By: Nicko Cajes; Northern Bukidnon State College, Philippines
Abstract
In cybersecurity field, one of the growing threats that takes a lot of attention is the ransomware attack, which can encrypt files and will also demand for the ransom payment in order to decrypt them. This attack can spread through phishing, malicious links, and software vulnerabilities. He idea of paying the ransom can’t also be appropriate, as it can result to a lot of consequences which typically received by you, such as being treated as part of the criminals. However, Strategies in the prevention of being attacked by this can also be implemented such as baking up, updating, and being wary of what you are doing online.
Introduction
Imagine you are having a wonderful dream, in which you are so happy and wished that it will never last. There comes the morning, and you wake up and after turning on your computer you see a terrifying message stating “Your important files have been encrypted, pay me $100000 in Bitcoin and I will decrypt them.” The message that you are seeing is definitely a Ransomware attack. Ransomware have grown enormously in the recent years, which targets individuals, organizations, and even the government [1]. Attackers utilized this type of attack to lock the victims out of their computer. This can result to a devastating consequence, potentially losing your personal data, important information and complete shutdown of your device [2]. But what exactly is ransomware? How is it working? And the most important thing, how can we protect ourselves and avoid being a victim of the attack? Well, we will answer all of that in this paper.

What is Ransomware?
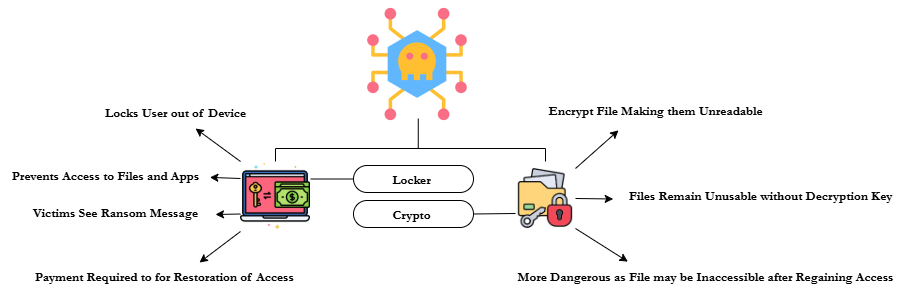
Ransomware is a novel type of malicious software which was primarily designed to make the victim unable to access their system or basically encrypting the victims file until the requested ransom is being paid. Attackers will typically demand a payment using cryptocurrency methods like Bitcoin as with the use of it, it is more difficult to trace them [3]. Ransomwares have two main types, and this is the Locker Ransomware and Crypto Ransomware.
Locker Ransomware: From the word locker itself, locker ransomware is the type of ransomware that lock users away from their devices, this attack will prevent the user from using his/her devices, files, or application. The victims can usually see a message in their screen that they are being a target of a ransomware, and they need to pay for it before they can gain the control of their device back [4].
Crypto Ransomware: Crypto Ransomware is another type of ransomware, in this attack, the attackers will encrypt the files of the system, making it unreadable and will remain in that state if the decryption key is not shared. Ransomware that was conducted in this type is far more dangerous, as even when the time that you have already regain the access of your computer, your files will be just a storage eater in your device because it is not readable unless you have the decryption key [5].
One of the most infamous ransomware attacks that happened in the past is the WannaCry in 2017, which have spread across 150 countries and have infected on over 200,000 computers, this attack exploited a vulnerability in a Windows system, making the attacker encrypt their files and demand a bitcoin payment [6].
How Does Ransomware Work?
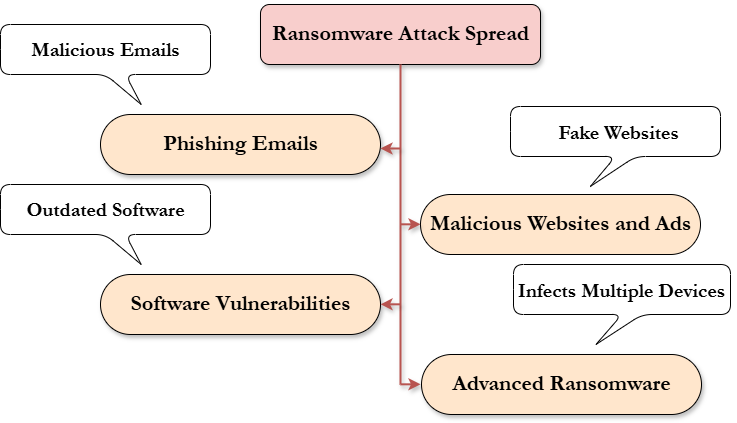
Ransomware attack doesn’t just like hit you without being a target first, common ransomware attack can spread through the following:
Phishing Emails: In phishing emails attack, cybercriminals will be sending a malicious email which have the characteristics of impersonating as a legit one, in this attack the message will contain a malicious link or maybe an attachment. When the victim is not well educated enough and will unknowingly or accidentally clicked don the link, the ransomware can then install itself on the device and encrypt the important files resulting to the ransomware attack [7].
