By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
With the Internet of Things (IoT) growing at a very fast rate, millions of smart devices integrated into the Internet have become an integral part of daily life. However, such devices are generally not adequately secured and open to cyber-attacks. Distributed Denial-of-Service (DDoS) attacks exploit such weaknesses and employ compromised IoT devices to target networks and compromise services. This essay describes how IoT devices are the cybersecurity Achilles’ heel, how IoT-caused DDoS attacks are carried out, and how they can be contained. Flowchart and a comparison table explains in-detail of these concepts in greater depth.
1.Introduction:
Internet of Thing (IoT) has revolutionized industries, households, and infrastructures in its trail. With the explosive increase in devices getting connected is the new issue of security. The most chilling of these threats is certainly the hacking of IoT devices to use them in DDoS attacks that can crash networks and negatively impact service[1]. Because Internet of Things devices lack safety precautions compared to traditional computer equipment, attackers can easily compromise them[2].
2.How IoT Devices Contribute to DDoS Attacks:
2.1 Inherent Security Weaknesses:
Majority of IoT devices lack or have minimal security within them, without firmware updates, secure authentication, or encryption methods. These exposures allow hackers to hijack devices and use them in huge botnets to launch DDoS attacks[3].
2.2 Botnets and DDoS Attacks:
Hackers employ hijacked Internet of Thing (IoT) devices to form botnets-networks of hijacked devices-that perform Distributed Denial-of-Service (DDoS) attacks by flooding targeted systems with enormous traffic[4].Some of the most prominent examples include the Mirai botnet, which used 1.5millions of IoT devices globally [5].
2.3 Exploiting IoT Communication Protocol:
IoT devices offer light protocols such as MQTT and CoAP, which in most cases lack security support. Attackers exploit the protocols to hijack communication and launch attacks to rapidly [6].
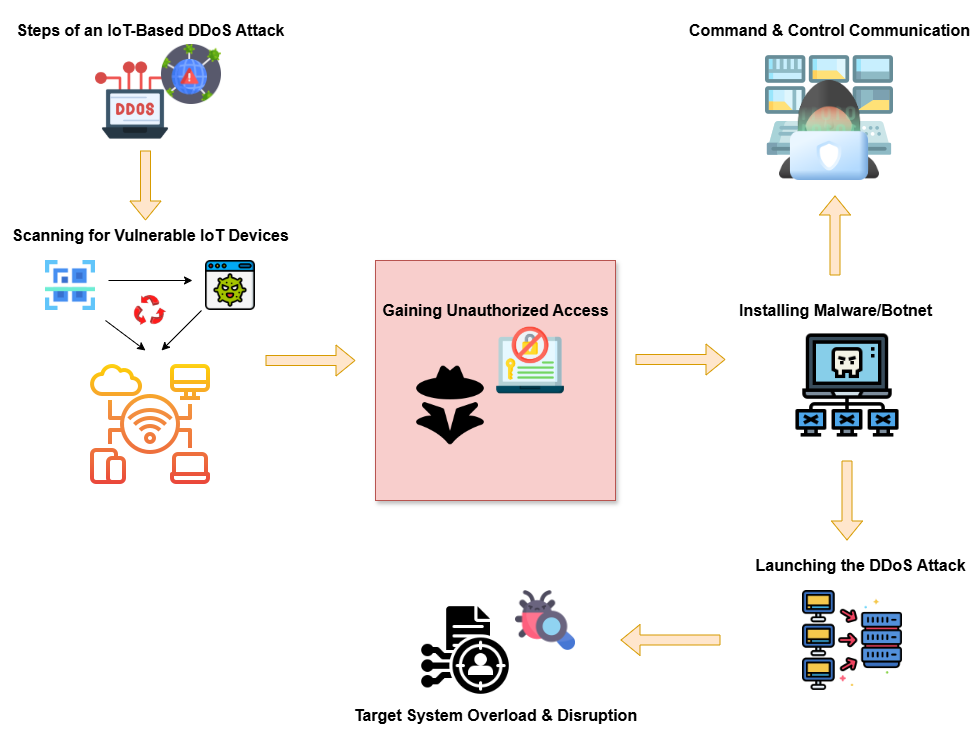
3. Flowchart of IoT-Based DDoS Attacks
Flowchart: Steps of an IoT-Based DDoS Attack
4. Comparison of IoT vs. Traditional Devices in DDoS Attacks:
Feature | IoT Devices | Traditional Computing Devices |
Security Updates | Infrequent or None | Regular Updates |
Preprocessing Power | Low | High |
Default Passwords | Weak & Often Unchanged | Typically Customized |
Attack surface | Large (Millions of Devices) | Smaller (Fewer Endpoints) |
Defense Mechanisms | Minimal | Advanced Firewalls & Antivirus |
5. Mitigation Strategies:
5.1 IoT Security Enhancement:
Firms should implement enhanced security features like secure boot functionality, automatic firmware updates, and encrypted data transfer. Secure development practices should also be required to be followed from the design phase to prevent vulnerabilities in the first place[7].
5.2 Network-Level Countermeasures:
Organizations should install traffic filtering, anomaly detection, and DDoS protection solutions to prevent IoT-based attacks from overwhelming networks. Intrusion Detection and Prevention Systems (IDPS) installation can help in the early blocking and detection of attack traffic[8].
