By: Gonipalli Bharath, Vel Tech University, Chennai, India, International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Distributed Denial-of-Service attacks pose one of the current serious threats to modern digital infrastructures. The traditional mechanisms used for defence seem incapable of handling the ever-changing nature of the attacks. In this regard, Machine Learning represents a dynamic and adaptive approach for real-time DDoS attack detection and mitigation. This paper revisits several machine learning techniques applied in cyber defences, revisits the related literature, and after that proposes some methodology that could be followed for the implementation of ML-based DDoS detection systems.
Introduction:
DDoS overloads the target system with undue traffic and causes service disruptions. Traditional security controls, which include firewalls and intrusion detection systems, usually use signature techniques that fail commonly in case of sophisticated patterns of attack. In such cases, ML-based solutions provide intelligence that can identify DDoS threats and mitigate the risk by learning from previous patterns of attack and adapting to newer ones [[1]].
Literature Review:
The incorporation of ML methods in SDN has opened new dimensions for proactive and reactive approaches against DDoS attacks. Several ML algorithms have been tried with good performance metrics, which reflects considerable improvement in accuracy, speed, and adaptability compared to traditional methods [[2]]. Algorithms of Supervised Learning that are in wide use in this area include Support Vector Machines, Decision Trees, and Random Forests. These algorithms benefit greatly from the labeled datasets they use to learn patterns of normal and malicious traffic [[3]].
Techniques of k-means clustering and methods of anomaly detection have become quite vital in cases with limited labeled data. They allow identification of unprecedented patterns of an attack and help dynamic adaptation in respect to new, unseen threats [[4]]. The use of deep learning models, such as those using neural networks, has been on the increase due to their capabilities in automatic feature extraction and the capture of complicated patterns within large datasets for high detection rates. CNNs and RNNs have yielded robust results for temporal traffic analysis. More recent research has focused on putting together a few algorithms to better exploit each of their strengths. As an example, an ensemble technique that combines decision trees with neural networks can leverage the interpretability from tree-based methods and the accuracy of deep learning [[5]].
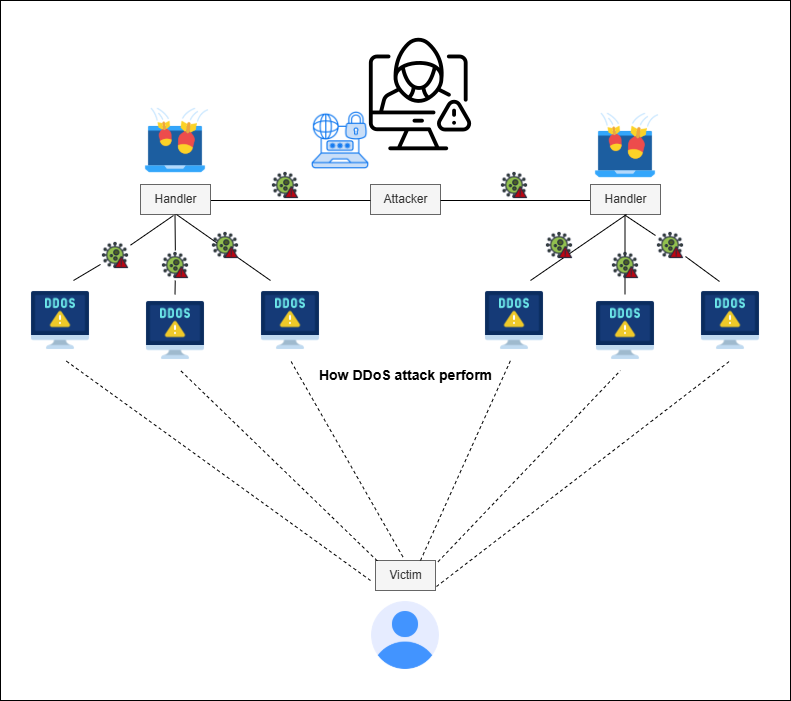
Fig[[6]]
Methodology:
The process of implementing a DDoS detection system supported by ML falls into a rather structured approach: data collection will be done based on network traffic data from reliable sources, namely the CIC-DDoS2019 dataset. This data was collected by varying the attack pattern and normal samples of traffic; thus, giving the model much to learn from. The critical parameters are identified: packet size, request frequency, source IP behaviour, and protocol usage, which enable the differentiation of legitimate traffic from malicious ones. Cleaning the raw data, further normalization, and division into training and test sets is a way to preprocess the data for model efficiency. It reduces the noise and improves model generalization. This is then followed by the selection of models that involves checking different ML techniques, such as Random Forest, SVM, CNNs, or hybrid models. Each model must be trained by labeled data to make it further perform better. Later on, it will be evaluated based on the standard metric: accuracy, precision, recall, F1-score, helping to illustrate how well this system works in DDoS attack detection and reduces the percentage of false positive rates. Finally, deployment of the trained model is done within a real-time network monitoring system. That way, the traffic will be kept under constant surveillance, where the model itself will proactively detect and mitigate DDoS attacks while they are occurring. The deployed system can further be optimized by reinforcement learning to adapt to new attack strategies dynamically.
