By: Ritika Bansal, Insights2Techinfo, India Email: ritika@insights2techinfo.com
The current state of web security is a critical concern in the digital age, as the internet has become an integral part of our daily lives. With the rapid growth of web services and internet applications, ensuring the security of these platforms has become increasingly challenging. Web service security encompasses various aspects such as message level security, application security, and the quality and security of web services. It is essential to guarantee the confidentiality, authentication, integrity, authorization, and non-repudiation of machine-to-machine interactions [1]. The security of web services is crucial for businesses to adopt web services technology as a means of running their information systems [2].
The increasing demand for web services has brought about new security challenges due to the open and scattered nature of the internet [3]. As a result, there is a growing emphasis on the quality and security of web services, with researchers and developers focusing on addressing vulnerabilities and improving the robustness of web services [4][5]. However, it is important to note that there is no way to completely alleviate all web vulnerabilities, and further study is desirable in the field of web information security [6].
Web application security assessment tools have become indispensable due to the increasing complexity of web systems, making security testing a critical activity in the web application development life cycle [7][8]. Additionally, the security of web services is closely linked to the trustworthiness of web applications, as the role of web services in secure web application development is contingent on their trustworthiness [9].
The evolution of the Internet, including the Internet of Things (IoT) and the Internet of People (IoP), has further emphasized the importance of secure web services. The impact of security on the development of IoT is becoming increasingly important, and secure wearable wireless sensor networks are gaining more significance with the growth and usage of IoT [10][11]. Furthermore, the Long Term Evolution (LTE) technology and its evolutions are expected to play a major role in ensuring secure communication infrastructure for machine-to-machine (M2M) devices and smart objects [12].
Understanding XSS Attacks
XSS (Cross-Site Scripting) attacks are a prevalent form of security threat that targets web applications. These attacks occur when malicious scripts are injected into web pages viewed by other users. The injected scripts can be written in various languages such as JavaScript, and they execute within the context of a user’s browser. This allows attackers to steal sensitive information, such as login credentials, session tokens, or personal data, from unsuspecting users. XSS attacks exploit the trust a user has for a particular site, as the scripts appear to be originating from the trusted site. There are different types of XSS attacks, including reflected XSS, stored XSS, and DOM-based XSS, each with its own specific characteristics and methods of exploitation [13][14][15].
The impact of XSS attacks can be severe, leading to unauthorized access to sensitive data, defacement of websites, and the spread of malware. As a result, there is a growing emphasis on the development of defense mechanisms and detection techniques to mitigate the risks associated with XSS attacks. Various approaches have been proposed to prevent XSS attacks, including the use of machine learning classifiers, semantic parsing, and randomization techniques. Additionally, researchers have explored the application of structural learning and attack vector analysis to generate mutated XSS attacks for testing and defense purposes [13][16][17].
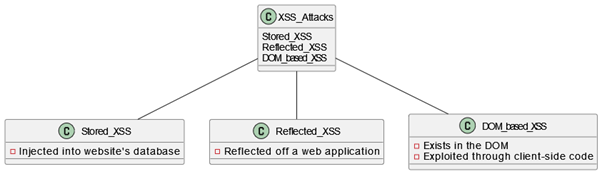
Furthermore, the significance of addressing XSS vulnerabilities has been underscored by the increasing interconnectedness of devices and the widespread use of web applications. The potential impact of XSS attacks on various platforms, including mobile devices and cloud computing environments, has prompted the development of specialized detection and prevention tools. Additionally, the severity of XSS vulnerabilities has been highlighted by notable incidents affecting major websites and online platforms, further emphasizing the need for robust security measures [18][19].
The Shortcomings of Traditional XSS Prevention Methods
Overview of Conventional XSS Defense Mechanisms
Traditional methods for preventing Cross-Site Scripting (XSS) attacks primarily focus on two strategies: input validation and output encoding.
- Input Validation: This involves scrutinizing user inputs to ensure they do not contain malicious scripts. By using allowlists (formerly known as whitelists) and blocklists (formerly known as blacklists), web applications attempt to filter out potentially harmful content. Allowlists permit only a predefined set of safe inputs, whereas blocklists deny known dangerous inputs.
- Output Encoding: This strategy is about escaping special characters in user inputs before they are rendered in the browser. By converting characters like <, >, and & into their HTML entity equivalents (e.g., <, >, &), the application prevents the browser from executing potentially malicious scripts.
- Content Security Policy (CSP): CSP is a browser-side mechanism that allows webmasters to declare approved sources of content that browsers should load on their websites. It’s designed to prevent a wide range of attacks, including XSS.
