By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Social engineering combined with phishing techniques poses an extreme danger to all members of society within today’s fast-moving cybersecurity domain. This paper studies the methods social engineers use to manipulate human psychology for phishing attacks while suggesting the need to comprehend psychological human behaviors in cybersecurity. The study of established cybercriminal approaches helps us create protective measures to improve computer security knowledge among users while enhancing their resistance against ongoing threats.
Introduction:
Cybersecurity requires understanding human behavior because people face this challenge even though most consider it an issue with technology. Modern sophisticated cyber threats have motivated organizations to shift their focus toward human factors as essential elements for cybersecurity protection[1]. The widespread phishing strategy used by digital attackers takes advantage of human behavior to prompt the disclosure of sensitive information thus creating major security problems for individuals and organizations. Attacks that make use of social engineering techniques critically facilitate overcoming technical protection mechanisms to get past defenses[2]. Organizations achieve better protection against such threats by understanding the connection that exists between phishing attacks and social engineering methods. The examination of cybercriminal methods through this study helps develop training strategies to empower people in detecting and reacting appropriately when they encounter phishing attempts.
Understanding Social Engineering:
Through psychological manipulation attackers coerce people into specific actions and disclose confidential information. Predatory cybercriminals exploit human feelings of worry and want as well as sense of emergency to manipulate innocent victims. Attackers employ three types of social engineering methods consisting of pretexting through deceptive scenarios and baiting by offering attractive tactics together with tailgating when unidentified individuals follow authorized personnel[3].
Flowchart: Understanding the Process of Phishing and Social Engineering
The following flowchart explains the connection between social engineering methods and phishing attacks by focusing on human involvement.
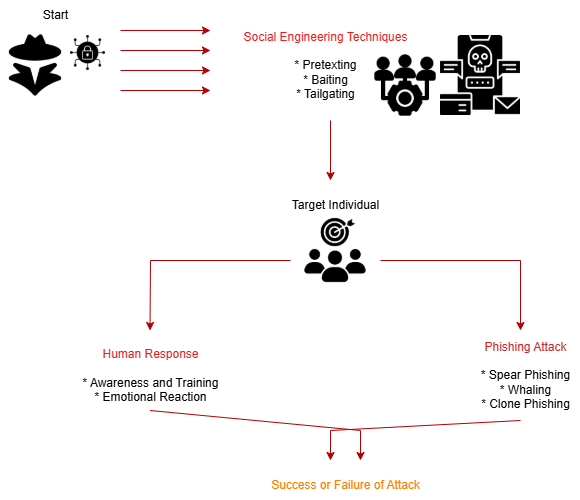
Phishing Techniques:
Social engineering primarily consists of phishing attacks through fraudulent communications that normally begin with emails. Phishing techniques encompass three main methods including spear phishing for specific targets and whaling attacks against executive-level persons and clone phishing that duplicates genuine messages containing harmful links[4].
The Human Factor:
Human behavior remains the primary factor behind successful phishing intrusion attempts. Cybercriminals target people through human psychological weaknesses since they know technology defenses are not foolproof[5]. Phishing signs often escape detection for people because they lack awareness and training and feel overconfident in their threat-detecting abilities while experiencing panic-like responses after receiving alarming messages. The extensive human exposure to phishing attacks shows a pressing requirement for permanent cybersecurity education besides organized security protocols[6].
Countermeasures and Best Practices:
An effective approach for fighting social engineering attacks in combination with phishing requires organizations to develop detailed training that teaches employees proper cybersecurity practices. Companies should train employees repeatedly about phishing detection and social engineering methods while conducting faux phishing tests to verify employee behavior and promoting a secure environment through employee-based reporting procedures. These security measures help both individual resilience and organizational security posture become stronger[7].
Conclusion:
The combination between social engineering and phishing proves how crucial it is for security measures to account for human behavior in protecting systems. Worldwide threats in the cyber realm require people and organizations to master the mental methods cyber criminals use to exploit their victims. Organizations that provide continuous education alongside awareness culture development will equip their staff members for combating phishing attacks along with social engineering attempts. A devoted security strategy protects both individual and organizational security while creating robust cybersecurity defenses that decrease human-based misstep threats. Protecting against cyber threats depends heavily on employees who remain alert because their awareness makes the human factor both strong and secure in cybercrime defense.
References:
- A. Lokare, S. Bankar, and P. Mhaske, “Integrating Cybersecurity Frameworks into IT Security: A Comprehensive Analysis of Threat Mitigation Strategies and Adaptive Technologies,” Feb. 02, 2025, arXiv: arXiv:2502.00651. doi: 10.48550/arXiv.2502.00651.
- S. Gupta, A. Singhal, and A. Kapoor, “A literature survey on social engineering attacks: Phishing attack,” in 2016 International Conference on Computing, Communication and Automation (ICCCA), Apr. 2016, pp. 537–540. doi: 10.1109/CCAA.2016.7813778.
- “Understanding and deciphering of social engineering attack scenarios – Yasin – 2021 – SECURITY AND PRIVACY – Wiley Online Library.” Accessed: Feb. 27, 2025. [Online]. Available: https://onlinelibrary.wiley.com/doi/abs/10.1002/spy2.161
- A. Arshad, A. U. Rehman, S. Javaid, T. M. Ali, J. A. Sheikh, and M. Azeem, “A Systematic Literature Review on Phishing and Anti-Phishing Techniques,” Apr. 02, 2021, arXiv: arXiv:2104.01255. doi: 10.48550/arXiv.2104.01255. [5] A. I. Mallick and R. Nath, “Navigating the Cyber security Landscape: A Comprehensive Review of Cyber-Attacks, Emerging Trends, and Recent Developments,” 2024.
- “Cybersecurity And Its Global Applicability to Decision Making: A Comprehensive Approach in The University System by Adebola Folorunso :: SSRN.” Accessed: Feb. 27, 2025. [Online]. Available: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4955601
- A. Sadiq et al., “A review of phishing attacks and countermeasures for internet of things-based smart business applications in industry 4.0,” Hum. Behav. Emerg. Technol., vol. 3, no. 5, pp. 854–864, 2021, doi: 10.1002/hbe2.301.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- Lv, L., Wu, Z., Zhang, L., Gupta, B. B., & Tian, Z. (2022). An edge-AI based forecasting approach for improving smart microgrid efficiency. IEEE Transactions on Industrial Informatics, 18(11), 7946-7954.
- Cajes N. (2025) The Hidden Threat: Understanding and Preventing Spear Phishing Attacks, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) The Intersection of Social Engineering and Phishing: Analyzing the Human Factor in Cybersecurity, Insights2Techinfo, pp.1