By: Rishitha Chokkappagari, Department of Computer Science &Engineering, Madanapalle Institute of Technology & Science, Angallu (517325), Andhra Pradesh. chokkappagaririshitha@gmail.com
Abstract
Cyber phishing scams continue to plague people due to their modern and diverse nature in the current world. In this context, it is essential to underline that traditional forms of security can barely respond to the new forms of threats that appear in the information space. Machine learning using AI natural language processing, and regularity learning form the basis of the Current approach to improve the capability of the phishing detection system. This article focuses on the use of AI in the detection of phishing, since through AI systems, large datasets can be processed, and relevant patterns and behaviours that characterize the activity to detected in real-time. It is evident that through the integration of Artificial Intelligence in organizational setups, there will be minimal phishing attack occurrences, faster response to such incidences, and a strengthened cyber defence. Besides, including AI in anti-phishing also helps to minimize the threats that phishing attacks pose and further establish an efficient yet continually evolving solution to new threats.
AI solution employs artificial intelligence tools, which can identify hidden patterns in large volumes of data that outline phishing incidents. A number of these systems can automatically adapt to the new data and enhance the capacity to identify between good and bad signals. NLP techniques prove most useful in this regard, assisting in the recognition of acquired emails, URLs, and any other message containing the usual phrasing and syntax of phishing components such as special texts and patterns, wrong sender details, and any context anomaly among numerous others.
Finally, this research tries to look at the direction that AI might be taking in the future especially in the field of phishing detection in consideration to other innovations like the use of blockchain and other enhanced encryption. Thus, utilizing all the possibilities of artificial intelligence, it is possible to develop stronger protection against phishing activity and ensure the confidentiality and uninterrupted nature of transmitting critical information.
Keywords: Artificial Intelligence, Phishing, Scam detection
Introduction
As the density of the connection of the people and organizations of the world continue to grow, the tendency of phishing attacks rises as well. This refers to the unlawful act of creating and sending messages in an organization which looks like genuine in an attempt of making receivers disclose their password and credit card numbers. These attacks target people’s psychological reactions and their trust, and they may appear as messages from familiar sources such as banks, social networks or popular shops.
AI as a technology is new, it has all the potential that cybersecurity needs in the future, especially in addressing the problem of phishing attacks. AI technologies are prominent that are using the technique such as ML algorithms ad NLP that presents extended features in tracing big data, pattern identification, and the capacity to learn from new datasets to enhance the detection capability. In this way, using machine learning approaches, it is possible to train models on huge amounts of phishing and genuine instances to detect such nuances that one may not easily notice. This helps to determine more new schemes of phishing that do not correlate to existing patterns. Specifically, NLP, an AI subfield that deals with the communication between computers and languages spoken by people, is employed in the process of analysis and interpretation of the content of the phishing messages. Linguistic tools can be used by the NLP to identify text characteristics that are highly common in phishing emails and that may include use of urgency terms, newly created domains or improper language usage that may not be applicable to the sender. This approach is beneficial if supplemented with other techniques to achieve three objectives: to maintain AI systems’ real-time threat detection and minimize the exposure window that malignant actors can capitalize on during phishing attacks.
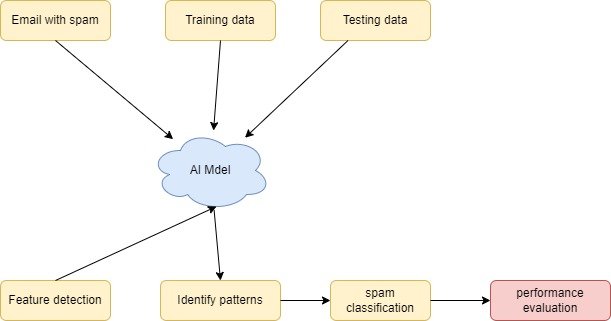
Figure 1 AI model for detecting spam
Phishing attacks and its challenge
In phishing attacks, the criminals employ psychological tactics and tricks, the method involves sending the target an e-mail, a text message, or an address like the real company, bank, or some other organization, and then the target is caught and offered to provide his or her account number, password, credit card information or other personal information. Cyber criminals have now added more refinement to their energy, and they are using spear phishing where the messages used are usually tailored to match the identity of the receiver, and clone phishing where the website is constructed to look exactly like the originality and techniques that defeat multi-factor authentication. Historical security solutions like filters or reviewing coming items separately can be rule-based and work with patterns or signatures. These methods can be quite easily bypassed by new tactics of phishing which, in turn, makes their employment necessary to evolve and become better[1].