Limitations in Dealing with Advanced and Evolving XSS Threats
Despite their effectiveness against basic attacks, these traditional methods have several limitations:
- Inability to Adapt to Sophisticated Attacks: Attackers continuously devise new methods to bypass static defense mechanisms. For instance, obfuscation techniques can disguise malicious scripts, making them undetectable by simple pattern-matching methods used in input validation.
- High False Positive and False Negative Rates: Rigid rules in input validation can lead to a high number of false positives, where benign inputs are mistakenly flagged as malicious. Conversely, they can also result in false negatives, where actual malicious inputs go undetected.
- Dependence on Manual Configuration and Updates: Traditional methods often rely on security professionals to manually configure and update defense mechanisms. This approach is not scalable and fails to keep pace with the rapidly evolving landscape of XSS attacks.
- Limited Effectiveness Against Zero-Day Vulnerabilities: Traditional defenses are largely ineffective against zero-day attacks, where the vulnerability is unknown and unaddressed until it is exploited.
- Complexity in Handling Dynamic Web Content: Modern web applications often include dynamic content and complex user interactions, which can be challenging to secure using static validation and encoding rules.
- Reliance on Browser Compliance with CSP: CSP’s effectiveness is contingent on browser enforcement. Inconsistent implementation across different browsers can lead to gaps in security.
Machine Learning in XSS Detection
We couldn’t properly fact-check and verify our response. Below is the raw draft before our verification step, so it might have issues. Please use it at your own risk. Machine learning has emerged as a powerful tool in the detection of XSS (Cross-Site Scripting) attacks, offering the potential to enhance the security of web applications. Researchers have proposed various methods and algorithms that leverage machine learning to detect and prevent XSS attacks, thereby mitigating the risks associated with these security threats.
One approach involves the use of machine learning algorithms to extract features from URLs and JavaScript code, enabling the detection of XSS attacks. For instance, a study by Fang et al. proposed a method for detecting XSS attacks using machine learning algorithms, such as naive Bayes, SVM, and J48 decision trees, to analyze the characteristics of URLs and JavaScript code Fang et al. [20]. Similarly, Buz et al. introduced a hybrid machine-learning model specifically designed to detect vulnerabilities related to reflected XSS attacks for a given website URL [21]. These studies demonstrate the potential of machine learning in identifying XSS attack patterns and enhancing the security of web applications.
Furthermore, researchers have explored the application of ensemble learning methods, such as ADTree and AdaBoost, to detect XSS attacks. Mokbal et al. utilized ensemble learning to effectively identify XSS attacks, highlighting the potential of combining multiple learning algorithms for improved detection accuracy [22]. Additionally, the use of genetic algorithms and reinforcement learning has been proposed to enhance the detection of XSS attacks. For example, Gupta et al. applied a genetic algorithm along with reinforcement learning to detect XSS attacks, showcasing the versatility of machine learning techniques in addressing web security challenges [23].
Table 1: Machine Learning and XSS Attack
| Machine Learning Algorithm | Description | Application in XSS Detection |
| Neural Networks | A set of algorithms modeled loosely after the human brain, designed to recognize patterns. | Can analyze web traffic and detect anomalies indicating XSS attacks. |
| Decision Trees | A tree-like model of decisions, where each branch represents a possible decision, event, or reaction. | Useful for classifying types of scripts and identifying potentially malicious ones. |
| Support Vector Machines (SVM) | Supervised learning models that analyze data for classification and regression analysis. | Efficient in classifying and segregating safe content from malicious XSS scripts. |
| Random Forests | An ensemble learning method that operates by constructing multiple decision trees. | Provides high accuracy in detecting complex XSS attack patterns by considering various factors. |
| Naive Bayes Classifier | A simple probabilistic classifier based on applying Bayes’ theorem. | Effective for web content filtering, identifying typical XSS attack signatures. |
| K-Nearest Neighbors (KNN) | A non-parametric method used for classification and regression. | Useful in detecting XSS attacks by analyzing similarities between known attacks and current data. |
| Logistic Regression | A statistical model that uses a logistic function to model a binary dependent variable. | Can help in predicting the probability of a web input being an XSS attack. |
Moreover, the integration of machine learning with other technologies, such as Bayesian networks and convolutional neural networks, has shown promise in the detection of XSS attacks. Sun and Zhou demonstrated the effectiveness of Bayesian network structure learning in achieving a high accuracy of 99.48% in detecting XSS attacks, highlighting the potential of probabilistic graphical models in web security [24]. Similarly, Yan et al. proposed a modified convolutional neural network for XSS attack detection, showcasing the application of deep learning techniques in addressing web security threats [25].
In addition to specific algorithmic approaches, the use of machine learning for cybersecurity has been emphasized in the context of intrusion detection systems. Machine learning-based intrusion detection systems have been recognized as an effective strategy for addressing cybersecurity challenges, leveraging the capabilities of machine learning to analyze risks and respond to security incidents [26]. Furthermore, the proactive nature of machine learning techniques has been highlighted, offering the potential to enhance cybersecurity by providing real-time threat prediction and response capabilities [27][28].
