By: B. Gupta
It is an easy task to identify if a web site is vulnerable to XSS attack. Various web application vulnerability scanners are available that assist in the identification of hidden vulnerabilities (web application vulnerability scanner list). Some of them are commercial tools, while some are open-source tools.
XSS attack occurs because of improper verification of the input values. Attacker takes advantage of this flaw and injects malicious script code, say, ‘><script>alert(‘XSS’)</script>. It is then executed in the same way as the legitimate JavaScript code, so the attacker is able to gain access to the sensitive information of the victim. Below are the steps to examine manually whether a Web site is vulnerable to XSS or not.
- Manual testing for XSS vulnerability requires searching for any entry point i.e., input field in the web page, for example, search box, comment box, etc.

- Now, submit any arbitrary malicious script code. First try with simple string like <script>alert(“XSS”)</script> in any input field
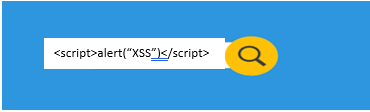
- Check if the submitted string value appears on the web page. If it is appearing then it is XSS vulnerable.

- Test for other fields also identify whether the maliciously crafted script gets executed in the web browser.
Thus, in this way, you can assess the web site for hidden XSS vulnerability. You can try XSS payloads having different context and use any to test for XSS attack.
RELATED ARTICLES
- More on XSS vulnerability. Cross Site Scripting (XSS) Software Attack | OWASP Foundation
- XSS cheat sheet. XSS Filter Evasion Cheat Sheet | OWASP
- Latest XSS incidents (CVE information). CVE-XSS attack.