By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
The cyber-attack tool known as Botnets allows criminals to conduct massive Distributed Denial-of-Service (DDoS) attacks. The attacks create extensive network disruptions while breaking essential services and result in substantial financial damage to organizations and state institutions. The paper evaluates how botnets function and their connection to DDoS attacks together with their protection methods. We establish a systematic analysis between various botnet systems alongside their attack modes and established security precautions. The paper includes a visual flowchart to explain how botnets generate DDoS attacks which helps readers understand the procedure better.
1.Introduction:
Internet dependency growth exposes organizations to multiple cyber-attacks because of their increased vulnerability. The DDoS attack remains the most detrimental type of persistent threat among cyber-attacks. The operational framework of extensive DDoS attacks functions through botnets which represent controlled remote-device networks[1]. This short article explains botnet operational methods and their cybersecurity impact alongside methods for botnet prevention measures.
2.Botnets and Their Role in DDoS Attacks:
Controlled by either C2 servers or decentralized mechanisms these computer networks made up of infected devices called bots carry out their operations. Through targeted traffic flooding attacks DDoS networks disable their victim systems thus making them unusable[2].
2.1 Components of a Botnet[3]:
- Botmaster: The attacker who controls the botnet operates under the role of Botmaster.
- Command and Control (C2): Through the Command and Control (C2) Server bots can communicate with each other.
- Infected Devices: The compromised systems which execute attack commands serve as infected devices.
- Attack Targets: The targets that suffered from DDoS attack operations functioned as victims[3].
2.2 Types of DDoS Attacks Executed by Botnets:
- Volume-Based Attacks: Flodding targets with enormous traffic (ingredients of UDP floods and ICMP floods) comprises Volume-Based Attacks[4].
- Protocol Attacks: Take advantage of weaknesses in network protocols (e.g., SYN flood, Ping of Death)[5].
- Application-Layer Attacks: Programs on the application layer experience targeted attacks when bots use HTTP flood or Slowloris attack methods[6].
3.Analysis of Botnet-Driven DDoS Attacks:
Several factors affect the capability of a botnet to conduct a DDoS attack, such as its size, communication model, and evasion technique. A comparison is illustrated below:
Botnet Type | Communication Model | Attack Impact | Detection Difficulty |
Centralized | C2 Server-Based | High | Moderate |
Peer-to-Peer (P2P) | Decentralized | Very High | High |
Hybrid | Mixed Approach | Extreme | Very High |
4.Flowchart: The DDoS attack by a Botnet:
A detailed flowchart showing how botnets initiate DDoS assaults can be seen below:
Fig(1)
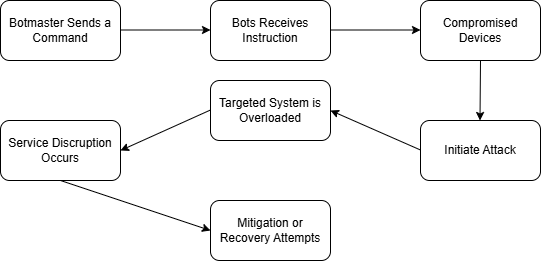
5.Mitigation Strategies:
Multiple methods exist to monitor and stop botnet assaults that launch DDoS attacks. The most productive methods to fight botnet-driven DDoS attacks consist of these:
- Traffic Analysis & Filtering: Security measures focused on traffic analysis help identify unusual traffic patterns in a network.
- Rate Limiting: Rate Limiting functions as a system to restrict the requests that come from individual sources.
- DDoS Protection Services: Utilizing cloud-based programs such as AWS Shield and Cloudflare.
- Behavioral Anomaly Detection: Behavioral Anomaly Detection uses AI to monitor systems in order to find irregular situations.
- Blacklisting Malicious IPs: The prevention of network access for known bots occurs through the practice of blacklisting malicious IP addresses.
6.Conclusion:
Mass DDoS attacks depend heavily on botnets to realize their malicious effects making them a primary cybersecurity threat. Defenders need to employ improved detection and mitigation methods as attackers continue to develop their attack methods. Future research needs to devise AI solutions that detect and prevent botnets from initiating their attack sequence.
References:
- A. A. Al-Kadhimi, M. M. Singh, and M. N. A. Khalid, “A Systematic Literature Review and a Conceptual Framework Proposition for Advanced Persistent Threats (APT) Detection for Mobile Devices Using Artificial Intelligence Techniques,” Appl. Sci., vol. 13, no. 14, Art. no. 14, Jan. 2023, doi: 10.3390/app13148056.
- M. Gelgi, Y. Guan, S. Arunachala, M. Samba Siva Rao, and N. Dragoni, “Systematic Literature Review of IoT Botnet DDOS Attacks and Evaluation of Detection Techniques,” Sensors, vol. 24, no. 11, Art. no. 11, Jan. 2024, doi: 10.3390/s24113571.
- S. Padhiar and R. Patel, “Behaviour based botnet detection with traffic analysis and flow intervals at the host level,” Indones. J. Electr. Eng. Comput. Sci., vol. 31, no. 1, p. 350, Jul. 2023, doi: 10.11591/ijeecs.v31.i1.pp350-358.
- S. Javanmardi, M. Ghahramani, M. Shojafar, M. Alazab, and A. M. Caruso, “M-RL: A mobility and impersonation-aware IDS for DDoS UDP flooding attacks in IoT-Fog networks,” Comput. Secur., vol. 140, p. 103778, May 2024, doi: 10.1016/j.cose.2024.103778.
- R. Uddin, S. A. P. Kumar, and V. Chamola, “Denial of service attacks in edge computing layers: Taxonomy, vulnerabilities, threats and solutions,” Ad Hoc Netw., vol. 152, p. 103322, Jan. 2024, doi: 10.1016/j.adhoc.2023.103322.
- S. Black and Y. Kim, “An Overview on Detection and Prevention of Application Layer DDoS Attacks,” in 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Jan. 2022, pp. 0791–0800. doi: 10.1109/CCWC54503.2022.9720741.
- Lu, J., Shen, J., Vijayakumar, P., & Gupta, B. B. (2021). Blockchain-based secure data storage protocol for sensors in the industrial internet of things. IEEE Transactions on Industrial Informatics, 18(8), 5422-5431.
- Singh, A., & Gupta, B. B. (2022). Distributed denial-of-service (DDoS) attacks and defense mechanisms in various web-enabled computing platforms: issues, challenges, and future research directions. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-43.
- Gaurav A. (2023) Cybersecurity in the Smart Grid: Detecting and Mitigating DDoS Attacks, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Botnets Fuel Large-Scale DDoS Attacks: An In-Depth Analysis, Insights2Techinfo, pp.1