Future Trends and Developments
Emerging Trends in ML and Web Security
The landscape of Machine Learning (ML) in web security is rapidly evolving. One of the most significant trends is the integration of Artificial Intelligence (AI) with ML for more dynamic and responsive security systems. AI algorithms are being developed to not only detect but also predict potential XSS vulnerabilities by analyzing patterns in large datasets. Another emerging trend is the use of federated learning, where ML models are trained across multiple decentralized devices or servers. This approach enhances privacy and security by allowing model training on a large scale without the need to share sensitive data.
Potential for AI and ML in Proactive Web Defense Strategies
AI and ML are shifting the paradigm from reactive to proactive web defense strategies. By leveraging predictive analytics, these technologies can forecast potential attack vectors and identify vulnerabilities before they are exploited. This proactive stance is particularly effective in defending against zero-day XSS attacks, where vulnerabilities are unknown until exploited. Additionally, the use of AI-driven automation in security protocols can significantly reduce the time and resources needed to respond to threats, enabling more efficient and effective security management.
Predictions for the Future of XSS Detection Technologies
Looking forward, the role of AI and ML in XSS detection is set to become more sophisticated and integrated. We can expect to see:
- Self-Learning Security Systems: Advanced ML models will continuously learn and adapt to new threats, reducing the need for manual updates and intervention.
- Enhanced Natural Language Processing (NLP): NLP techniques will improve the ability of security systems to understand and interpret human language within code, enhancing the detection of sophisticated XSS attacks embedded in texts.
- Integration with Internet of Things (IoT): As IoT devices become more prevalent, ML models will be increasingly deployed to secure these devices from XSS and other web-based attacks.
- Blockchain for Security: Blockchain technology, combined with ML, could offer a new layer of security by providing decentralized and tamper-proof data management, making XSS attack detection more reliable and transparent.
- Quantum Computing: The advent of quantum computing could revolutionize ML capabilities in XSS detection by processing vast amounts of data at unprecedented speeds, making real-time detection and response a reality.
Conclusion
In conclusion, the current state of web security is characterized by a growing emphasis on addressing vulnerabilities, improving the robustness of web services, and ensuring the trustworthiness of web applications. The increasing complexity of web systems and the evolution of the Internet, including IoT and wearable wireless sensor networks, have further underscored the importance of web service security in the digital landscape. XSS attacks pose a significant threat to web application security, and their potential impact on user privacy and data integrity cannot be understated. The development of effective defense mechanisms and detection techniques is crucial in mitigating the risks associated with XSS attacks and ensuring the overall security of web applications. Overall, the application of machine learning in the detection of XSS attacks holds significant promise for improving the security of web applications. By leveraging machine learning algorithms, feature extraction, ensemble learning, and integration with other technologies, researchers have made strides in developing effective detection mechanisms for XSS attacks, contributing to the ongoing efforts to enhance web security.
References
- M. Basha, “Service level security using expected clandestine figure for corroboration of web service consumer“, International Journal of Advancements in Computing Technology, vol. 2, no. 3, p. 139-154, 2010.
- R. Boncella, “Web and web security“, Communications of the Association for Information Systems, vol. 14, 2004.
- M. Noman, M. Iqbal, & A. Manzoor, “A survey on detection and prevention of web vulnerabilities“, International Journal of Advanced Computer Science and Applications, vol. 11, no. 6, 2020.
- S. Lee, “A study on web service analysis and bio-information based web service security mechanism“, International Journal of Security and Its Applications, vol. 8, no. 2, p. 77-86, 2014.
- “Survey on a novel approach for web service – security testing to improve web service robustness“, International Journal of Science and Research (Ijsr), vol. 5, no. 1, p. 325-329, 2016.
- J. Shahid, M. Hameed, I. Javed, K. Qureshi, M. Ali, & N. Crespi, “A comparative study of web application security parameters: current trends and future directions“, Applied Sciences, vol. 12, no. 8, p. 4077, 2022.
- A. Jaiswal, G. Raj, & D. Singh, “Security testing of web applications: issues and challenges“, International Journal of Computer Applications, vol. 88, no. 3, p. 26-32, 2014.
- M. Curphey and R. Arawo, “Web application security assessment tools“, Ieee Security & Privacy, vol. 4, no. 4, p. 32-41, 2006.
- G. Raj, M. Mahajan, & D. Singh, “Trust decision model and trust evaluation model for quality web service identification in web service lifecycle using qsw data analysis“, International Journal of Web-Based Learning and Teaching Technologies, vol. 15, no. 1, p. 53-72, 2020.
