By: Mosiur Rahaman ,International Center for AI and Cyber Security Research and Innovation, Asia University, Taiwan
Abstract:
Because of the simple nature and trust that come with Text interactions, smishing a type of spoofing via SMS has become a significant security threat. Because of the briefly text messages, the necessity for real-time analysis, and the regularly altering methods of hackers, conventional methods for detection frequently fail. The objective of the present research is to boost scams detection by using hybrid deep learning designs. Neural networks with convolution (CNNs), neural networks with recurrent neurons (RNNs), transformers that operate and other data analysis methods are examples of concepts that are incorporated into hybrid designs. This makes it possible them to capture situational relationships and local information while combining the positive aspects of each model.
Introduction:
Both Facebook and Google are always trying to make the internet more user-friendly. Users of smartphones are growing in number as technology becomes more accessible [1]. Due to the huge amount of people using the Internet, cases of cybercrime like phishing have risen substantially.
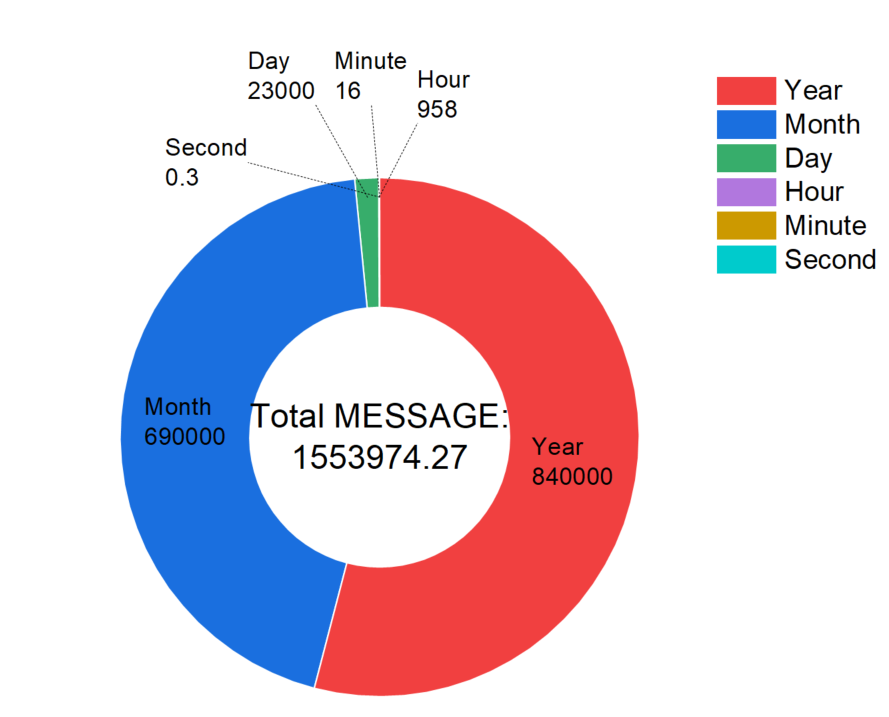
Text messaging between mobile devices is accomplished using an approach to communication called Short Message Service (SMS). With this popular messaging software, users may communicate with one other via short text messages [2]. In marketing, text messaging is widely used. The increased usage of text messaging gives hackers an edge. There are over 9132 million text writing sent globally per hour. Most SMS messages are opened in a matter of seconds shown in figure 1 [3].
The literature has documented a few methods for smishing detection. Most solutions have recommendations, including to be aware of unknown links in the SMS. Still, the literature has touched on the difficulty of smishing pattern detection. According to an analysis of current methods, the majority use blocklist, heuristic, and allow list strategies for detecting smishing attacks.
Landscape of Smishing Threat:
According to Kaspersky’s telemetry, the total number of cyberthreats in the United Arab Emirates fell by 20% in 2023 compared to 2022. However, phishing attacks that use social engineering techniques to trick users into disclosing private information rose by 70%. Examining the threat environment in the United Arab Emirates in more detail, Kaspersky analysts saw a 53% increase in assaults utilizing exploits that take advantage of specific system vulnerabilities between Q4 and Q3 of 2023 [4]. In the UAE, ransomware attacks which encrypt a victim’s data, files, or system and make them available in return for a fee rose by 86%.
