By: KUKUTLA TEJONATH REDDY, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, tejonath45@gmail.com
Abstract:
As mobile devices have become essential in the digital landscape, they are vulnerable to attacks, posing serious cybersecurity risks. This article examines the critical role of behavioural analytics for mobile phishing detection, providing detailed insights into its methods and techniques Behavioural analytics, a proactive approach, is the study of user behaviour patterns for detection anomalies that could indicate phishing attempts the process includes data collection, preprocessing, modeling user behaviour, anomaly identification, and subsequent resolution of phishing’s. By examining real-world examples and case studies, this article highlights the importance of mobile phishing detection. Through an in-depth analysis of common phishing techniques, the article demonstrates how behavioural analysis works as a powerful security device. To protect sensitive information and ensure digital security, this article provides a comprehensive understanding of behavioural analysis to detect mobile phishing, empowering readers with the knowledge to create their digital assets protection.
Introduction:
Mobile devices have become an integral part of our daily lives in today’s digital age, facilitating communication, financial transactions and sensitive information but the widespread use of mobile devices poses cybersecurity threats, especially mobile phishing attacks Moreover have become sophisticated, requiring more sophisticated detection techniques Improved cybersecurity screening approach Behavioural analysis plays an important role in identifying and mitigating these threats.
Understanding Behavioural Analysis:
Behavioural analysis is a technique used in mobile phishing detection that identifies changes in user behaviour that indicate a phishing attempt. Unlike traditional methods that rely on fixed indicators such as known malicious websites, behavioural analysis focuses this way on the dynamic aspects of the user interface highlights the fluid elements of user interaction, and provides powerful and effective defence mechanisms.
The Process of Behavioural Analysis:
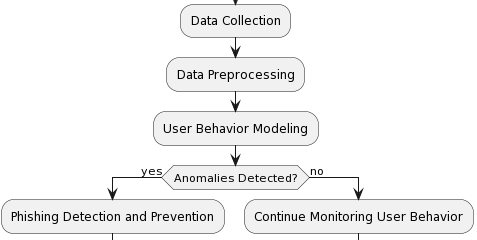
Data Collection: The initial step in behavioural analysis involves gathering data from diverse sources, encompassing user interactions, device configurations, network activities, and application usage. This collected data serves as the foundation for analysing user behaviour patterns.
Data Preprocessing: After collecting data, the information undergoes a series of essential steps. These include cleaning, transforming, and normalizing the data, which aims to remove any inconsistencies and discrepancies. This meticulous preprocessing procedure enhances the data quality, rendering it suitable for behavioral analysis algorithms.
User Behaviour Modeling: Behavioural models are developed through the analysis of commonly used behaviours. Machine learning algorithms and statistical methods are used to identify specific user behaviours, and serve as a baseline for comparison.
Anomaly Detection: Anomalies and deviations are detected by comparing real-time user behavior with established patterns. Suspicious activity, such as unexpected clicks on links or unusual access triggers alerts for further investigation.
Phishing detection and prevention: When the system detects potentially malicious behaviour, it can take a variety of actions, such as alerting the user, blocking suspicious activity, or triggering additional validation steps to ensure that user identity.
Importance of Mobile Phishing Detection:
Mobile phishing attacks include unauthorized access to personal and financial information, identity theft, and financial fraud. Detecting and preventing these attacks is of utmost importance protecting individuals, businesses and organizations from catastrophic consequences.
General Phishing Tactics and Behavioural Analysis:
Spear Phishing:
Attackers target specific individuals or organizations, designing their phishing efforts to appear more credible. Behavioural analysis can detect unusual communication patterns or unexpected requests, flagging them as possible spear phishing attempts [7].
Smishing (SMS Phishing):
Phishers use text messages to trick users into clicking malicious links. Behavioural analytics can identify unusual click patterns, enabling the identification of attempted attempts based on unusual user behaviour [8].
Vishing (Voice Phishing):
Attackers use voice communication to trick users into revealing sensitive information. Behavioural analysis analyses the call patterns and responses of the user to detect threatening voice hacking attempts [9].
Conclusion:
Behavioural analytics for mobile phishing detection is at the forefront of cybersecurity, providing proactive protection against persistent phishing techniques by understanding user behaviour, detecting anomalies, with the use of advanced algorithms, cybersecurity professionals who disrupt mobile phishing attacks for users and organizations Protect against consequences as technology advances, so does phishing effort will also be. Thus, investing in behavioural analytics techniques is not just a safety measure but a necessity in our interconnected digital world. Stay vigilant, understand the risks, and embrace the power of behavioural analytics to protect your digital domain.
References:
- Ryu, H. R., Hong, M., & Kwon, T. (2014). Behavioural Analysis of Password Authentication and Countermeasure to Phishing Attacks-from User Experience and HCI Perspectives. Journal of Internet Computing and Services, 15(3), 79-90.
- Alam, M. N., Sarma, D., Lima, F. F., Saha, I., & Hossain, S. (2020, August). Phishing attacks detection using machine learning approach. In 2020 third international conference on smart systems and inventive technology (ICSSIT) (pp. 1173-1179). IEEE.
- Shahbaznezhad, H., Kolini, F., & Rashidirad, M. (2021). Employees’ behavior in phishing attacks: what individual, organizational, and technological factors matter?. Journal of Computer Information Systems, 61(6), 539-550.
- Katipally, R., Yang, L., & Liu, A. (2011, October). Attacker behavior analysis in multi-stage attack detection system. In Proceedings of the seventh annual workshop on cyber security and information intelligence research (pp. 1-1).
- Sanders, D. (2010). Behavioural analysis. Theory and methods in political science, 23-41.
- James, R. J., & Tunney, R. J. (2017). The need for a behavioural analysis of behavioural addictions. Clinical Psychology Review, 52, 69-76.
- Bhavsar, V., Kadlak, A., & Sharma, S. (2018). Study on phishing attacks. International Journal of Computer Applications, 182(33), 27-29.
- Banu, M. N., & Banu, S. M. (2013). A comprehensive study of phishing attacks. International Journal of Computer Science and Information Technologies, 4(6), 783-786.
- Alabdan, R. (2020). Phishing attacks survey: Types, vectors, and technical approaches. Future internet, 12(10), 168.
- Wang, L., Li, L., Li, J., Li, J., Gupta, B. B., & Liu, X. (2018). Compressive sensing of medical images with confidentially homomorphic aggregations. IEEE Internet of Things Journal, 6(2), 1402-1409.
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). InFeMo: flexible big data management through a federated cloud system. ACM Transactions on Internet Technology (TOIT), 22(2), 1-22.
- Gupta, B. B., Perez, G. M., Agrawal, D. P., & Gupta, D. (2020). Handbook of computer networks and cyber security. Springer, 10, 978-3.
- Bhushan, K., & Gupta, B. B. (2017). Security challenges in cloud computing: state-of-art. International Journal of Big Data Intelligence, 4(2), 81-107.
Cite As
REDDY K.T (2024) Unravelling Behavioural Analysis in Phishing Detection, Insights2Techinfo, pp.1