By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Within the digital world, cybersecurity threats have become more sophisticated, and among these, one of the most persistent and damaging threats involves DDoS attacks. The majority of such DDoS attacks are carried out using botnets-a network of various compromised devices controlled by cybercriminals. This article presents the in-depth analytical overview of the functioning mechanisms behind botnets that drive DDoS-attacks, their very impact on businesses and internet infrastructures, and different mitigation mechanisms that could and should be drawn. Indeed, understanding how this type of threat works will aid organizations and people in making conscious decisions about setting up defense strategies against these specific cyber threats.
Introduction:
Today, in a globally interconnected modern world, all kinds of cybersecurity threats are going up at unending rates due to the large exposition of enterprise business, state and government records, and person-level information through connected devices on the internet, out of which the DDoS attack features at the center stage. By nature, any DDoS attack involves subjecting the targeted site with intensive traffic that a legitimate user finds difficult to assess. A botnet is the main enabler of DDoS attacks-a huge network of devices compromised by hackers who take control over the devices remotely. Such devices, often infected with malware, are used to take part in massive attacks-with the owners never knowing that it could be computers, IoT devices, and even smartphones; hence, highly scalable and hard to trace[[1]].
Botnets have made DDoS attacks more within the reach of cybercriminals, and the consequences of this have stretched across industries, from financial institutions to online gaming services. As such, research into the operations of botnets, how they perform DDoS attacks, and the security imperatives or countermeasures that could be pursued and imposed becomes highly relevant for economic and security reasons[[2]].
What is a botnet?
It is an ensemble of devices, including computers, routers, IoTs, and smartphones. They get infected with malware. These are the so-called “bots” or “zombies”-remote-controlled by some cybercriminal, often referred to as a botmaster. Among the ways botnets can be used, one of the most common is running DDoS attacks.
How Do Botnets Accomplish DDoS Attacks?
The major function of a botnet in the case of DDoS is to flood the target server, network, or website with high volumes of traffic, making services unavailable partly or completely. In starting the process, the cybercriminal infects several devices with malware through phishing emails, downloads, or via software vulnerabilities. These devices are thus turned into remotely controlled bots on a C&C server or distributed within a peer-to-peer decentralized network. An activated bot would, in a chain, activate others to participate in the processing of massive sets of requests, sending them, along with associated data packets toward the target’s system resources so that the inability to cope, leading to failure, becomes hopeless for legitimate use. The scale and complexity of botnet-driven DDoS attacks make them hard to mitigate, thus allowing cybercriminals to conduct large-scale disruptions with very little effort[[3]].
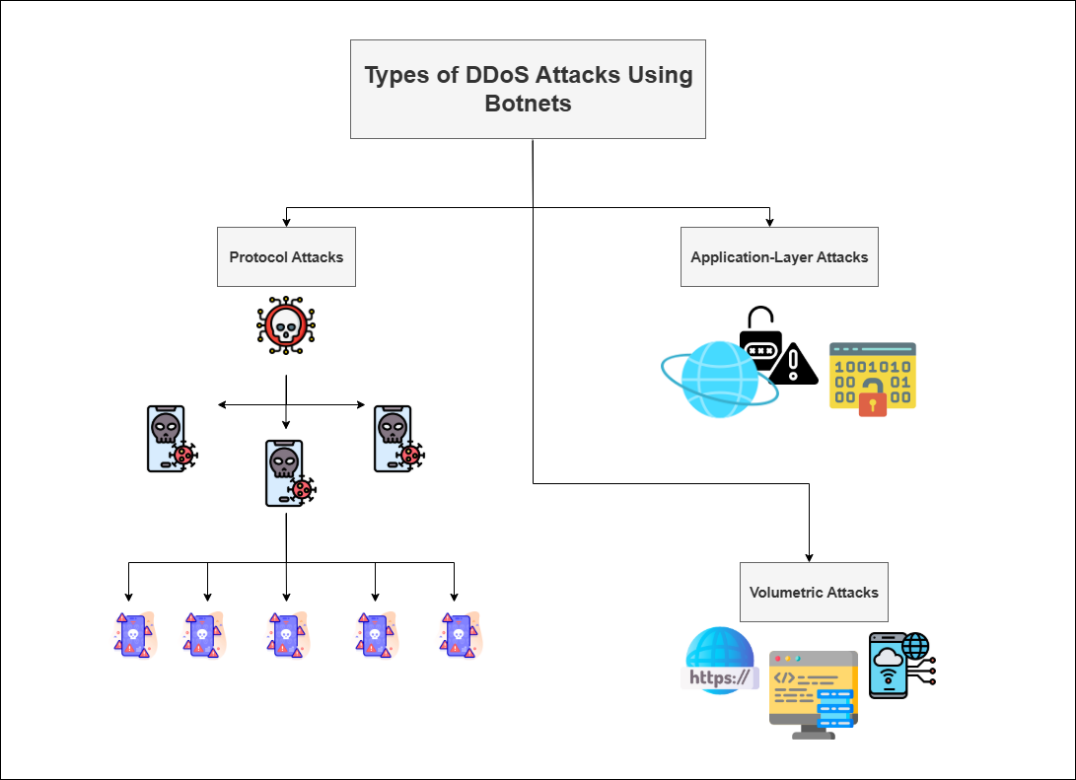
Fig(1)
Real-world examples of botnet DDoS attacks:
Mirai Botnet (2016): Mirai botnet hacked Internet of Things (IoT) devices and performed large DDoS assaults on popular services such as Twitter and Netflix[[4]].