In 2023, phishing assaults escalated to previously unheard-of heights, according to the Vade “Phishers’ Favourites 2023 Year-in-Review Report,” which examined millions of phishing documents and websites. Despite a 28% decrease from 2022, globally, more over 1.76 billion phishing URLs were transmitted, with 197,000 unique URLs detected [5]. The most often impersonated brand was Facebook, which accounted for 23% of all unique phishing websites. The most frequently targeted industries were cloud services, social media, and financial services, which accounted for 32%, 26%, and 22% of assaults, respectively. Password reuse problems allowed attackers to access other company platforms, which led to a startling 113% surge in social media phishing. By embedding phishing URLs in QR codes to get beyond email filters, hackers began to significantly increase QR code phishing in Q2 2023.
Smishing Detection in Deep Learning:
The ability of deep learning machines to recognize important characteristics in text messages and decide if they are authentic or malicious. To demonstrate how much better deep learning models are at detecting smishing attacks, a comparison with standard machine learning algorithms takes place. Convolutional neural networks (CNNs) and long short-term memory (LSTM) are combined in this research [6].
Deep learning models, which replicate the human neural network in the brain, are currently at the cutting edge of artificial intelligence, allowing machines to learn and make challenging choices. In order for the neural network to compare the output with the expected result, the output and the provided input sets must be provided. The researchers used several features of SMS and URLs to achieve categorization using a flow-based method [7].
Hybrid Deep Learning Architecture:
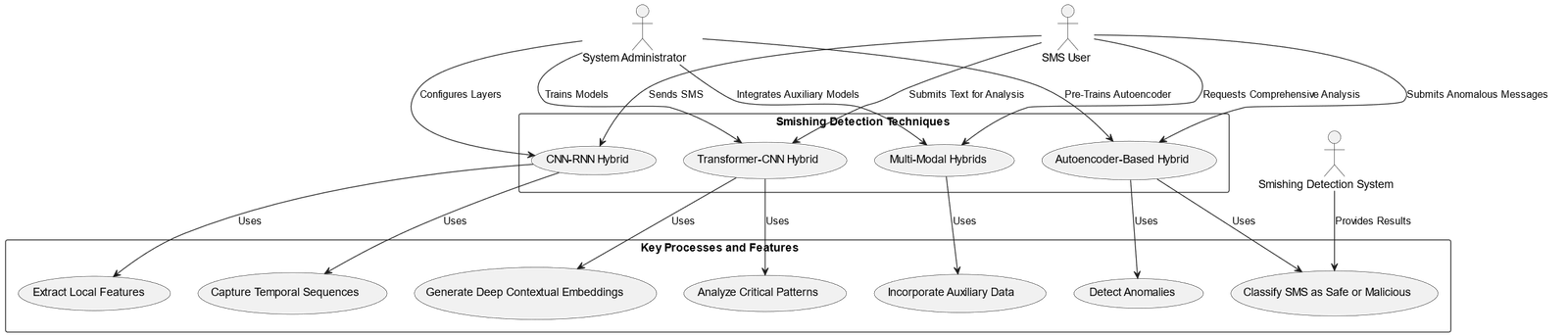
Whereas an RNN or LSTM layer records the temporal sequence of words, a CNN layer extracts local characteristics from SMS text. This combination guarantees the recognition of delicate patterns as well as interpretation of the broader context of a conversation. To locate deep contextual embedded values, transformers analyse the SMS text. After that, a CNN layer is applied to these embeddings in order to highlight important smishing-related patterns or characteristics. For the analysis of sender connections, integrate text-based architectures with auxiliary data models like Graph Neural Networks (GNNs). By using several data dimensions, this method expands the detection breadth. To find abnormalities in SMS messages, an autoencoder might be utilized as a pre-training phase. For ultimate categorization, the autoencoder’s output is then fed into a deep learning model, such a Transformer [8]. Details shown in in figure 2.
