By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
While the growth of digital communication has also dramatically increased phishing attacks, they now pose a critical threat to people and organizations globally. The paper reviews some of the comprehensive recommendations for distinguishing phishing from real messages and lays more emphasis on awareness and preventive measures. The research makes use of present patterns, technological instruments, and useful methods of verification in trying to get users the much-needed information they require to help protect their online interactions. Identification of alerts, use of tools for verification, and conduction of the best practices over the internet remain important tactics. For improving digital literacy and decreasing risk to online scams, this resource is an essential tool.
Introduction
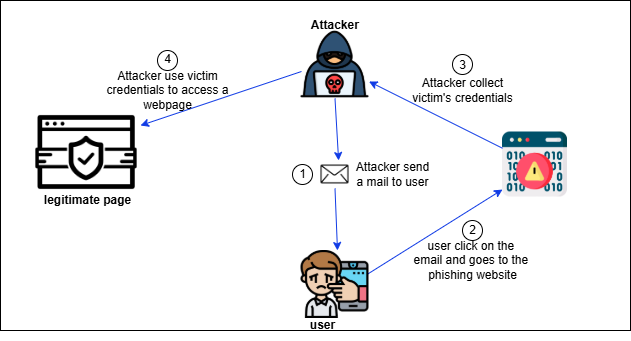
With greater connectivity of the world today, internet communication plays a vital role both in personal and professional spheres. However, the ever-increasing rates of phishing attacks have raised severe concerns regarding cybersecurity. Phishing is a deceptive way of collecting private data related to financial information and passwords through impersonation of reputed organizations. Since most of the users cannot identify phishing attempts, the human factor remains a significant vulnerability apart from technological developments in cybersecurity. In order to close this gap and encourage safer online behavior, this source material provides practical advice on how to spot phishing emails from authentic ones.
Literature review
In the context of cybersecurity, phishing has been thoroughly examined, with researchers highlighting its increasing difficulty. It frequently takes some time for technical solutions to identify and filter out phishing emails after they arrive in inboxes[1].
They are two types of list-based approaches they are whitelisting and blacklisting. The whitelist contains a list of valid URLs that browsers can access. You can download the web page, at the same time blacklisting includes phishing or fraud URLs[2].
Identity-based phishing detection methods are: Textual or visual brand identities can be used to implement identity-based phishing detection techniques. Methods that use textual identities for brands are covered first, then visual identities for brands, and finally a mix of the two[3].
Despite these initiatives, there is still a gap in the conversion of academic understanding into useful, approachable recommendations. By combining current research with practical methods for confirming online communications, this work aims to close this gap.
The difference between phishing and legitimate
Phishing (Spam emails) | Legitimate email |
Phishing emails look authentic, but they are really attempts to obtain your personal information or steal your money. | “Legitimate Email” describes emails sent by recognized senders who have been verified by DNS-based email sender authentication systems. |
Methodology
Using a mixed-methods approach, this study evaluates user behaviors and responses to simulated phishing efforts statistically while qualitatively analyzing phishing case studies. Publicly available reports on phishing trends, phishing email analysis, and user surveys are some examples of data sources. To enable users to recognize and successfully reduce phishing risks, the results are condensed into a useful manual.
Conclusion
In the digital era, phishing is still a common problem that calls for a knowledgeable and proactive approach to online communication. This manual offers a useful foundation for spotting phishing efforts, stressing the value of being alert doing your research, and using cybersecurity tools. Users can greatly increase their resistance to online scams by putting the tactics described in this paper into practice, which will help create a safer online environment. Addressing the changing nature of phishing threats requires ongoing awareness and education efforts.
Reference
- M. Mossano, K. Vaniea, L. Aldag, R. Düzgün, P. Mayer, and M. Volkamer, “Analysis of publicly available anti-phishing webpages: contradicting information, lack of concrete advice and very narrow attack vector,” in 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Sep. 2020, pp. 130–139. doi: 10.1109/EuroSPW51379.2020.00026.
- “1-s2.0-S1319157823000034-main.pdf,” Google Docs. Accessed: Dec. 31, 2024. [Online]. Available: https://drive.google.com/file/d/1MDEx5x-NKLxo6N4juLonU7LGxtdgv1HK/view?usp=drive_web&usp=embed_facebook
- “1-s2.0-S0957417423002245-main.pdf,” Google Docs. Accessed: Dec. 31, 2024. [Online]. Available: https://drive.google.com/file/d/1FiMkBLYNCINtF4HYtp8ml55aUuLbEwpg/view?usp=drive_web&usp=embed_facebook
- “What is Phishing Attack? Types and Examples.” Accessed: Dec. 31, 2024. [Online]. Available: https://www.wallarm.com/what/types-of-phishing-attacks-and-business-impact
- Al-Ayyoub, M., AlZu’bi, S., Jararweh, Y., Shehab, M. A., & Gupta, B. B. (2018). Accelerating 3D medical volume segmentation using GPUs. Multimedia Tools and Applications, 77, 4939-4958.
- Tewari, A., & Gupta, B. B. (2017). A lightweight mutual authentication protocol based on elliptic curve cryptography for IoT devices. International Journal of Advanced Intelligence Paradigms, 9(2-3), 111-121.
- REDDY K.T (2024) Unravelling Behavioural Analysis in Phishing Detection, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) Phishing or legit? A guide to verify online communications, Insights2techinfo pp.1