By: Aiyaan Hasan, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, rayhasan114@gmail.com
Abstract
As Internet of things (IoT) carries on with its expansion in this technologically advanced world, there’s an increasing need for efficiency and the privacy-preserving machine learning on the IoT devices, making it of paramount importance. Security issues, Concerns related to privacy, and the nature of the IoT data have eventually led to the development of privacy- preserving federated learning as a solution which is quite promising. In this article we shall explore the challenges, opportunities and implementation of federated learning in the IoT networks while preserving data.
Introduction
The internet of things (IoT) is particularly the network of objects (physical)- instruments, vehicle, devices, buildings and other items which are embedded with the circuits, electronics, software and even network and connectivity which makes these objects capable of the collection of data and the exchange of data too.[1] The idea is that IoT is virtually connecting every physical entity in this world and therefore is capable of making this entire world a computer which is connected to the internet.[2]
IoT is often referred to as the third big wave of scientific and economic wave after the computer and internet.[3] The emergence of these IoT devices has transformed the way we are currently interacting with this physical world. Be it smart thermostats or wearable fitness trackers, we are surrounded by IoT devices which withhold within themselves enormous amounts of data which has tremendous potential. However, this ocean of data is vulnerable and raises significant concerns related to privacy and security. IoT has a lot of applications in our society, such as the GPS-equipped vehicles for transport and so much more.[4] The results of IoT failures can be lethal and therefore, studying and researching in the IoT domain becomes of significance importance. They key objective over here is basically to preserve the user-privacy, confidentiality, ensuring that users have no security related issues, infrastructures and much more.[5]
Traditional machine learning involves the centralization of data in order to train the model, which might not be the most suitable way of training an IoT device for its respective purpose. Centralization of information and data is something which is concerning as it may cause privacy breaches and scalability challenges. In this scenario Privacy-preserving federated learning plays a crucial role and acts as a promising alternative to allow machine learning models to be trained on data sources which are decentralized.
Challenges in IoT-Federated learning
- Data-sources:
- Diverse Devices: IoT networks consists of a wide spectrum of devices, which ranges from sensors to smartphones and wearable tech. Each particular device is capable of generating data with different scales and formats. In order to handle this data, it becomes a major challenge when it comes to federated learning.
- Data Quality: Data that is being generated by these IoT devices can vary in different parameters such as quality, accuracy, and even its overall completeness. Therefore, these federated learning models should be robust enough in order to handle the noise present inside the data and incomplete data as well.
2) Communication:
- Limited Bandwidth: There are many IoT devices which are operating in environments which possess limited bandwidth, for example: remote sensors in agriculture or industrial settings. Frequent updates in federated learning can also lead to the consumption of crucial bandwidth resources.
- Latency: When it comes to IoT networks, we often experience latency issues (high) because of factors such as network congestion and long-distance communication. While most of the computer related performance parameters have gotten better drastically, the latency of network communication has not.
| 1983 | 2011 | Improved | |
| CPU SPEED | 1x10Mhz | 4x3GHz | > 1,000x |
| Memory Size | ≤ 2MB | 8GB | ≥ 4,000x |
| Disk capacity | ≤ 30MB | 2TB | > 60,000x |
| Network Bwidth | 3Mbps | 10Gbps | > 3,000x |
| RTT | 2.54ms | 80µs | 32x |
Figure 1: Shows the improvement of network latency which has evolved far less slowly in terms of performance over the past 3 decades.[6]
3) Privacy Preservation:
- Sensitive data: Data contained in these IoT devices is often sensitive, for example: Personal health records, location related data, process-oriented details. Protecting such vulnerable data is of paramount importance.
- Regulations: Compliance with respect to the data privacy regulations, such as GDPR (general data protection regulation) in European union, which blends complexity into the implementation of the federated learning in IoT.
4) Resource Constraints:
- Limited computational power: There are multiple IoT devices, such as sensors and the edge devices, which have limited computational resources. These constraints particularly require the design of the federated learning algorithms that are resource- efficient.
- Energy Efficiency: IoT devices are mostly battery powered and they can be operated from remote locations as well. Therefore, the federated learning algorithms require themselves to energy-efficient and need to possess a definite amount of lifespan for optimal functioning.
5) Security related issues and risks:
- Device security: IoT devices are prone to security vulnerabilities and therefore can be compromised by the attackers. Ensuring that the security of these devices which are participating in federated learning is crucial in order to prevent any malicious attacks.
- Model Security: The security of models based on machine learning and the model updates during federated learning is also concern.
6) Scalability:
- Scaling Up: As the number of devices based on IoT in a network increase, the scalability of the federated learning becomes challenging.
7) Interoperability:
- Diverse Protocols: The IoT devices are often used in communication protocols which ensure compatibility between these devices and federated learning-based systems.
