By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Phishing is one of the most current and serious cyber threats that many individuals and organizations are facing today. In it, attackers leverage trusting users’ lack of awareness to make them reveal sensitive information, including passwords, credit card details, or personal identifiers. This article highlights phishing and some ways of its detection and prevention. In this perspective, through reviewing the available literature and proposing some methodology, we show how one may protect themselves against this dangerous kind of cyberattack.
Introduction:
Cyber phishing in recent years has turned out to be one of the most current and hazardous types of cyber threats in the modern, post-modern digital sphere. Generally, phishing is the criminal activity where by fraudsters try to dupe people into giving out important personal information such as passwords, credit card numbers, and personal identifications. They usually attack their victims with what looks like legitimate emails, messages, or even voice calls from an apparently trusted institution like a bank or government agency or service provider. The success of a phishing attack is essentially dependent on the manipulation of human feelings like urgency, fear, or curiosity. Attackers might also spoof a bank or online retailer and send the target an email, thereby requesting that he updates his account information urgently. This email contains a link that would lead the victim to a fake website that appears similar to any legitimate one [[1]]. Once the victim logs in with their information, the attackers then have unauthorized access to personal information that then can be used for identity theft or financial fraud. The increasing effectiveness of phishing schemes makes it more hazardous. Most of the phishing attempts nowadays are undifferentiable from real communications. The attackers now use advanced techniques, such as social engineering, which involves gathering information from public sources, like social media profiles, to craft messages. This has increased the legitimacy of phishing because it has become simple for an attacker to create customized messages that appeal to the target. The risks of phishing are not limited to individuals, but also to organizations. Employees could get tricked by phishing, resulting in the compromise of systems and breaches of data. The financial losses from phishing are in billions annually [[2]]. Besides this, reputational damage due to a successful phishing attack might take some time to restore. While there’s risk, phishing can be prevented. It can be significantly reduced by increasing user awareness and education, using technological measures such as multi-factor authentication and email filtering to reduce the likelihood of being victimized by phishing. Being aware and caution remain the best guard against this growing threat.
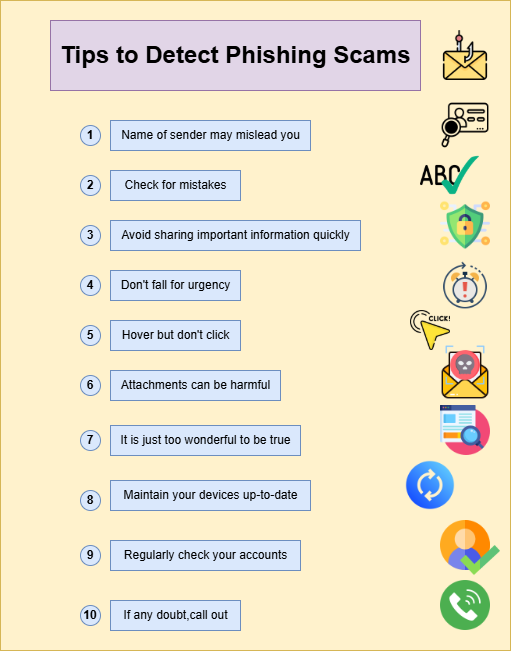
Figure(1)[[3]]
Literature Review:
While the threat keeps growing, research about phishing has increased exponentially in the past decade. Early works mostly focused on the psychological factor involved in phishing, how the attacker manipulates urgent emotions, curious feelings, or even fear, to get the sensitive information out from users. On other occasions, works later investigated technological methods of detection by machine learning algorithms analyzing patterns in headers and email contents for phishing detection[[4]].
Recent studies have also placed emphasis on the role of user awareness and training in preventing phishing, therefore suggesting education as one of the most effective strategies. A look at some techniques used for preventing phishing has demonstrated the general approaches such as MFA, e-mail filtering system, DNS Security [[5]]. Whereas those approaches seem somewhat effective, they too could not make users absolutely immune or fully un-targetable because more effective tricks develop along with developing mechanisms of protection against their realization.
