By: Achit Katiyar1,2
1South Asian University, New Delhi, India.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan. Email: achitktr@gmail.com
Abstract
Cloud computing has turned out to be a key element of modern IT infrastructure, providing flexible resources and services. However, because cloud designs are shared, security becomes an issue. This article explores methods for improving cloud computing security with a focus on flexible security protocols. This discussion also explores the many evolutionary algorithms and their applications in improving cloud security, as well as the obstacles and future research in this field.
Introduction
The introduction of cloud computing has changed how organizations manage and deploy IT resources [1]. This is because classical security methods tend to be negatively correlated in countering the active and complex threats. The following are the major benefits of cloud computing, which displays various insecurity threats such as fraud, leakage of information, persons’ risk and cybercrimes. It is, therefore, concerning that there has been a growing trend towards optimization of cloud security using evolutionary techniques [2]. The following article offers a brief overview of such and such techniques and the potential they hold to optimise cloud security.
Key Evolutionary Algorithms
- Genetic algorithms (GA):
Genetic algorithms are popularly referred to as search methods which are drawn from natural selection and genetics [3]. These algorithms help their users by evolving the solutions of these optimization problems.
Application in Cloud Security-
As for GAs, they have been found to aid in optimising resources in cloud security as well as in identifying security issues in cloud systems [4]. They do this by requiring the organisation to modify and adapt the security protocols and procedures in place GAs are useful as they enable an organisation to adapt to the changing threat environment.
- Particle swarm optimization (PSO):
Particle Swarm Optimization (PSO) is a swarm intelligent method which is inspired by the bird’s flocking or fishes schooling social behaviour [5] [6]. It enhances problems by constantly transforming the possible solutions [7].
Application in Cloud Security-
PSO can be employed for the purpose of scheduling of virtual machines as well as for load balancing of cloud data centres [2]. It improves security by successfully handling resources and reducing areas of attack [8].
- Artificial Immune System (AIS):
AIS are developed after the biological immune system’s ability to identify and react to infections [9]. These systems use the pattern recognition and anomaly detection for finding threats.
Application in Cloud Security-
AIS can classify and react to harmful activity in cloud settings by developing responses to new threats [10]. AIS provides strategies to detect and defend against altering threats.
Challenges of Implementing Evolutionary Approaches
- Computational Overhead:
Evolutionary algorithms often require processing power, which could pose a challenge, for security applications that need real time responses [11]. It is tough to find a connection between performance and security.
- Scalability:
In dynamic cloud environments its important to have security measures that can adapt to varying workloads and conditions. Protecting the scalability of algorithms presents a challenge [2]. - Adaptability:
The ability of algorithms to adjust to evolving threats is essential, for maintaining robust security [10]. Continuous learning and adaptation methods are required to manage growing security threats.
Emerging trends and future directions
- Hybrid Evolutionary Algorithms:
Integrating several evolutionary algorithms can improve their efficacy and efficiency in cloud security. Hybrid techniques use the strengths of different algorithms to tackle difficult security problems [2].
- Integration of Machine Learning:
Integrating evolutionary algorithms and machine learning approaches can enhance threat identification and response capabilities. Machine learning models can give useful information for optimizing evolutionary security systems [12].
The integration of evolutionary algorithms and machine learning is shown in figure 1.
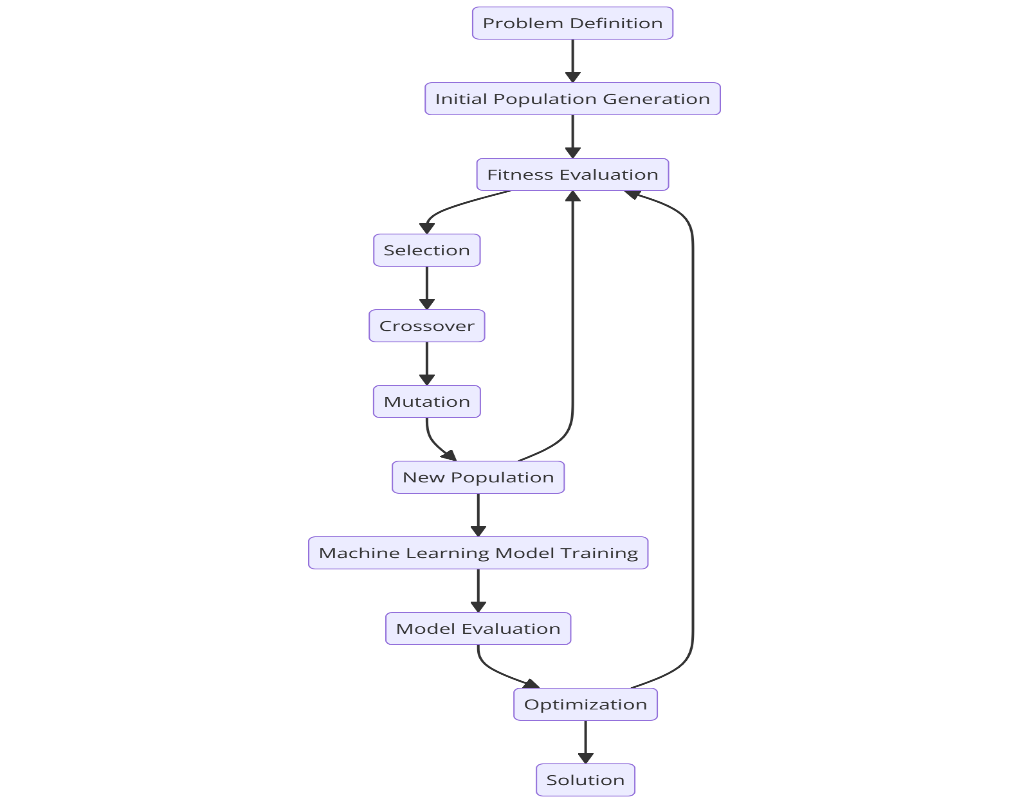
Conclusion
Evolutionary methods offer potential in tackling the security issues of cloud computing systems. Genetic algorithms, particle swarm optimization and artificial immune systems are intelligent approaches to enhance security. As a result, this study introduces a multi-objective facility allocation issue with cooperative-based multi-level backup coverage that takes into account the attraction of distance-based facilities [13].The successful application of these techniques will require addressing difficulties such as processing overhead, scalability, and flexibility. Hybrid algorithms and machine learning integration have become topics that have tremendous promise as potential cloud security advances.
