By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
The sophistication of social engineering assaults has increased in the constantly changing world of cyber threats. Two popular methods used by cybercriminals to take advantage of human weaknesses and obtain sensitive data without authorization are spear phishing and smishing. Spear phishing uses targeted email attacks, whereas smishing uses SMS messages to trick victims. This article offers a thorough how-to for comprehending, identifying, and reducing these risks. The objective of this guide is to provide individuals and businesses with the necessary knowledge to protect against these widespread cyber risks by examining real-world instances, detection methods, and preventive actions.
Introduction
Unmatched convenience has been brought about by the digital age, but it has also made room for new types of cybercrime. Among them, attacks using social engineering such as smishing and spear phishing have become important dangers[1]. Because they prey on human psychology instead of technological weakness, these attacks are more difficult to defend against. In addition to highlighting the distinction between spear phishing and smishing, this paper explores their mechanism and offers practical detection and avoidance techniques.
Understanding Spear Phishing
Spear phishing is a type of targeted phishing in which the attackers modify their strategies to trick particular people or organizations[2]. Spear phishing, in contrast to typical phishing efforts, entails a thorough investigation of the victim’s relationship, interests, and job function. The objective is to create a very convincing message that device the receiver into disclosing private information, opening dangerous attachments, or clicking on malicious links.
How Spear Phishing Works[3]
- Reconnaissance: Through social media, corporate websites, or data breaches, attackers learn about the target.
- Crafting the Message: Attackers use the information they have gathered to craft individualized emails that look authentic.
- Execution: The email is sent to the intended recipient, frequently posing as a reliable organization such as a bank, service provider, or colleague.
- Exploitation: The attacker obtains sensitive information or systems if the target is tricked.
Understanding Smishing
Smishing, also known as SMS phishing, is a type of phishing in which victims are tricked by text messages. These communications frequently include compelling offers or urgent demands that entice readers to click on harmful links or divulge personal information[4]. Smishing has grown in effectiveness as an attack vector due to the increasing use of smartphones.
How Smishing works[5]
- Message Creation: Attackers create SMS messages that seem to be from reputable organizations, such government offices, banks, or delivery services.
- Delivery: Using spoof sender IDs, the message is transmitted to a huge number of phone numbers.
- Deception: The message makes the receiver feel compelled to act by arousing their curiosity or sense of urgency.
- Exploitation: Data theft, virus installation, or monetary loss result from clicking on the link or entering personal information.
Detection Techniques for Spear Phishing and Smishing
Security detection of these attacks requires simultaneous implementation of awareness measures together with technological tools and knowledge dissemination. Below are some effective strategies:
Analyze the Sender :
The sender’s online identity for emails must be checked through their address for any indications of falseness or unexpected domain names.
It is essential to check the messaging number for every text message because unknown senders represent a potential security risk.
Look for Red Flags :
Threatening communication with urgent words attracts users into taking fast actions immediately.
Grammatical errors, unusual phrasing, or poor formatting.
The requester attempts to obtain access to passwords or credit card details.
Verify Links and Attachment
Before clicking on a link, you should place your cursor above it to view the target URL.
Attachments must always be avoided from source domains that lack reputation trust.
Use Security Tools :
Organizations need to install email screening protocols which identify phishing scams that block their entry.
The implementation of anti-malware software helps stop the entry of harmful downloads into your system.
Mobile phones should have spam filter options enabled to block unwanted text messages.
Education and Train :
Organize ongoing educational workshops that teach staff members about social engineering methods.
Organizations should conduct tests that combine simulated phishing and smishing simulations to help their workforce develop improved readiness against attacks.
Preventive Measures
Spear phishing and smishing attacks can best be prevented through prevention methods. The following actions form a proactive approach both at an individual level and organizational level:
Implement Multi-Factor Authentication (MFA) :
The security enhancement provided by MFA refers to multiple verification steps that protect accounts from unauthorized access after a credential loss.
Keep Software Updated :
Upgrading all operating systems and applications and security software patches important vulnerabilities.