Mēris Botnet (2021) :It targets economic and government organizations, with unprecedented attack volumes[[5]].
Reducing Botnet-Driven DDoS Assaults:
There are multiple strategies to lessen the botnet risk for companies and people in general:
- Network Security Solutions: Barriers, systems to detect intrusions, and DDoS mitigation services should be implemented.
- Keep Devices Updated: Software, firmware, and security fixes must be upgraded upon an ongoing schedule to prevent cyberattacks based on identified weaknesses.
- Strong Authentication: Multi-factor authentication protects access in the event of stolen credentials.
- Monitor Network Traffic: Monitoring irregular flow of traffic enables prompt identification of malware activity. And educate user awareness training reduces the risk of malware infection via phishing and fraudulent downloads.
Conclusion:
Botnets remain a potent force driving DDoS attacks, causing significant disruptions to businesses and internet services. Their role, methods of attack, and mitigation strategies must be understood to secure networks and online resources. By adopting proactive security strategies, organizations can mitigate the risk of botnet-driven DDoS attacks.
References:
- Borys, Adam, Abu Kamruzzaman, Hasnain Nizam Thakur, Joseph C. Brickley, Md L. Ali, and Kutub Thakur. “An Evaluation of IoT DDoS Cryptojacking Malware and Mirai Botnet.” In 2022 IEEE World AI IoT Congress (AIIoT), 725–29, 2022. https://doi.org/10.1109/AIIoT54504.2022.9817163.
- Haner, Justin K, and Robert K Knake. “Breaking Botnets: A Quantitative Analysis of Individual, Technical, Isolationist, and Multilateral Approaches to Cybersecurity.” Journal of Cybersecurity 7, no. 1 (February 16, 2021): tyab003. https://doi.org/10.1093/cybsec/tyab003.
- Owen, Harry, Javad Zarrin, and Shahrzad M. Pour. “A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention.” Journal of Cybersecurity and Privacy 2, no. 1 (March 2022): 74–88. https://doi.org/10.3390/jcp2010006.
- ———. “A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention.” Journal of Cybersecurity and Privacy 2, no. 1 (March 2022): 74–88. https://doi.org/10.3390/jcp2010006.
- Shao, Yu-An, and Chi-Shih Chao. “Real-Time Dynamic Configuration of Firewall Rules for High-Speed IoT Networks.” In 2022 IEEE 4th Eurasia Conference on IOT, Communication and Engineering (ECICE), 89–94, 2022. https://doi.org/10.1109/ECICE55674.2022.10042899.
- Gaurav, A., Gupta, B. B., & Panigrahi, P. K. (2023). A comprehensive survey on machine learning approaches for malware detection in IoT-based enterprise information system. Enterprise Information Systems, 17(3), 2023764.
- Lv, L., Wu, Z., Zhang, L., Gupta, B. B., & Tian, Z. (2022). An edge-AI based forecasting approach for improving smart microgrid efficiency. IEEE Transactions on Industrial Informatics, 18(11), 7946-7954.
- Cajes N. (2025) DDoS Explained: A Deep Dive into Cyber Disruptions, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) The Role of Botnets in DDoS Attacks: A Deep Dive, Insights2Techinfo, pp.1