References
- M. Armbrust et al., “A View of Cloud Computing,” Commun ACM, vol. 53, pp. 50–58, Apr. 2010, doi: 10.1145/1721654.1721672.
- S. Aljawarneh, A. Alawneh, and R. Jaradat, “Cloud security engineering: Early stages of SDLC,” Future Gener. Comput. Syst., vol. 74, Oct. 2016, doi: 10.1016/j.future.2016.10.005.
- D. E. Goldberg and J. H. Holland, “Genetic Algorithms and Machine Learning,” Mach. Learn., vol. 3, no. 2, pp. 95–99, Oct. 1988, doi: 10.1023/A:1022602019183.
- J. Chen, T. Du, and G. Xiao, “A multi-objective optimization for resource allocation of emergent demands in cloud computing,” J. Cloud Comput., vol. 10, no. 1, p. 20, Mar. 2021, doi: 10.1186/s13677-021-00237-7.
- J. Kennedy and R. Eberhart, “Particle swarm optimization,” in Proceedings of ICNN’95 – International Conference on Neural Networks, Nov. 1995, pp. 1942–1948 vol.4. doi: 10.1109/ICNN.1995.488968.
- J. C. Bansal, P. K. Singh, and N. R. Pal, Eds., Evolutionary and Swarm Intelligence Algorithms, vol. 779. in Studies in Computational Intelligence, vol. 779. Cham: Springer International Publishing, 2019. doi: 10.1007/978-3-319-91341-4.
- Y. Shi and R. Eberhart, “A modified particle swarm optimizer,” in 1998 IEEE International Conference on Evolutionary Computation Proceedings. IEEE World Congress on Computational Intelligence (Cat. No.98TH8360), May 1998, pp. 69–73. doi: 10.1109/ICEC.1998.699146.
- A. M. Widodo et al., “Port-to-Port Expedition Security Monitoring System Based on a Geographic Information System,” Int. J. Digit. Strategy Gov. Bus. Transform. IJDSGBT, vol. 13, no. 1, pp. 1–20, Jan. 2024, doi: 10.4018/IJDSGBT.335897.
- S. Forrest, S. A. Hofmeyr, A. Somayaji, and T. A. Longstaff, “A sense of self for Unix processes,” in Proceedings 1996 IEEE Symposium on Security and Privacy, May 1996, pp. 120–128. doi: 10.1109/SECPRI.1996.502675.
- Z. Ataser, “A review of artificial immune systems,” presented at the IJCCI 2013 – Proceedings of the 5th International Joint Conference on Computational Intelligence, Oct. 2013, pp. 128–135.
- Y. Shi and R. Eberhart, “A modified particle swarm optimizer,” in 1998 IEEE International Conference on Evolutionary Computation Proceedings. IEEE World Congress on Computational Intelligence (Cat. No.98TH8360), May 1998, pp. 69–73. doi: 10.1109/ICEC.1998.699146.
- “Transparency and Accountability: Computer Science & IT Book Chapter | IGI Global.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.igi-global.com/chapter/transparency-and-accountability/354396
- C.-Y. Lin, M. Rahaman, M. Moslehpour, S. Chattopadhyay, and V. Arya, “Web Semantic-Based MOOP Algorithm for Facilitating Allocation Problems in the Supply Chain Domain,” Int. J. Semantic Web Inf. Syst. IJSWIS, vol. 19, no. 1, pp. 1–23, Jan. 2023, doi: 10.4018/IJSWIS.330250.
- Gupta, B. B., Chui, K. T., Gaurav, A., Arya, V., & Chaurasia, P. (2023). A novel hybrid convolutional neural network-and gated recurrent unit-based paradigm for IoT network traffic attack detection in smart cities. Sensors, 23(21), 8686.
- A. Gaurav, B. B. Gupta, K. T. Chui and V. Arya, “Enhancing Email Security in Consumer Electronics with a Hybrid Deep Learning Approach,” 2024 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 2024, pp. 1-5, doi: 10.1109/ICCE59016.2024.10444468.
Cite As
Katiyar A. (2024) Evolutionary Methods to Secure Cloud Computing, Insights2Techinfo, pp.1