By: Vivek Singh Baghel and Surya Prakash
Fingerprint biometrics is one of the extensively used biometric traits in order to provide secure authentication. It has numerous advantages [1] over the other biometric traits such as being easy to capture and process; and being highly distinctive in establishing the individual’s identification due to which fingerprint biometrics has been widely in use. The fingerprint impression of an individual is comprised of a continuous pattern of valleys and ridges. These patterns exhibit distinctive features for the identification of a person. Fingerprint-based biometric systems are mainly categorized as texture-based and minutiae-based systems. In the systems based on texture, the extracted features from a fingerprint image represent the pattern of ridge and valley such as LBP [2], LDP [3], and FingerCode [4]. Whereas in the latter category, ridge end and ridge bifurcation that is also called minutiae points are used as unique features to identify an individual. In addition, core and delta points, also called singular points, are used along with the minutiae to identify a person. Figure 1 depicts an image of a fingerprint impression, along with the minutiae and singular points marked on it. Furthermore, as compared to texture-based systems, minutiae-based systems have a higher level of reliability, which has been widely explored in the literature.

The research in fingerprint biometrics revolves around developing highly accurate fingerprint authentication systems, fingerprint template protection techniques, and the application of secure fingerprint authentication for various fields such as IoT, Networking, Cloud computing, etc. Various fingerprint databases have been utilized to evaluate the proposed methodologies that are discussed in the literature. The fingerprint databases from the international Fingerprint Verification Competition (FVC) [1, 6, 7] are the most popular and widely used databases by the researchers to evaluate their findings. Moreover, there are a few large-sized fingerprint databases such as the IIT Kanpur fingerprint database [8] and CASIA fingerprint databases [9], which have also been utilized. Here, we provide a description of some of the popular fingerprint databases that have been used to carry out all kinds of research related to fingerprint biometrics. We have discussed a total of sixteen fingerprint databases from the international Fingerprint Verification Competition FVC2000, FVC2002, FVC2004, and FVC2006, along with two large-sized fingerprint databases, viz., IIT Kanpur and CASIA fingerprint databases. A detailed description of these databases is as follows.
FVC2000 (DB1, DB2, DB3, DB4) [1, 10]: These databases are from the first international Fingerprint Verification Competition, which includes four databases collected using different sensors. These databases are publicly available and can be accessed through [1]. In these databases, DB1, DB2, and DB3 have been collected using optical and capacitive fingerprint sensors. Whereas, DB4 is a synthetic database, and has been generated using a synthetic generator [11]. There are two sets in each database, i.e., set A and set B, where set A is used to evaluate the proposed methodology, whereas set B is used to tune the parameters. The complete information about these databases is tabulated in Table 1:

FVC2002 (DB1, DB2, DB3, DB4) [1, 12]: These fingerprint databases are from the second international Fingerprint Verification Competition, which includes four databases. FVC2002 databases are publicly available and can be accessed through [1]. Three of these databases, namely, DB1, DB2, and DB3 have been acquired by utilizing optical and capacitive sensors. In contrast, the fourth database, i.e., DB4 is a synthetic fingerprint database and is obtained using SFinGe v2.51 software [11]. There are two sets in each database, i.e., set A and set B, where set A is used to evaluate the proposed methodology, whereas set B is used to tune the parameters. The complete information about these databases is in Table 2:

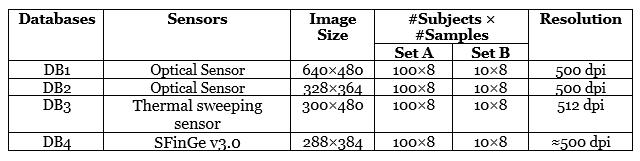
FVC2004 (DB1, DB2, DB3, DB4) [6]: These fingerprint databases are from the third international Fingerprint Verification Competition, which includes four databases. Fingerprint databases from FVC2004 are publicly available and can be accessed through the official webpage of FVC2004 [6]. Among these four databases, DB1 and DB2 have been collected by using an optical sensor, DB3 has been collected using a thermal sweeping sensor whereas DB4 is a synthetic dataset that has been obtained using SFinGe v3.0 [11]. In these databases, the fingerprint images have been collected without putting any effort to get good quality fingerprint images. The volunteers were asked to keep their fingerprint on the sensor by rotating the finger, exaggerating the skin distortion, high/low pressure on the sensor, changing finger’s position vertically on the sensor, dried, and moistened fingers to collect the fingerprint images. This makes the FVC2004 databases more challenging and it provides a very realistic set of images for developing an effective fingerprint recognition techniques as compared to the databases which were provided in the previous competitions such as FVC2000 and FVC2002. There are two sets in each database, i.e., set A and set B, where set A is used to evaluate the proposed methodology, whereas set B is used to tune the parameters. The complete information about these databases is tabulated in Table 3.
FVC2006 (DB1, DB2, DB3, DB4) [7]: These fingerprint databases are from the fourth international Fingerprint Verification Competition, which includes four databases. FVC2006 databases are publicly available and can be accessed through [7, 13]. In these databases, DB1 has been collected using an electric field sensor, DB2 has been collected using an optical sensor, DB3 has been collected using a thermal sweeping sensor, and DB4 is a collection of synthetic fingerprint images, which has been obtained using SFinGe v3.0 [11]. The fingerprint images have not been collected by imposing intentionally distorted skin, rotation, and translation of fingerprint images, unlike the previous FVC databases. However, the FVC2006 database consists of a more heterogeneous population and contains the fingerprint samples collected from older people and manual workers. In addition, the samples that have been collected from the lowest quality index finger were considered for the selection of the final dataset in order to make the database sufficiently challenging in terms of technological evaluation. Like previous competitions, there are two sets in each database, i.e., set A and set B, where set A is used to evaluate the proposed methodology, whereas set B is used to tune the parameters in the FVC2006 database. The complete information about these databases is tabulated in Table 4.