New possibilities of utilizing AI technologies, through machine learning (ML) and natural language processing (NLP), present a new approach to managing the problem of phishing. AI is better because it can process large data and learn from it and is always able to develop new strategies against threats[2].
Here’s how AI enhances phishing detection:
- Machine Learning Algorithms: Machine learning can be trained from large databases that comprise both phishing and legitimate messages. These models are trained to learn and look for characteristics that might point to a phishing attempt, such as linguistic peculiarities, meta-tags, or other abnormalities of the domain. Since new data can be integrated into the machine learning models, it is possible to update or enhance the capability to detect new and existing methods of the phishers.
- Naive Bayes, K-Means, and SVM serve unique purposes in defeating Phishing E-mails; they take different characteristics of machine learning. This paper deems Naive Bayes particularly suitable as a classifier because it is simple and fast for text classification tasks. K-Means clustering is useful for outlier detection and feature extraction, while SVM’s main feature is its powerful ability to classify many records in cases of large numbers of input variables. Thus, applying these algorithms, one or combined, in a cybersecurity system, boosts the defense mechanisms against the phishing threat to bolster general security.
- Natural Language Processing (NLP): NLP allows AI systems to comprehend the content in emails or messages and even web pages that may be received or typed. This entails flagging words that are usually used in a Suspicious language pattern, an unusual request, and context which is usually applicable in phishing. NLP can also be incorporated into the messages to determine the sender’s intention hence increasing the efficiency of the detection[3].
- Real-Time Analysis and Response: Compared to traditional MDA, AI is capable of real-time data processing and returning immediate alarms and responses when there are potential phishing threats. It minimizes the time window that a phishing attack can inflict damage and pushes forward an earlier counteraction like the restriction of access, notification of the users, or setting up other lines of defense[4].
- Anomaly Detection: The elementary applications of the AI are to identify at least something that is out of the ordinary log-in time and IP addresses or any demanded data access. These disturbances can be recognized as the signs of phishing that follow and should be checked and countered.
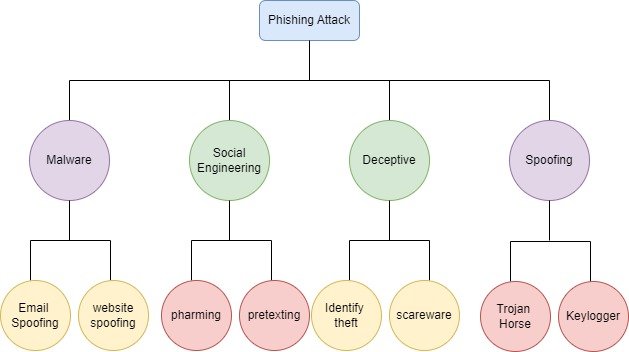
Figure 2 Phishing and it’s forms
Challenges and Considerations
While AI offers significant advantages in phishing detection, its implementation is not without challenges. Subsequently, the key drawback of AI for the detection of phishing is as follows:
- Data Quality and Quantity: Effective learning is hereby achieved through training with large datasets of high quality. Obtaining the right information to feed into the detection mechanism as well as a diverse sample of the phishing attack is very crucial[5].
- False Positives and Negatives: As mentioned before the functionality of an AI system sometimes classifies legitimate communications as phishing messages that they are not, this is called false positive and vice versa: no AI is perfect and it can sometimes fail to detect a real phishing attempt and classify it as such, these comprise false negatives. Like any measure, these mistakes can be minimized by creating a positive correlation between the sensitivity and specificity levels[6].