Conclusion:
A comprehensive, scalable, and flexible solution to one of the most urgent cybersecurity risks in SMS communication is provided by hybrid deep learning architectures, which mark a paradigm leap in smishing detection. These architectures enable immediate identification and mitigation of smishing attacks by combining secondary knowledge and exploiting the benefits of numerous machine learning models. Research and innovation in hybrid architectures will be crucial to staying ahead of counterfeiters as the threat landscape changes.
Reference:
- Md. R. H. K. Rakib, S. A. K. Pramanik, Md. A. Amran, Md. N. Islam, and Md. O. F. Sarker, “Factors affecting young customers’ smartphone purchase intention during Covid-19 pandemic,” Heliyon, vol. 8, no. 9, p. e10599, Sep. 2022, doi: 10.1016/j.heliyon.2022.e10599.
- S. Rommer, P. Hedman, M. Olsson, L. Frid, S. Sultana, and C. Mulligan, “Chapter 3 – Architecture overview,” in 5G Core Networks, S. Rommer, P. Hedman, M. Olsson, L. Frid, S. Sultana, and C. Mulligan, Eds., Academic Press, 2020, pp. 15–72. doi: 10.1016/B978-0-08-103009-7.00003-X.
- S. Knight, “How Many Text Messages Are Sent a Day? (2024 Statistics),” SellCell.com Blog. Accessed: Feb. 04, 2025. [Online]. Available: https://www.sellcell.com/blog/how-many-text-messages-are-sent-a-day-2023-statistics/
- A. Joseph, “Middle East businesses determined to enhance cybersecurity readiness: Kaspersky,” TahawulTech.com. Accessed: Feb. 04, 2025. [Online]. Available: https://www.tahawultech.com/news/middle-east-businesses-determined-to-enhance-cybersecurity-readiness-kaspersky/
- “CrowdStrike 2024 Global Threat Report.” Accessed: Feb. 04, 2025. [Online]. Available: https://go.crowdstrike.com/global-threat-report-2024.html?utm_campaign=cao&utm_content=crwd-cao-apj-sea-en-psp-x-wht-gtr-tct-x_x_x_x-x&utm_medium=sem&utm_source=goog&utm_term=global%20threat%20report&cq_cmp=10902423317&cq_plac=&gad_source=1&gclid=CjwKCAiA74G9BhAEEiwA8kNfpQjYgYW84wWN7Z6RD2k6r0UCKLq3c8R9THPWsyZIX7A91eDktow6_xoCq6EQAvD_BwE
- A. Redhu, P. Choudhary, K. Srinivasan, and T. K. Das, “Deep learning-powered malware detection in cyberspace: a contemporary review,” Front. Phys., vol. 12, Mar. 2024, doi: 10.3389/fphy.2024.1349463.
- C. Chakraborty, M. Bhattacharya, S. Pal, and S.-S. Lee, “From machine learning to deep learning: Advances of the recent data-driven paradigm shift in medicine and healthcare,” Current Research in Biotechnology, vol. 7, p. 100164, Jan. 2024, doi: 10.1016/j.crbiot.2023.100164.
- S. Markkandeyan, A. D. Ananth, M. Rajakumaran, R. G. Gokila, R. Venkatesan, and B. Lakshmi, “Novel hybrid deep learning based cyber security threat detection model with optimization algorithm,” Cyber Security and Applications, vol. 3, p. 100075, Dec. 2025, doi: 10.1016/j.csa.2024.100075.
- Kee S.N. (2024) The Role of Blockchain in Enhancing Cloud Security against Phishing Attacks, Insights2Techinfo, pp.1
Cite As
Rahaman M. (2025) Hybrid Deep Learning Architectures for Smishing Detection in SMS Communication, Insights2Techinfo, pp.1