5.3 User Awareness and Best Practices:
Default passwords have to be changed by users, devices have to be updated, and IoT devices have to be isolated from mission-critical environments to reduce hazards. Educating consumers regarding danger in IoT devices and promoting uptake of security mechanisms such as VPNs and firewalls will equally go a great distance in mitigating threats.
5.4 Regulatory and Compliance Measures:
IoT manufacturers should be made to follow strict cybersecurity regulations by governments and regulatory bodies. IoT devices should be mandated to comply with compliance standards such as GDPR, NIST, and ISO 27001 to ensure security compliance. IoT security certifications will be mandated to encourage manufacturers to adopt security best practices.
5.5 AI and Machine Learning-Based Threat Detection:
The use of AI-driven security mechanisms can significantly enhance real-time DDoS attack detection. Machine learning software can analyze patterns of traffic, detect anomalies, and trigger automatic mitigation responses before attacks have formed[9].
5.6 Blockchain for IoT Security:
Blockchain can be utilized to enhance IoT security by means of decentralized authentication procedures, maintaining data integrity and reducing device tampering risk. Blockchain identity management systems on a blockchain basis can exclude unauthorized parties from IoT networks[10].
6. Conclusion:
The greater the growth of IoT adoption, the greater the threat of IoT-based DDoS attacks will be. The vulnerability of smart devices to security breaches makes them compromise as the perfect targets for hackers. A combination of strong device security, network protection, and user awareness is critical in thwarting these vulnerabilities. Without precautions, IoT devices will remain the weakest link in the cybersecurity chain.
References:
- P. Kumari and A. K. Jain, “A comprehensive study of DDoS attacks over IoT network and their countermeasures,” Comput. Secur., vol. 127, p. 103096, Apr. 2023, doi: 10.1016/j.cose.2023.103096.
- Dr. Y. Perwej, S. Qamar Abbas, J. Pratap Dixit, Dr. N. Akhtar, and A. Kumar Jaiswal, “A Systematic Literature Review on the Cyber Security,” Int. J. Sci. Res. Manag., vol. 9, no. 12, pp. 669–710, Dec. 2021, doi: 10.18535/ijsrm/v9i12.ec04.
- S. El Jaouhari and E. Bouvet, “Secure firmware Over-The-Air updates for IoT: Survey, challenges, and discussions,” Internet Things, vol. 18, p. 100508, May 2022, doi: 10.1016/j.iot.2022.100508.
- M. A. AlHija, H. J. Alqudah, and H. Dar-Othman, “Uncovering botnets in IoT sensor networks: a hybrid self-organizing maps approach,” Indones. J. Electr. Eng. Comput. Sci., vol. 34, no. 3, p. 1840, Jun. 2024, doi: 10.11591/ijeecs.v34.i3.pp1840-1857.
- H. Jin, G. Jeon, H. W. A. Choi, S. Jeon, and J. T. Seo, “A threat modeling framework for IoT-Based botnet attacks,” Heliyon, vol. 10, no. 20, Oct. 2024, doi: 10.1016/j.heliyon.2024.e39192.
- S. Lakshminarayana, A. Praseed, and P. S. Thilagam, “Securing the IoT Application Layer From an MQTT Protocol Perspective: Challenges and Research Prospects,” IEEE Commun. Surv. Tutor., vol. 26, no. 4, pp. 2510–2546, 2024, doi: 10.1109/COMST.2024.3372630.
- S. Brightwood, “The Importance of Secure Firmware Updates in Maintaining System Integrity”.
- A. Pakmehr, A. Aßmuth, N. Taheri, and A. Ghaffari, “DDoS attack detection techniques in IoT networks: a survey,” Clust. Comput., vol. 27, no. 10, pp. 14637–14668, Dec. 2024, doi: 10.1007/s10586-024-04662-6.
- S. Kumar, M. Dwivedi, M. Kumar, and S. S. Gill, “A comprehensive review of vulnerabilities and AI-enabled defense against DDoS attacks for securing cloud services,” Comput. Sci. Rev., vol. 53, p. 100661, Aug. 2024, doi: 10.1016/j.cosrev.2024.100661.
- M. Rahaman, C. Y. Lin, I. Rachmat, R. Bansal, and Prayitno, “Secure Health Features: Implementing Hyperledger Fabric in Blockchain-Driven Healthcare Management Systems,” in Digital Forensics and Cyber Crime Investigation, CRC Press, 2024.
- Gupta, B. B., Gaurav, A., Panigrahi, P. K., & Arya, V. (2023). Analysis of artificial intelligence-based technologies and approaches on sustainable entrepreneurship. Technological Forecasting and Social Change, 186, 122152.
- Zou, L., Sun, J., Gao, M., Wan, W., & Gupta, B. B. (2019). A novel coverless information hiding method based on the average pixel value of the sub-images. Multimedia tools and applications, 78, 7965-7980.
- Dhananjay Singh (2021) Captcha Improvement: Security from DDoS Attack, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) DDoS in the Age of IoT: Why Smart Devices Are the Weakest Link, Insights2Techinfo, pp.1