber-crimes like (figure 1) [2]:
- Photo-morphing- In this case, hackers morph the pictures of people and post them to pornographic websites, or they may use them to blackmail them into providing sexual or financial favors.
- Shopping Scams- Hackers post many fake retail ads on social networking sites, and when users click on these ads, the cybercriminal obtains their personal information.
- Cyberbullying- Cyberbullying is defined as the act of sending or posting obscene or embarrassing messages or material online, as well as making threatening to conduct violent actions.
- Link baiting- When scam artists use this tactic, they offer the victim a link that tugs at their emotional investment in order to increase the likelihood of exploitation. When the link is opened, it takes the user to a bogus landing page that asks them to input their account credentials, and by this fake page, hackers steal the user’s credentials.
Apart from cybercrimes, social media is excellent for gathering evidence about possible perpetrators and witnesses [3]. Furthermore, integrating social network investigation with digital forensics in reaching a new and complex subgroup of data sources such as demographics, photos, places, and messages would provide investigators with expanded data access. The combination of this network information with the metadata has a tremendous investigative ability. The metadata may be used to support social networking information, as well. For these reasons, it can be assumed that social network analysis is emerging as a new direction in digital forensics [4].
Due to social media applications on many devices, social media forensics can use the data in these devices as visual proof. In other terms, extensive analysis, including the conversation records and digital artifacts such as photographs, keys, tweets, and friends, will remain as possible digital forensic evidence. Social network forensics is an essential key to different case investigations [5]. Similar forensics investigation can be conducted for smartphones, like Androids, iPhones, and Blackberries, to extract digital artifacts, including timestamps, passwords, URLs, and pictures. Based on the previous research, social network analysis may be an effective method to follow digital data distribution and very successful in uncovering and collecting digital evidence. Social network forensics often have three features: searching in reverse, weakening geographic searches, understanding how and when people use location, and metadata collection [6]. The first benefit of Google Image Searching is done in a window that provides the results in a tab. It also integrates six separate forensic charts to get various balances on social media. Lastly, it works for embedded images and presents all the metadata in whole rather than truncated form. Using these functionalities, investigators may have more access to relevant material. Social network forensics has been a significant theme in the digital investigation community.
While most digital forensics tools are geared to finding proof on the target computer; however, more advanced options for researching unfamiliar and challenging settings like big data are missing in these tools [7]. Because of this software diversity, most forensic software cannot automatically detect irregularities without human supervision. Hence, one of the most urgent priorities in developing forensic software is to add automated data searching. Of course, unfortunately, this complex challenge of adding automation in digital forensic methods and procedures is not met with uniform standards.
As has been said, digital forensics is a requirement for investigations that are often closely interwoven with cybersquatted aspects. The prevalence of cybercrimes and fraudulent activity in modern society creates an economic and personal risk for all in society. Thus, emerging technology in the investigative area can emphasize heterogeneity, protect anonymity, and have scalability.
Open Issues and Challenges for Forensics Techniques
- Anit-forensics techniques- Hackers use anti-forensic methods to conceal evidence or to divert investigators’ attention. Evidence concealment techniques include encryption, steganography, covert channelling, storage space data concealment, and residual data erasing, mainly used by hackers [8].
- Legal Challenges- As there are no standard guidelines available for the digital forensic process, sometimes some legal issues arise due to which digital forensic techniques are not implemented in the investigation process [8].
- Resource Challenges- As there are a large amount of data present at the social networking sites. Therefore, for a proper forensic investigation, the investigator should analyze all this data. However, sometimes the investigator did not have essential tools or knowledge for analyzing a large amount of data. Hence, there is a need to develop tools and education systems for digital forensic in social media networks [8].
References:
- Wazid, M., Katal, A., Goudar, R. H., & Rao, S. (2013, April). Hacktivism trends, digital forensic tools and challenges: A survey. In 2013 IEEE Conference on Information & Communication Technologies (pp. 138-144). IEEE.
- Foundation, I. F. (2019, April 28). Application Of Social Media Forensics To Investigate Social Media Crimes. IFF Lab. https://ifflab.org/application-of-social-media-forensics-to-investigate-social-media-crimes/.
- Rocha, A., Scheirer, W. J., Forstall, C. W., Cavalcante, T., Theophilo, A., Shen, B., … & Stamatatos, E. (2016). Authorship attribution for social media forensics. IEEE transactions on information forensics and security, 12(1), 5-33.
- Baggili, I., & Breitinger, F. (2015). Data sources for advancing cyber forensics: what the social world has to offer.
- Al Mutawa, N., Baggili, I., & Marrington, A. (2012). Forensic analysis of social networking applications on mobile devices. Digital investigation, 9, S24-S33.
- Zampoglou, M., Papadopoulos, S., Kompatsiaris, Y., Bouwmeester, R., & Spangenberg, J. (2016, April). Web and social media image forensics for news professionals. In Proceedings of the International AAAI Conference on Web and social media (Vol. 10, No. 1).
- Khan, S., Gani, A., Wahab, A. W. A., Shiraz, M., & Ahmad, I. (2016). Network forensics: Review, taxonomy, and open challenges. Journal of Network and Computer Applications, 66, 214-235.
- Fakiha, B. (2020). Digital Forensics: Crimes and Challenges in Online Social Networks Forensics. Journal of the Arab American University, 6(1), 15-33.
Cite this article as:
Ivan Cvitić, G. Praneeth, D. Peraković (2021), Digital Forensics Techniques for Social Media Networking, Insights2Techinfo, pp.1