By: KUKUTLA TEJONATH REDDY, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, tejonath45@gmail.com
Cryptography means protecting sensitive information using some mathematical algorithms and techniques. Cryptography has an important role in this modern cyberworld. In cryptography we need to using encryption algorithm to convert original message (plain text) into ciphertext, which is we cannot able into understand to decrypt that message we need a key. If the receiver has the key, he can able to read the message or he cannot able to decrypt the message. In this article we are discussing about some concepts of cryptography, types of cryptography, challenges of cryptography.
Introduction
Now a days protecting our sensitive information or data is important. By using cryptography, we can convert our data or information into ciphertext which we can be able to understand using mathematical algorithms and some techniques. The word crypto means “hidden” or “secret” and graphy meaning is “writing”. In this article we will discuss about some concepts of cryptography, types of cryptography, and challenges of cryptography.
Features of Cryptography
- Confidentiality: Confidentiality means sensitive data or information can only accessed by authorized persons only, others used not able to access.
- Integrity: In integrity information can’t able change between sender and receiver. If any unauthorized person tries to change the information, Cryptographic techniques will detect any unauthorized person.
- Authentication: It will verify the sender and receiver that they are authorized persons or not.
Types of Cryptography
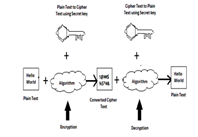
- Symmetric Key Cryptography: In Symmetric Key Cryptography both sender and receiver will use only one key to encrypt and decrypt. It is a simple and faster method but problem is the sender and receiver have to exchange the key in securely. There are two most poplar symmetric key cryptography they are Data Encryption System (DES) and Advanced Encryption System (AES).
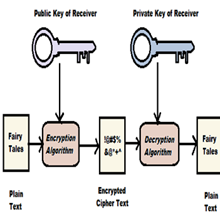
- Asymmetric Key Cryptography: In Asymmetric Key Cryptography there are two keys one is public key and another is private key. Public key is for encryption and the private key for decryption. Public and private 2 different keys. If public key is found by someone also there is no problem only intended receiver only have private key which helps to decrypt. Asymmetric Key Cryptography algorithm is used RSA algorithm.
- Hash functions: In hash functions algorithms will change data into a fixed length string which is known as hash functions. Many Operating Systems will used hash functions to encrypt passwords
Advantages of Cryptography
- Data Protection: Cryptography will protect our data, if our device is lost or stolen by someone. Data inside the device is in encrypted format without decryption key anyone cannot able to access the device
- Access Control: By using Cryptography we can control the access only who have proper permission will get access to the resources that means only who have decryption key will get access to the resources.
- Secure Communication: when we are sending any important information or any message on internet, we can send in encrypted form using Cryptography then no one couldn’t able to understand.
- Password Protection: Using Cryptography we can secure passwords by storing passwords in hash function. Then attackers can’t able to find the passwords
Disadvantages of Cryptography
- Key Management: We face challenges when we are managing encryption keys in large-scale system. If we lost the key means you lost the data. If we lose the keys means we are unauthorized person to access.
- Human Errors: we need to manage secret keys and passwords properly. If we are using easy passwords or not taking care of secret keys it will leads to data loss. So, we need to be more careful when we are dealing with keys and passwords.
- Cost: Cryptography are expensive software for strong encryption and decryption. Some small-scale industries or organisation can’t able to afford.
Applications of Cryptography
- VPN (Virtual Private Network): VPNs will encrypt connection and provides a secure and private network over internet. Allows the user for remote connection it will be helpful for so many employees who is on work from home.
- Data Privacy and Security: Cryptography will used to protect sensitive data or financial information form unauthorized persons.
- Password Protection: Using Cryptography we can secure passwords by storing passwords in hash function. Then attackers can’t able to find the passwords
- Secure Messaging Apps: Prefer end-to-end encryption messaging apps like WhatsApp to protect our data.
- Secure File Storage: By using cryptography encrypt the data files and folders and protect the data from unauthorized persons
Conclusion
Cryptography is important in this modern cyberworld. It will help to transfer the data securely. In Cryptography the data will encrypt and send to receiver if the receiver is an authorized person means he will have a decryption key with help of that help he can decrypt the data. There are various types in cryptography. Using different mathematical algorithms and different techniques the data will be encrypted. In the article I have discussed about that. Day by day technology will evolve we have to protect our data.
Reference
- S. Chandra, S. Bhattacharyya, S. Paira and S. S. Alam, “A study and analysis on symmetric cryptography,” 2014 International Conference on Science Engineering and Management Research (ICSEMR), Chennai, India, 2014, pp. 1-8, .
- S. Chandra, S. Paira, S. S. Alam and G. Sanyal, “A comparative survey of Symmetric and Asymmetric Key Cryptography,” 2014 International Conference on Electronics, Communication and Computational Engineering (ICECCE), Hosur, India, 2014, pp. 83-93, .
- A. M. Qadir and N. Varol, “A Review Paper on Cryptography,” 2019 7th International Symposium on Digital Forensics and Security (ISDFS), Barcelos, Portugal, 2019, pp. 1-6, doi: .
- A. Eskicioglu and L. Litwin, “Cryptography,” in IEEE Potentials, vol. 20, no. 1, pp. 36-38, Feb-March 2001,.
- T. R. Devi, “Importance of Cryptography in Network Security,” 2013 International Conference on Communication Systems and Network Technologies, Gwalior, India, 2013, pp. 462-467,.
Cite As
REDDY K.T (2023) Cryptography in Action: Applications and Advantages, Insights2Techinfo, pp.1