By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Email: nee.kee2001.nks@gmail.com
Abstract
Phishing attacks is a significant security threat to the cloud computing. This paper proposes a novel framework that integrates blockchain technology with federated learning to enhance phishing detection in cloud computing. Federated learning enables decentralized model training across multiple edge devices without transferring data, ensuring user privacy. Blockchain stores the detected phishing URLs in an immutable ledger, ensuring the trust and transparency. By leveraging the whitelist of popular websites, the system effectively shortens the detecting times and increases the performance. Safe data is encrypted by using Secure Hash Algorithm (SHA-3) and uploaded to the cloud, once again improve the security. This combination method increases phishing detection accuracy, system security, and user privacy, making it an effective solution for cloud-based systems.
Keywords: Blockchain, Cloud, Federated Learning, Phishing, Secure Hash Algorithm, SHA-3
Introduction
Blockchain is a distributed database that maintains a growing amount of data by using hash pointer scheme. The data in the blockchain is managed in blocks. Each block connects previous blocks in the cryptography chain in a way that makes tampering nearly hard, which maintains a consistent view of the entire system, guarantees the correctness of data, and fosters trust. [1]
The AI technique discussed in this paper is federated learning. Federated learning is a type of machine learning that trains models on various edge devices without transferring the data across network and relying on a central server. [2] After training, the updated models are sent to a central server to aggregate the updates and enhance the model’s accuracy and phishing detection capabilities. The updated global model is distributed to each edge device to perform real-time detection. This ensures privacy and security as the sensitive data is not transmitted.
Framework
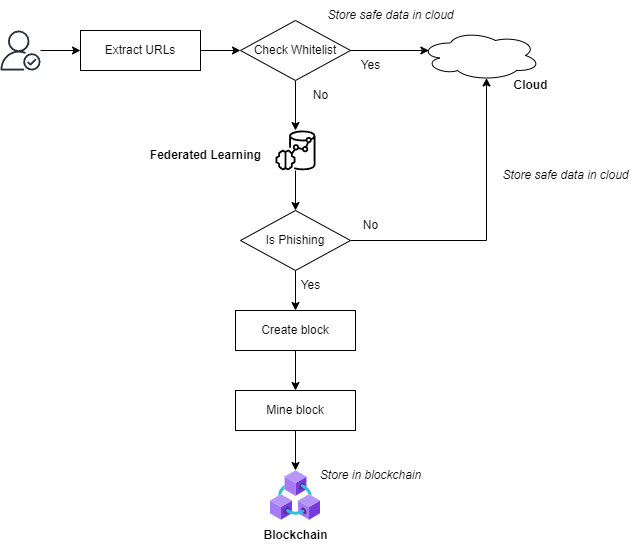
This paper’s proposed framework integrates federated learning with blockchain to improve the existing phishing detection methods. Blockchain is used to store the detected URL, while federated learning is used to detect phishing. When users want to upload data on the cloud, the URLs will be extracted and checked to see whether they are in the whitelist. The whitelist is a dataset of Alexa’s most popular website URLs. [3] Checking with the whitelist can improve efficiency and effectively reduce the time of phishing detection.
After that, the federated learning model detects phishing URLs. Once a phishing URL is detected, a block is created and added to the blockchain once it passes through the mining process. An enhanced PoW algorithm is used to select a miner among the cloud users. After the miner verifies the contents, the block gets mined. Once a block containing phishing content is mined, it becomes visible to all cloud users to allow legitimate cloud users to be aware of phishing content. The mined block will be added to the blockchain. The safe data will be encrypted using the Secure Hash Algorithm (SHA-3) and uploaded to the cloud. [4]
Conclusion
In conclusion, the paper proposed a phishing detection method that combining federated learning and blockchain technology, effectively improves the security and capabilities of the system. Federated learning eliminates the need to transfer data across the network, preserving user privacy. Besides, federated learning provides continuous learning as the phishing detection model is constantly updated from time to time, improving the detection accuracy. In addition, blockchain improves trust and transparency in the phishing detection process, avoids tampering data, and ensures the accuracy of the data.
Reference
- “Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications – ScienceDirect.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1084804524000614
- I. Priyadarshini, “Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning,” Big Data and Cognitive Computing, Feb. 2024, doi: 10.3390/bdcc8030021.
- “PhishingRTDS: A real-time detection system for phishing attacks using a Deep Learning model – ScienceDirect.” Accessed: Oct. 05, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0167404824001445
- R. Karthika, C. Valliyammai, and M. Naveena, “Phish Block: A Blockchain Framework for Phish Detection in Cloud,” Jun. 2022, doi: 10.32604/csse.2023.024086.
- Chaudhary, P., Gupta, B. B., Choi, C., & Chui, K. T. (2020). Xsspro: Xss attack detection proxy to defend social networking platforms. In Computational Data and Social Networks: 9th International Conference, CSoNet 2020, Dallas, TX, USA, December 11–13, 2020, Proceedings 9 (pp. 411-422). Springer International Publishing.
- Gupta, B. B., Gaurav, A., Arya, V., Alhalabi, W., Alsalman, D., & Vijayakumar, P. (2024). Enhancing user prompt confidentiality in Large Language Models through advanced differential encryption. Computers and Electrical Engineering, 116, 109215.
Cite As
Kee S.N. (2024) Combining Blockchain and AI for Phishing Detection in Cloud Computing, Insights2Techinfo, pp.1