- Privacy and Security: AI performs the same task in analysing communication while also highlighting the matters regarding data privacy and its misuse. Stating that it is necessary to make the corresponding changes, the question arises: How can the data of OSCE users be protected? How can it be guaranteed that the AI systems ‘operate’ only the privacy act?[7]
Conclusion:
Despite the risks of phishing campaigns subsiding in recent years, they still present a major threat to cybersecurity due to human ignorance and tricks. The effectiveness of conventional anti-phishing measures is now more and more limited against the cornucopia of phishing techniques. The application of AI for defining phishing threats is a significant achievement in combating all the subfields of these cyber threats. Current AI technologies such as machine learning and natural language processing offer major opportunities in the fight against phishing attempts. Compared to conventional methods, AI can use large amounts of data and integrate new experiences to detect signs of phishing invisible to people. These systems are effective in providing real-time threat detection and as such, the response to the threats is likely to be more efficient.
However, there is a hitch when it comes to applying AI to phishing detection. To consider is the training of the model with quality data, the problems of false positives and negatives, and the privacy of data. Also, the adjustment of AI models to new tactics used in phishing needs to be ongoing, and there has to be research done on it. Therefore, it is reasonable to claim that the application of AI provides an additional tool for phishing protection as a component of complex security systems and continuous response to new threats. Implementing and utilizing AI solutions is the key to strengthening the organizations’ security, preserving their reputation, and becoming safeguarded against security threats in the contemporary highly digital environment.
References:
- L. Burita, P. Matoulek, K. Halouzka, P. Kozak, and Department of Informatics and Cyber Operations, University of Defence, 65 Kounicova Street, 66210 Brno, Czech Republic, “Analysis of phishing emails,” AIMS Electron. Electr. Eng., vol. 5, no. 1, pp. 93–116, 2021, doi: 10.3934/electreng.2021006.
- N. Kumar, S. Sonowal, and Nishant, “Email Spam Detection Using Machine Learning Algorithms,” in 2020 Second International Conference on Inventive Research in Computing Applications (ICIRCA), Jul. 2020, pp. 108–113. doi: 10.1109/ICIRCA48905.2020.9183098.
- F. Hossain, M. N. Uddin, and R. K. Halder, “Analysis of Optimized Machine Learning and Deep Learning Techniques for Spam Detection,” in 2021 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Apr. 2021, pp. 1–7. doi: 10.1109/IEMTRONICS52119.2021.9422508.
- P. Kalaharsha and B. M. Mehtre, “Detecting Phishing Sites — An Overview,” Apr. 06, 2021, arXiv: arXiv:2103.12739. doi: 10.48550/arXiv.2103.12739.
- P. Pappachan, Sreerakuvandana, and M. Rahaman, “Conceptualising the Role of Intellectual Property and Ethical Behaviour in Artificial Intelligence,” in Handbook of Research on AI and ML for Intelligent Machines and Systems, IGI Global, 2024, pp. 1–26. doi: 10.4018/978-1-6684-9999-3.ch001.
- L. Triyono, R. Gernowo, P. Prayitno, M. Rahaman, and T. R. Yudantoro, “Fake News Detection in Indonesian Popular News Portal Using Machine Learning For Visual Impairment,” JOIV Int. J. Inform. Vis., vol. 7, no. 3, pp. 726–732, Sep. 2023, doi: 10.30630/joiv.7.3.1243.
- S. Garera, N. Provos, M. Chew, and A. D. Rubin, “A framework for detection and measurement of phishing attacks,” in Proceedings of the 2007 ACM workshop on Recurring malcode, in WORM ’07. New York, NY, USA: Association for Computing Machinery, Nov. 2007, pp. 1–8. doi: 10.1145/1314389.1314391.
- Chui, K. T., Gupta, B. B., Chi, H. R., Arya, V., Alhalabi, W., Ruiz, M. T., & Shen, C. W. (2022). Transfer learning-based multi-scale denoising convolutional neural network for prostate cancer detection. Cancers, 14(15), 3687.
- Sharma, A., Singh, S. K., Kumar, S., Preet, M., Gupta, B. B., Arya, V., & Chui, K. T. (2024, January). Revolutionizing Healthcare Systems: Synergistic Multimodal Ensemble Learning & Knowledge Transfer for Lung Cancer Delineation & Taxonomy. In 2024 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-6). IEEE.
Cite As
Spoorthi K.S. (2024) Generative AI in Personalized Medicine, Insights2Techinfo, pp.1