By: Himanshu Tiwari, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, nomails1337@gmail.com
The rise of spam emails threatens email communication efficiency and security. This study examines spam emails’ complex effects on individuals and organizations. It examines spam evolution, spammer methods, and anti-spam measures. The study attempts to shed light on spam and recommend ways to fight it.
1. Introduction:
Email is essential for personal and professional communication in the digital age. The many spam emails ruin this convenience. Spam, unsolicited and often malicious emails, clog inboxes and pose phishing, malware, and identity theft dangers. This essay delves into spam’s history and emphasizes the need for comprehensive anti-spam solutions[1][2].
2. Historical Background:
Spam originated as unsolicited messages in the early days of the internet. Spam has become into a sophisticated and pervasive danger as technology has advanced. Understanding this history is essential for creating successful anti-spam solutions that battle modern spamming.
3. Spammer Methods:

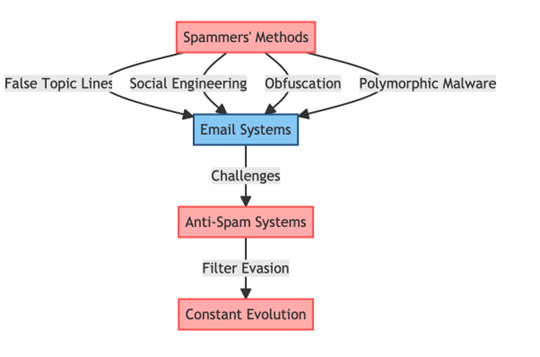
Spammers use many methods to hack email systems and transmit their spam. From false topic lines and social engineering to obfuscation and polymorphic malware, spammers constantly improve their strategies to escape filters. Spammers’ arsenal and standard anti-spam systems’ problems are examined in this section[3].
4. Current Spam Prevention:
To combat the growing issue of spam, many anti-spam solutions have been created. From heuristic filtering and blacklisting to machine learning methods, this section covers existing tools and technologies. These techniques have enhanced security, but their limitations and vulnerabilities require ongoing anti-spam strategy evaluation and improvement[4].
5. Current Anti-Spam Measure Flaws:

Despite advances in anti-spam technologies, spammers use weaknesses to avoid detection. Still, false positives—legitimate emails being classified as spam—are a problem. Spammers also use image-based spam and compromised real accounts, making it hard for typical filters to distinguish malicious from innocuous content. This section critiques current anti-spam measures and calls for a more sophisticated approach[5].
6. Spam Trends:
As technology advances, spammers adapt their approaches. This section discusses spam developments including mobile-based spam, voice message spam, and spammers using AI to produce more convincing phishing efforts. Staying ahead of these trends and updating anti-spam techniques to new threats requires understanding them[5].
7. Innovative Anti-Spam Defense Strategies:
This section addresses present weaknesses and evolving spamming techniques to offer more strong defenses. The research proposes a dynamic and adaptive spam response using advanced machine learning techniques, behavioral analysis, and collaborative threat intelligence[6].
8. User Education and Awareness:
Technological solutions are crucial for combatting spam, but user education and awareness are also crucial. This section emphasizes the need of spam education, phishing detection, and email hygiene. Cybersecurity awareness can make people the first line of spam defense[6].
9. Conclusion:
Fighting spam requires a diverse approach combining technology and user education. As spam evolves, so must our countermeasures. We can strengthen our defenses and create a more secure and efficient email communication ecosystem by addressing anti-spam flaws, following trends, and adopting new technology.
10. Future Directions:
To combat spam, research may explore blockchain technology for secure email communication, improved email service provider collaboration, and standardized protocols to prevent spam at its source. To create a spam-free digital world, this section examines research and development opportunities.
This study piece attempts to improve our understanding of spam and lay the groundwork for better anti-spam methods.
References
- Mohammed MA, Mostafa SA, Obaid OI, Zeebaree SR, Abd Ghani MK, Mustapha A, Fudzee MF, Jubair MA, Hassan MH, Ismail A, Ibrahim DA. An anti-spam detection model for emails of multi-natural language. Journal of Southwest Jiaotong University. 2019;54(3).
- Carreras X, Marquez L. Boosting trees for anti-spam email filtering. arXiv preprint cs/0109015. 2001 Sep 13.
- Wu CT, Cheng KT, Zhu Q, Wu YL. Using visual features for anti-spam filtering. InIEEE International conference on image processing 2005 2005 Sep 14 (Vol. 3, pp. III-509). IEEE.
- Boykin PO, Roychowdhury V. Personal email networks: An effective anti-spam tool. arXiv preprint cond-mat/0402143. 2004 Feb 4.
- Mohammed MA, Gunasekaran SS, Mostafa SA, Mustafa A, Abd Ghani MK. Implementing an agent-based multi-natural language anti-spam model. In2018 International symposium on agent, multi-agent systems and robotics (ISAMSR) 2018 Aug 27 (pp. 1-5). IEEE.
- Pampapathi R, Mirkin B, Levene M. A suffix tree approach to anti-spam email filtering. Machine Learning. 2006 Oct;65:309-38.
- Sharma, A., Singh, S. K., Badwal, E., Kumar, S., Gupta, B. B., Arya, V., … & Santaniello, D. (2023, January). Fuzzy Based Clustering of Consumers’ Big Data in Industrial Applications. In 2023 IEEE International Conference on Consumer Electronics (ICCE) (pp. 01-03). IEEE.
- Chui, K. T., Kochhar, T. S., Chhabra, A., Singh, S. K., Singh, D., Peraković, D., … & Arya, V. (2022). Traffic accident prevention in low visibility conditions using vanets cloud environment. International Journal of Cloud Applications and Computing (IJCAC), 12(1), 1-21.
- Gupta, P., Yadav, K., Gupta, B. B., Alazab, M., & Gadekallu, T. R. (2023). A Novel Data Poisoning Attack in Federated Learning based on Inverted Loss Function. Computers & Security, 130, 103270.
- Jain, A. K., Gupta, B. B., Kaur, K., Bhutani, P., Alhalabi, W., & Almomani, A. (2022). A content and URL analysis‐based efficient approach to detect smishing SMS in intelligent systems. International Journal of Intelligent Systems, 37(12), 11117-11141.
Cite As
Tiwari H. (2023) Tackling the Menace: A Comprehensive Analysis of Anti-Spam Measures in Email Communication, Insights2Techinfo, pp.1