IIT Kanpur (IITK) fingerprint database: IITK fingerprint database is a large database compared to the databases provided in various fingerprint verification competitions. The database has been collected from 1378 subjects and for each subject, four fingerprint samples are there in the database. This makes it a large fingerprint database containing 5512 fingerprint images. The IITK fingerprint database has also been used in the literature [8]; however, it has not been made publicly available by the concerned organization.
CASIA fingerprint database: This fingerprint biometric database is one of the large fingerprint databases, and is popularly called CASIA fingerprint image database v5.0 [9]. The database has been collected from 500 subjects and contains a total of 20,000 images. For each subject, 40 fingerprint images are there in the database, which includes 5 samples of 8 different fingers (both thumb, second, third, and fourth fingers) of a subject. The volunteers who contributed to this database are workers, graduate students, waiters, etc. The CASIA fingerprint image database v5.0 is a publicly available fingerprint database and can be accessed through the official website of CASIA [9].
References
- Maltoni, D.; Maio, D.; Jain, A. K.; Prabhakar, S., Multimodal Biometric Systems. Handb. Fingerpr. Recognit., 2003, 233–255.
- Ahonen, T.; Hadid, A.; Pietikainen, M. Face Description with Local Binary Patterns: Application to Face Recognition. IEEE Trans. Pattern Anal. Mach. Intell., 2006, 28 (12), 2037–2041.
- Jabid, T.; Kabir, M. H.; Chae, O. Local Directional Pattern (LDP) – A Robust Image Descriptor for Object Recognition. In Proc. 7th IEEE International Conference on Advanced Video and Signal Based Surveillance; 2010; pp 482–487.
- Jain, A. K.; Prabhakar, S.; Hong, L.; Pankanti, S. Filterbank-Based Fingerprint Matching. IEEE Trans. Image Process., 2000, 9 (5), 846–859. https://doi.org/10.1109/83.841531.
- Baghel, V. S.; Ali, S. S.; Prakash, S. A Non-Invertible Transformation Based Technique to Protect a Fingerprint Template. IET Image Process., 1–15. https://doi.org/https://doi.org/10.1049/ipr2.12130.
- Fingerprint Verification Competition 2004 (accessed Dec 6, 2021).
- Cappelli, R.; Ferrara, M.; Franco, A.; Maltoni, D. Fingerprint Verification Competition 2006. Biometric Technol. Today, 2007, 15 (7), 7–9.
- Ali, S. S.; Iyappan, G. I.; Mahyo, S.; Prakash, S. Polynomial Vault: A Secure and Robust Fingerprint Based Authentication. IEEE Trans. Emerg. Top. Comput., 2019.
- CASIA Fingerprint databases (accessed Dec 6, 2021).
- Maio, D.; Maltoni, D.; Cappelli, R.; Wayman, J. L.; Jain, A. K. FVC2000: Fingerprint Verification Competition. IEEE Trans. Patt. Anal. Mach. Intell., 2002, 24 (3), 402–412.
- Fingerprint Generation – Biometric System Laboratory, DISI – University of Bologna (accessed Dec 6, 2021).
- Maio, D.; Maltoni, D.; Cappelli, R.; Wayman, J. L.; Jain, A. K. FVC2002: Second Fingerprint Verification Competition. In 2002 International Conference on Pattern Recognition; 2002; Vol. 3, pp 811–814 vol.3.
- Biometrics and Data Pattern Analytics – BiDA Lab
Cite this article as:
Vivek Singh Baghel and Surya Prakash (2021) Fingerprint Biometrics: Popular Databases for Research, Insights2Techinfo, pp.1
Also Read
- Biometric Fingerprint Authentication: Challenges and Future Research Directions
- Biometric Spoof Detection
- Biometric Template Security
Very Good Article
Thank you
great article
Thank you