Methodology:
The steps we propose against phishing are technologically and people-oriented. In short, the breakdown of the methodology will go this way:
- User awareness training:
Imparting regular training in terms of spotting attempts at phishing-by identifying suspicious ‘from’ e-mail addresses, suspicious attachments, unexpected language usage among others.
- Deployment of MFA:
Microsoft Multi-Factor Authentication
Enabling MFA across all accounts secures them much further, making such attacks even tougher for the perpetrators, who cannot successfully get hold of sensitive information easily.
- E-mail Filtering and Spam Detection:
Advanced spam filters can be utilized that may efficiently block suspicious emails, which could contain links or attachments to phishing sites.
- Regular Software Updates:
Keep the antivirus software updated, as well as the web browsers, to protect against known phishing techniques.
- Verification Methods:
In the event of any unsolicited communication from trusted sources, the verification of these should be sought after through different means of contact, for instance.
Strategy | Description | Effectiveness |
User Awareness Training | Teaching consumers how to spot phishing scams and how to be protected. | High |
Multi-Factor Authentication (MFA) | An additional security measure that calls for more information than a login credentials. | Very High |
Email Filtering & Spam Detection | Blocks fraudulent websites and attachments as well as doubtful interactions. | High |
Software Updates | Updates security software in order to fight off emerging threats. | Moderate |
Verification Methods | Verifying doubtful communications using different methods. | High |
Conclusion:
This will continue to be a risk to individuals and businesses throughout the digital age. The majority of phishing is identifiable and preventable by creating a combination of awareness, technology, and vigilance. The strategies that could keep users safe in this regard might include user training, multi-factor authentication, and more advanced email filtering systems. Understanding the dynamics of phishing and applying effective preventive measures is the key to online safety and security in today’s cyber landscape.
References:
- Burita, Ladislav, Petr Matoulek, Kamil Halouzka, Pavel Kozak, and Department of Informatics and Cyber Operations, University of Defence, 65 Kounicova Street, 66210 Brno, Czech Republic. “Analysis of Phishing Emails.” AIMS Electronics and Electrical Engineering 5, no. 1 (2021): 93–116. https://doi.org/10.3934/electreng.2021006.
- Maroso, Leonardo. “10 Top Tips to Detect Phishing Scams.” SecurityHQ, September 1, 2020. https://www.securityhq.com/blog/top-tips-to-detect-phishing-scams/.
- Naqvi, Bilal, Kseniia Perova, Ali Farooq, Imran Makhdoom, Shola Oyedeji, and Jari Porras. “Mitigation Strategies against the Phishing Attacks: A Systematic Literature Review.” Computers & Security 132 (September 1, 2023): 103387. https://doi.org/10.1016/j.cose.2023.103387.
- Sahingoz, Ozgur Koray, Ebubekir Buber, Onder Demir, and Banu Diri. “Machine Learning Based Phishing Detection from URLs.” Expert Systems with Applications 117 (March 1, 2019): 345–57. https://doi.org/10.1016/j.eswa.2018.09.029.
- Sonowal, Gunikhan. “Introduction to Phishing.” In Phishing and Communication Channels: A Guide to Identifying and Mitigating Phishing Attacks, edited by Gunikhan Sonowal, 1–24. Berkeley, CA: Apress, 2022. https://doi.org/10.1007/978-1-4842-7744-7_1.
- Jain, A. K., & Gupta, B. B. (2018). PHISH-SAFE: URL features-based phishing detection system using machine learning. In Cyber Security: Proceedings of CSI 2015 (pp. 467-474). Springer Singapore.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- Rahaman M. (2025) Understanding Smishing: An Introduction to Mobile Phishing Threats in the Digital Age, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Understanding Phishing: Strategies to Detect and Prevent Online Scams, Insights2Techinfo, pp.1