Federated learning has gained a reputation not just for building Machine learning models which particularly are dependent on datasets which are distributed, in order to play a key role when it comes to privacy solutions and security to sensitive data and information based on a variety of Machine learning related attacks. This Makes it an ideal choice for evolving networks, in this case, Internet of things (IoT). [7-12]
Privacy-Preserving Techniques in Federated Learning:
The Privacy-Preserving Techniques in Federated Learning are essential for the purpose of safeguarding the integrity of data which is sensitive while simultaneously allowing parties which are decentralized to be collaborating with the machine learning models. These techniques are addressed in as follows:
- Differential Privacy: It is a foundational and conventional privacy preserving technique that is particularly used in order to add noise in a controlled manner to data to prevent any extraction of information from the data. With respect to federated learning, it can be utilized to protect the privacy of the device data wile model is being trained and thereafter in aggregation of updates.
- Privacy assurance: Differential privacy ensures the privacy of individual data points with the utilization of strong mathematics.
- Noise addition: When the model is being updated during the aggregation process, each individual device is adding random noise to its update before sharing it with its respective server (central).
- Aggregated noise: The central server is basically aggregating the updates that are noisy in nature from multiple devices and as the number keeps increasing, the aggregated noise decreases and eventually is cancelled out.
- Homomorphic encryption: It is based on cryptographic techniques that allows the computation to be performed on data which is encrypted and that too without decrypting it directly. In federated learning, this can be used to protect the privacy of data that is present on IoT devices as well as the model updates during the process of aggregation.
- Secure computation: IoT devices basically encrypting their data and are sending it to the central server, and this is where the computations happen over the encrypted data without being able to access the data.
- Privacy-Preserving Aggregation: The model updates from the devices can ensure encryption, and aggregation can even occur in these encrypted domains.
c. Types of Homomorphic Encryption:
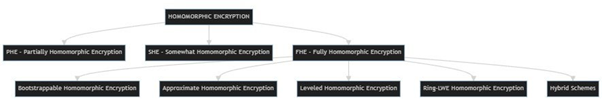
- Secure Aggregation: Techniques that includes Secure Multi-Party Computation (SMPC), aiming to aggregate model updates from multiple devices as it simultaneously preserves the privacy of their users. These methods are ensuring that the aggregation result does not reveal the individual contribution of data to individual contribution of data to anyone.
Conclusion
Privacy-preserving federated learning is promising when it comes to addressing the challenges of specifically training the machine learning models which are based of IoT devices and simultaneously maintaining and safeguarding privacy. With the utilization of techniques such as differential privacy, homomorphic encryption, and secure aggregation, researchers and the practitioners are enabling security in terms of IoT related data for machine learning and their applications.
The future of federated learning is bright and promising, but in order to maintain that legacy it requires consistent transparency, accountability and fairness. Collaboration with respect to the stakeholders and the advancements in privacy-preserving techniques and security measures, shall remain the pillars upon which federated learning continues its journey.
References
- https://www.researchgate.net/profile/Omkar- Bhat/publication/330114646_Introduction_to_IOT/links/5c2e31cf299bf12be3ab21eb/Introdu ction-to-IOT.pdf
- The study and application of the IOT technology in agriculture. (2010, July 1). IEEE Conference Publication | IEEE Xplore. https://ieeexplore.ieee.org/abstract/document/5565120
- Study and application on the architecture and key technologies for IOT. (2011, July 1). IEEE Conference Publication | IEEE Xplore. https://ieeexplore.ieee.org/abstract/document/6002149
- The application and development of IOT. (2012, August 1). IEEE Conference Publication| IEEE Xplore. https://ieeexplore.ieee.org/abstract/document/6291468
- Noor, M. B. M., & Hassan, W. H. (2019, January 1). Current research on Internet of Things (IoT) security: A survey. Computer Networks; Elsevier BV. https://doi.org/10.1016/j.comnet.2018.11.025
- https://www.irjmets.com/uploadedfiles/paper//issue_5_may_2023/38894/final/fin_irjmets168 3972606.pdf. (2023, May 13). International Research Journal of Modernization in Engineering Technology and Science. https://doi.org/10.56726/irjmets38894
- Chaudhry, A. F., Aniol, H., & Shegos, C. J. (2020). https://www.consultant360.com/article/consultant360/congenital-hypothyroidism-due- thyroid-agenesis. Consultant. https://doi.org/10.25270/con.2020.05.00011
- Gupta, B. B., & Lytras, M. D. (2022). Fog-enabled secure and efficient fine-grained searchable data sharing and management scheme for IoT-based healthcare systems. IEEE Transactions on Engineering Management
- Dahiya, A., Gupta, B. B., Alhalabi, W., & Ulrichd, K. (2022). A comprehensive analysis of blockchain and its applications in intelligent systems based on IoT, cloud and social media. International Journal of Intelligent Systems, 37(12), 11037-11077.
- Cvitić, I., Peraković, D., Periša, M., & Gupta, B. (2021). Ensemble machine learning approach for classification of IoT devices in smart home. International Journal of Machine Learning and Cybernetics, 12(11), 3179-3202.
- Al-Qerem, A., Alauthman, M., Almomani, A., & Gupta, B. B. (2020). IoT transaction processing through cooperative concurrency control on fog–cloud computing environment. Soft Computing, 24(8), 5695-5711.
- Gupta, B. B., & Quamara, M. (2020). An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurrency and Computation: Practice and Experience, 32(21), e4946
Cite As:
Hasan A. (2023) Privacy-Preserving Federated Learning for IoT Networks, Insights2Techinfo, pp.1