Malicious Websites and Ads: Another method can also be used by the attackers, the utilization of fake websites or advertisement that is infected commonly known as the malvertising can also be done by them to trick users into downloading the ransomware, in this attack the users can usually see ad and when he/she clicks it, it will then download the ransomware [8].
Software Vulnerabilities: Some of the most common way to spread the attack of ransomware is the software vulnerabilities. In this attack, cybercriminals will exploit the flaws identified in the security system usually achieved with the utilization of outdated software, when the attackers are able to exploit this, they can then have access to the system and will be able to perform the ransomware attack [9].
Once the ransomware is installed in the device, the attacker can then directly commence their attack mechanism, which is to scan the system for important files, encrypt the important files, and display a ransom note which was already explained earlier. Additionally, there are some advance ransomware attacks which has the ability to spread across the networks and can infect one or more device at once, showcasing its sophistication [10].
Should You Pay the Ransom?
In the case of ransomware attack, the ransom is always a factor, however once being hit and see the terrifying message, you can then ask yourself about “should I pay for the ransom?” Well, cybersecurity experts have suggested about it, they strongly advise that you should not for the following reasons:
File recovery is not Guaranteed: In a ransomware attack, if there is a chance that you are going to pay for the ransom there are still going to be a huge chance that you can’t recover your file [11]. Most of the victims pay for the ransomware amount but end up gaining nothing in return.
Encourage More Attacks: Once you are going to pay for the ransom on the attackers, they will gain the idea of making it as a living, as it will be going to be an easy money for them. This will then drive them to commence a lot more attack and gain a lot more money with doing it [12].
Possible Legal Issues: Paying attackers some ransom even though you are just doing it to recover your files can also regulate some legal issues. Some governments have classified ransom payments as a method of supporting attackers, making you the victim classified as a criminal also [13].
These reasons are a strong statement that you need to consider. Alternatively, to effectively deal with this attack, the thing you can do is to focus more on implementing preventive measures and strategies for data recovery.
How to Protect Yourself from a Ransomware Attack
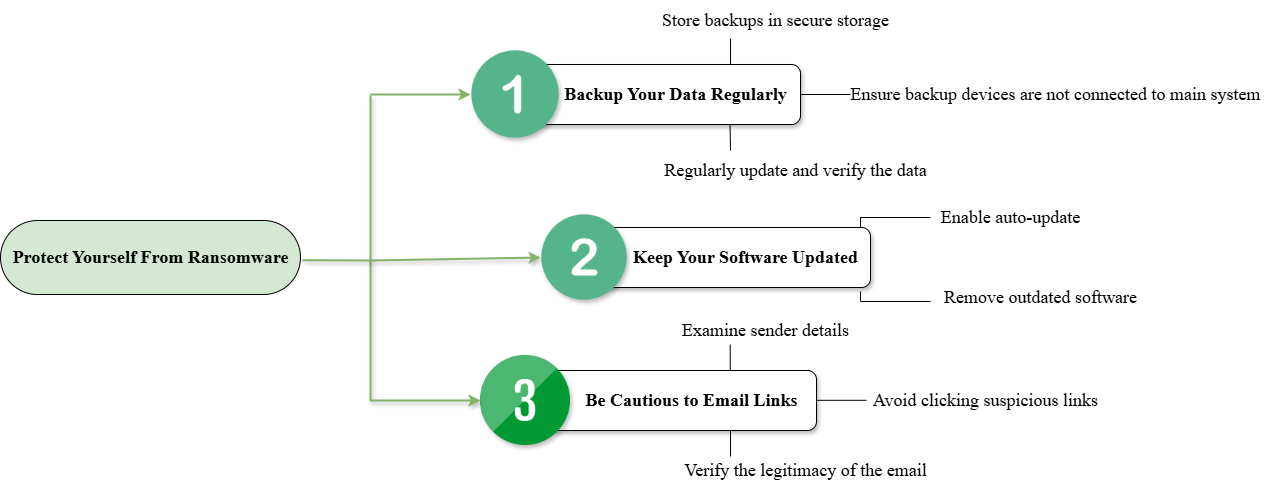
Even with the terrifying threat ransomware can provide, strategies that will keep you avoid being hit by this type of attack are still attainable, these practices will significantly lower the risk that you will have and is few of the best practices you can implement.
Backup Your Data Regularly: One of the best ways to prevent being tempted to pay for the ransom is to back up your data, this technique can be done in a common way of storing a backup of your important files or even all the files in cloud services or external drives which are not connected in the main system you are using. Additionally, you should ensure that the backup device or system that you are storing is frequently updated so that when you are being attacked by a ransomware, you can easily store the data even If the attacker have encrypted it in your main system [14].
Keep Your Software Updated: One of the common method attackers often used is the exploitation of the outdated software as security defense mechanism are not too sophisticated in this scenario. By effectively updating your system time to time or even enabling the auto update features that most of the operating system has, it can drastically lower the chance of you being attacked by ransomware attackers [15].