- Q. Liu, X. Zhang, Q. Hua, Z. Wen, & H. Li, “Adaptive differential evolution algorithm with simulated annealing for security of iot ecosystems“, Wireless Communications and Mobile Computing, vol. 2022, p. 1-13, 2022.
- M. Savitha*, “Applications, attacks and authentication schemes for future iot“, International Journal of Innovative Technology and Exploring Engineering, vol. 9, no. 4, p. 2841-2848, 2020.
- M. Ouaissa and A. Rhattoy, “A secure model for machine to machine device domain based group in a smart city architecture“, International Journal of Intelligent Engineering and Systems, vol. 12, no. 1, p. 151-164, 2019.
- Ahvanooey, M. T., Zhu, M. X., Li, Q., Mazurczyk, W., Choo, K. K. R., Gupta, B. B., & Conti, M. (2021). Modern authentication schemes in smartphones and IoT devices: An empirical survey. IEEE Internet of Things Journal, 9(10), 7639-7663.
- B. Buz, B. Gülçiçek, & Ş. Bahtiyar, “A hybrid machine learning model to detect reflected xss attack“, Balkan Journal of Electrical and Computer Engineering, vol. 9, no. 3, p. 235-241, 2021.
- Gupta, S., & Gupta, B. B. (2016). XSS-SAFE: a server-side approach to detect and mitigate cross-site scripting (XSS) attacks in JavaScript code. Arabian Journal for Science and Engineering, 41, 897-920.
- Y. Wang, C. Mao, & H. Lee, “Structural learning of attack vectors for generating mutated xss attacks“, Electronic Proceedings in Theoretical Computer Science, vol. 35, p. 15-26, 2010.
- C. Pardomuan, A. Kurniawan, M. Darus, M. Ariffin, & Y. Muliono, “Server-side cross-site scripting detection powered by html semantic parsing inspired by xss auditor“, Pertanika Journal of Science and Technology, vol. 31, no. 3, p. 1353-1377, 2023.
- Poonia, V., Goyal, M. K., Gupta, B. B., Gupta, A. K., Jha, S., & Das, J. (2021). Drought occurrence in different river basins of India and blockchain technology based framework for disaster management. Journal of Cleaner Production, 312, 127737.
- V. Nithya, S. Pandian, & C. Malarvizhi, “A survey on detection and prevention of cross-site scripting attack“, International Journal of Security and Its Applications, vol. 9, no. 3, p. 139-152, 2015.
- Gupta, B. B., Gupta, S., Gangwar, S., Kumar, M., & Meena, P. K. (2015). Cross-site scripting (XSS) abuse and defense: exploitation on several testing bed environments and its defense. Journal of Information Privacy and Security, 11(2), 118-136.
- B. Buz, B. Gülçiçek, & Ş. Bahtiyar, “A hybrid machine learning model to detect reflected xss attack“, Balkan Journal of Electrical and Computer Engineering, vol. 9, no. 3, p. 235-241, 2021.
- F. Mokbal, D. Wang, X. Wang, & L. Fu, “Data augmentation-based conditional wasserstein generative adversarial network-gradient penalty for xss attack detection system“, Peerj Computer Science, vol. 6, p. e328, 2020.
- C. Gupta, R. Singh, & A. Mohapatra, “Geneminer: a classification approach for detection of xss attacks on web services“, Computational Intelligence and Neuroscience, vol. 2022, p. 1-12, 2022.
- Gupta, S., & Gupta, B. B. (2018). XSS-secure as a service for the platforms of online social network-based multimedia web applications in cloud. Multimedia Tools and Applications, 77, 4829-4861.
- H. Yan, L. Feng, Y. You, W. Liao, F. Liu, J. Zhanget al., “Cross-site scripting attack detection based on a modified convolution neural network“, Frontiers in Computational Neuroscience, vol. 16, 2022.
- Gaurav, A., Gupta, B. B., & Panigrahi, P. K. (2023). A comprehensive survey on machine learning approaches for malware detection in IoT-based enterprise information system. Enterprise Information Systems, 17(3), 2023764.
- A. Alharbi, A. Seh, W. Alosaimi, H. Alyami, A. Agrawal, R. Kumaret al., “Analyzing the impact of cyber security related attributes for intrusion detection systems“, Sustainability, vol. 13, no. 22, p. 12337, 2021.
- M. Arshad and M. Hussain, “A real-time lan/wan and web attack prediction framework using hybrid machine learning model”, International Journal of Engineering & Technology, vol. 7, no. 3.12, p. 1128, 2018. https://doi.org/10.14419/ijet.v7i3.12.17774
Cite As:
Bansal R. (2023), The Future of Web Security: XSS Detection through Machine Learning, Insights2Techinfo, pp.1