Table Representation of Final Outcomes of Different ML Algorithms:(Review)[[7]]
Algorithm Type | Specific Algorithms | Detection Accuracy (%) | Response Time (ms) | Advantages |
Supervised Learning | SVM Decision Tree Random Forest | 95.2 92.0 94.5 | 100 80 90 | SVM- High accuracy with clear decision boundaries. Decision Tree-Easy to interpret, fast training. RF- Reduces overfitting, handles large datasets |
Unsupervised Learning | k-means Clustering Anomaly Detection | 85.0 88.0 | 150 120 | k-means Clustering- No need for labeled data. Anomaly Detection-Detects novel attacks. |
Deep Learning | CNN RNN | 96.5 95.0 | 120 130 | CNN- Effective in capturing spatial dependencies. RNN- Great for handling sequential data. |
Hybrid Approaches | Ensemble Methods | 97.0 | 125 | Improved accuracy and robustness. |
Conclusion:
Machine Learning has really revolutionized the art of approach towards mitigating DDoS attacks by real-time threat detection and response. Though different machine learning techniques offer various advantages, hybrid models give the best trade-off between accuracy and efficiency. Future research is needed in enhancing the generalization ability of models and reducing the computational cost of security mechanisms. This would mean that by integrating ML-driven solutions, a robustly secure network infrastructure can proactively protect an organization’s digital assets from up-and-coming DDoS threats.
References:
- Ahmed, Usama, Mohammad Nazir, Amna Sarwar, Tariq Ali, El-Hadi M. Aggoune, Tariq Shahzad, and Muhammad Adnan Khan. “Signature-Based Intrusion Detection Using Machine Learning and Deep Learning Approaches Empowered with Fuzzy Clustering.” Scientific Reports 15, no. 1 (January 11, 2025): 1726. https://doi.org/10.1038/s41598-025-85866-7.
- Aljuhani, Ahamed. “Machine Learning Approaches for Combating Distributed Denial of Service Attacks in Modern Networking Environments.” IEEE Access 9 (2021): 42236–64. https://doi.org/10.1109/ACCESS.2021.3062909.
- Aslan, Ömer, Semih Serkant Aktuğ, Merve Ozkan-Okay, Abdullah Asim Yilmaz, and Erdal Akin. “A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions.” Electronics 12, no. 6 (January 2023): 1333. https://doi.org/10.3390/electronics12061333.
- Bawany, Narmeen Zakaria, Jawwad A. Shamsi, and Khaled Salah. “DDoS Attack Detection and Mitigation Using SDN: Methods, Practices, and Solutions.” Arabian Journal for Science and Engineering 42, no. 2 (February 1, 2017): 425–41. https://doi.org/10.1007/s13369-017-2414-5.
- Saranya, T., S. Sridevi, C. Deisy, Tran Duc Chung, and M. K. A. Ahamed Khan. “Performance Analysis of Machine Learning Algorithms in Intrusion Detection System: A Review.” Procedia Computer Science, Third International Conference on Computing and Network Communications (CoCoNet’19), 171 (January 1, 2020): 1251–60. https://doi.org/10.1016/j.procs.2020.04.133.
- Singh, Jagdeep, and Sunny Behal. “Detection and Mitigation of DDoS Attacks in SDN: A Comprehensive Review, Research Challenges and Future Directions.” Computer Science Review 37 (August 1, 2020): 100279. https://doi.org/10.1016/j.cosrev.2020.100279.
- Ömer Aslan et al., “A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions,” Electronics 12, no. 6 (January 2023): 1333, https://doi.org/10.3390/electronics12061333. ↑
Narmeen Zakaria Bawany, Jawwad A. Shamsi, and Khaled Salah, “DDoS Attack Detection and Mitigation Using SDN: Methods, Practices, and Solutions,” Arabian Journal for Science and Engineering 42, no. 2 (February 1, 2017): 425–41, https://doi.org/10.1007/s13369-017-2414-5. ↑
T. Saranya et al., “Performance Analysis of Machine Learning Algorithms in Intrusion Detection System: A Review,” Procedia Computer Science, Third International Conference on Computing and Network Communications (CoCoNet’19), 171 (January 1, 2020): 1251–60, https://doi.org/10.1016/j.procs.2020.04.133. ↑
Usama Ahmed et al., “Signature-Based Intrusion Detection Using Machine Learning and Deep Learning Approaches Empowered with Fuzzy Clustering,” Scientific Reports 15, no. 1 (January 11, 2025): 1726, https://doi.org/10.1038/s41598-025-85866-7. ↑
Jagdeep Singh and Sunny Behal, “Detection and Mitigation of DDoS Attacks in SDN: A Comprehensive Review, Research Challenges and Future Directions,” Computer Science Review 37 (August 1, 2020): 100279, https://doi.org/10.1016/j.cosrev.2020.100279. ↑
Ahamed Aljuhani, “Machine Learning Approaches for Combating Distributed Denial of Service Attacks in Modern Networking Environments,” IEEE Access 9 (2021): 42236–64, https://doi.org/10.1109/ACCESS.2021.3062909. ↑
Singh and Behal, “Detection and Mitigation of DDoS Attacks in SDN.” ↑
- Zou, L., Sun, J., Gao, M., Wan, W., & Gupta, B. B. (2019). A novel coverless information hiding method based on the average pixel value of the sub-images. Multimedia tools and applications, 78, 7965-7980.
- Sahoo, S. R., & Gupta, B. B. (2019). Hybrid approach for detection of malicious profiles in twitter. Computers & Electrical Engineering, 76, 65-81.
- Rahaman M. (2025) Hybrid Deep Learning Architectures for Smishing Detection in SMS Communication, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Mitigating DDoS Attacks: How Machine Learning Enhances Cyber Defense, Insights2Techinfo, pp.1