Be cautious with Email and Links: If you receive a malicious message with an embedded links or URLs through emails, you need to be cautious. As this is the most common way of conducting cyber-attack, being not too carefree and analyze carefully the situation whether you will click the link or not is a good way to prevent being attacked. You can easily do this by verifying the details of the sender, before fully opening the email as most of the time this type emails have contents that will urge you to open and will make you not focus on the sender details [16].
Conclusion
The growing threat of ransomware have a huge potential to affect individuals, businesses, and even governments and attackers usually did this by locking the users out to their devices, files, or systems and will request a payment for them to decrypt it. However, as what cybersecurity experts advise, paying the ransomware stated by the attacker is not going to be a good idea, as it will encourage them to conduct more attacks and will have no full possibility of a guaranteed file recovery. The best and easiest way to avoid being attack by this is prevention, with regularly backup, timely software update, and being cautious, the chance of being attacked is lower. With the method of cybercriminals in conducting their attack is more evolving, we need to stay one step ahead to them. Because in the current state of cybersecurity, prevention is better than cure.
Reference
- McIntosh, T., Kayes, A. S. M., Chen, Y. P. P., Ng, A., & Watters, P. (2021). Ransomware mitigation in the modern era: A comprehensive review, research challenges, and future directions. ACM Computing Surveys (CSUR), 54(9), 1-36.
- Lang, M., Connolly, L., Taylor, P., & Corner, P. J. (2023). The evolving menace of ransomware: A comparative analysis of pre-pandemic and mid-pandemic attacks. Digital Threats: Research and Practice, 4(4), 1-22.
- Lubin, A. (2022). The law and politics of ransomware. Vand. J. Transnat’l L., 55, 1177.
- Sharma, N., & Shanker, R. (2022, March). Analysis of ransomware attack and their countermeasures: A review. In 2022 International Conference on Electronics and Renewable Systems (ICEARS) (pp. 1877-1883). IEEE.
- Alqahtani, A., & Sheldon, F. T. (2022). A survey of crypto ransomware attack detection methodologies: an evolving outlook. Sensors, 22(5), 1837.
- What was the WannaCry ransomware attack? (n.d.). Cloudflare. Retrieved February 8, 2025, from https://www.cloudflare.com/learning/security/ransomware/wannacry-ransomware/
- Kovács, A. (2022). Ransomware: a comprehensive study of the exponentially increasing cybersecurity threat. Insights into Regional Development, 4(2), 96-104.
- Nowroozi, E., Mohammadi, M., & Conti, M. (2022). An adversarial attack analysis on malicious advertisement URL detection framework. IEEE Transactions on Network and Service Management, 20(2), 1332-1344.
- Reshmi, T. R. (2021). Information security breaches due to ransomware attacks-a systematic literature review. International Journal of Information Management Data Insights, 1(2), 100013
- Akibis, M., Pereira, J., Clark, D., Mitchell, V., & Alvarez, H. (2024). Measuring ransomware propagation patterns via network traffic analysis: An automated approach.
- Yin, T., Sarabi, A., & Liu, M. (2021, June). Deterrence, backup, or insurance: A game-theoretic analysis of ransomware. In The Annual Workshop on the Economics of Information Security (WEIS).
- Connolly, A. Y., & Borrion, H. (2022). Reducing ransomware crime: analysis of victims’ payment decisions. Computers & Security, 119, 102760.
- Logue, K. D., & Shniderman, A. B. (2021). The case for banning (and mandating) ransomware insurance. Conn. Ins. LJ, 28, 247.
- Patel, S., Bhadouria, A., Dodiya, K. R., & Khunt, A. Evaluating Modern Ransomware and Effective Data Backup and Recovery Solutions.
- Hrıstev, R., Veselınova, M., & Kolev, K. (2022). Ransomware Target: Linux. Recover Linux Data Arrays after Ransomware Attack. The Eurasia Proceedings of Science Technology Engineering and Mathematics, 19, 78-86.
- Humayun, M., Jhanjhi, N. Z., Alsayat, A., & Ponnusamy, V. (2021). Internet of things and ransomware: Evolution, mitigation and prevention. Egyptian Informatics Journal, 22(1), 105-117.
- Vajrobol, V., Saxena, G. J., Pundir, A., Singh, S., B. Gupta, B., Gaurav, A., & Rahaman, M. (2024). Identify spoofing attacks in Internet of Things (IoT) environments using machine learning algorithms. Journal of High Speed Networks, 09266801241295886.
- Rahaman, M., Pappachan, P., Orozco, S. M., Bansal, S., & Arya, V. (2024). AI Safety and Security. In Challenges in Large Language Model Development and AI Ethics (pp. 354-383). IGI Global.
- Shaik D. A. (2024) AI-Driven Solutions for Ransomware Protection, Insights2Techinfo, pp.1
Cite As
Cajes N. (2025) Ransomware in the Digital Age: How to Stay Safe from Cyber Extortion Insights2Techinfo, pp.1