Monitor Accounts and Transactions :
Individuals must examine bank statements and email accounts and other sensitive platforms for any suspicious activities on a regular basis.
Report Suspicious Messages :
All personnel should alert IT departments and relevant authorities about phishing and smishing attempts they encounter.
Use Encrypted Communication Channels :
Detailed transmissions should always use encrypted applications to minimize interception danger.
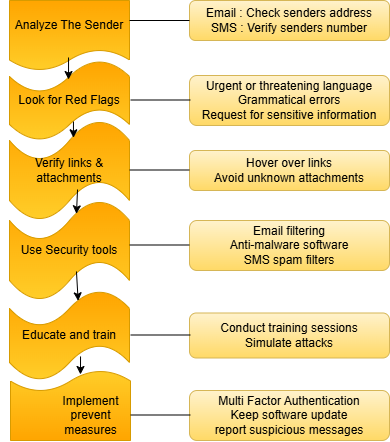
Fig : Detecting and preventing process
Conclusion
Modern cybersecurity faces numerous risks because of spear phishing combined with smishing attacks. People who grasp the attack methods can protect themselves and their organizations more effectively through strong proactive procedures. The combination of active monitoring and knowledge and suitable security tools helps people avoid cybercriminals. Modern technological advancement requires updated cybersecurity strategies which create resistance to increasingly complex threats.
References
- P. Y. Leonov, A. V. Vorobyev, A. A. Ezhova, O. S. Kotelyanets, A. K. Zavalishina, and N. V. Morozov, “The Main Social Engineering Techniques Aimed at Hacking Information Systems,” in 2021 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), May 2021, pp. 0471–0473. doi: 10.1109/USBEREIT51232.2021.9455031.
- T. Xu, K. Singh, and P. Rajivan, “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Appl. Ergon., vol. 108, p. 103908, Apr. 2023, doi: 10.1016/j.apergo.2022.103908.
- “What is Spear Phishing? Definition with Examples | CrowdStrike,” CrowdStrike.com. Accessed: Mar. 19, 2025. [Online]. Available: https://www.crowdstrike.com/en-us/cybersecurity-101/social-engineering/spear-phishing/
- [4] E. B. Blancaflor, K. J. R. Cruz, F. J. C. Monta, and P. E. Flores, “Unmasking the Threat: Analyzing and Mitigating SMS Smishing Attacks,” in Proceedings of Ninth International Congress on Information and Communication Technology, X.-S. Yang, R. S. Sherratt, N. Dey, and A. Joshi, Eds., Singapore: Springer Nature, 2024, pp. 69–78. doi: 10.1007/978-981-97-5441-0_7.
- “What is Smishing & How Does it Work?,” Perception Point. Accessed: Mar. 19, 2025. [Online]. Available: https://perception-point.io/guides/phishing/what-is-smishing-how-does-it-work/
- Setiawan, Iwan, et al. “Utilizing Random Forest Algorithm for Sentiment Prediction Based on Twitter Data.” First Mandalika International Multi-Conference on Science and Engineering 2022, MIMSE 2022 (Informatics and Computer Science)(MIMSE-IC-2022). Atlantis Press, 2022.
- M. Rahaman, S. S. Bakkireddygari, S. Chattopadhyay, A. L. Gomez, V. Arya, and S. Bansal, “Infrastructure and network security,” in Advances in information security, privacy, and ethics book series, 2024, pp. 108–144..
- Yu, C., Li, J., Li, X., Ren, X., & Gupta, B. B. (2018). Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimedia Tools and Applications, 77, 4585-4608.
- Zhang, Q., Guo, Z., Zhu, Y., Vijayakumar, P., Castiglione, A., & Gupta, B. B. (2023). A deep learning-based fast fake news detection model for cyber-physical social services. Pattern Recognition Letters, 168, 31-38.
- Brijith A. (2023) Phishing Attack and its Types, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) From Spear Phishing to Smishing : A Complete Detection Guide, Insights2techinfo pp.1