By: M. Sai, F. J. Penalvo
Fuzzing is a widely used automated software testing technique that entails introducing random or inaccurate data into a computer system in order to find software vulnerabilities and shortcomings. Though it may be challenging, it is possible that the procedure will be required throughout the testing phase. Reduced time required for software fuzzing improves the efficiency and productivity of testing, allowing for more extensive analysis and correction of software issues or vulnerabilities. The test’s quality and the number of wrong inputs used, as well as the manner in which samples were gathered or created, are only a few of the numerous variables that affect fuzzing methods.
Fuzzing is a technique for identifying faults in a particular program. When random and inaccurate data is provided to the computer, we can see whether the software behaves differently, such as crashing or refusing service. Along with the crash data itself, we may record the input data used to produce the malfunction, allowing us to locate the precise location of the data that caused the application to fail. The technique is performed whenever new data kinds are introduced in order to ascertain the software’s flaws.
Fuzzing is a well-known and low-cost approach for identifying faults and security vulnerabilities in software prior to release [1]. It is ideal for identifying faults in software prior to its release. Testing software without access to the source code or knowledge of the high-level programming language used to develop it is simple, as fuzzing is automated and requires no supervision. The test case depicted in Figure 1 was constructed using randomly generated inputs for use in a fuzzer to detect faults in the target software.

Two fuzzers, FileFuzz and Peachfuzz, are utilised in this research to compare the effectiveness of two major methods of fuzzing and to assess how fuzzing may be improved for greater efficiency [2]. The common Fuzzing and techniques are given in the Fig. 2.
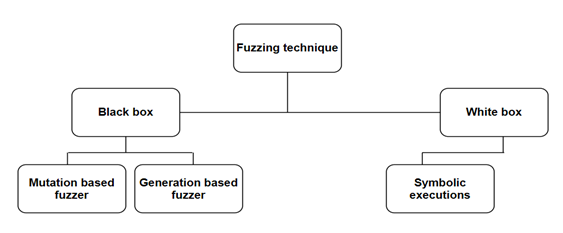
Black box fuzzing: The Microsoft Forefront Edge Security team says that black-box fuzzing necessitates providing invalid data with no code path verification. Since it requires no prior knowledge of the source code, black-box testing has an advantage over other testing strategies, and it is also a more useful tool for both developers and attackers. While the speed of testing software with complex logic may match developer expectations, the target’s lack of understanding means it will not. Additionally, black-box testing has little code coverage and is incapable of finding security vulnerabilities [3].
A mutation-based fuzzer is a method for fuzzing a target by using a legitimate test case, including incorrect input.
Protocol-aware or intelligent fuzzing, which uses generation-basedfuzzers, relies on pre-existing knowledge about the target. The test case must be created from scratch depending on the target’s format.
White Box Fuzzing: One kind of open-source automated testing tool called “white-box testing” or “smart fuzzing” does whole-software testing by looking for negative pathways and may span millions of instructions, execution traces, and lines of code.
White box testing uses symbolic execution [4]. When using symbolic values in place of standard data, this technique enables you to predict how the programme will react when given infinite inputs, and it permits the exploration of input spaces that are unrealistic for random testing.
Open Research issues
- To assist with future research on fuzzers that may be used to locate and exploit vulnerabilities in programs running on embedded devices running real-time operating systems (RTOS) based on Windows OSs. Windows IoT, previously known as Windows Embedded, has key capabilities that are built into the Windows OS that are already installed on physical devices.
- The first step before using fuzzing is to properly comprehend the target’s capabilities.
- Fuzzing is a technique with application in many domains, such as IoT, networking, and software testing, and various techniques and tools have to be generated to ensure overcome the vulnerabilities and bugs in them.
References
- Godefroid, P., Levin, M. Y., & Molnar, D. A. (2008, February). Automated whitebox fuzz testing. In NDSS (Vol. 8, pp. 151-166).
- Alhawi, O. M., Akinbi, A., &Dehghantanha, A. (2019). Evaluation and application of two fuzzing approaches for security testing of IoT applications. In Handbook of Big Data and IoT Security (pp. 301-327). Springer, Cham.
- .Miller, C., & Peterson, Z. N. (2007). Analysis of mutation and generation-based fuzzing. Independent Security Evaluators, Tech. Rep, 4.
- Godefroid, P., Levin, M. Y., & Molnar, D. (2012). SAGE: Whitebox Fuzzing for Security Testing: SAGE has had a remarkable impact at Microsoft. Queue, 10(1), 20-27
Also Read: