By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Cyber threats based on phishing scams currently stand as one of the most widespread deception tools which trick users and organizations into handing over their sensitive information. Sophisticated phishing attacks circumvent security measures that were established traditionally. The decentralized quality and unalterable characteristics of blockchain technology provide an effective approach to reduce security risks. This research investigates blockchain applications to strengthen anti-phishing security through methods that stabilize data authenticity and spread authorization across the system and create a trust-centric environment. The paper examines different blockchain anti-phishing solutions composed of decentralized identity management and smart contracts and domain security components. Blockchain technology can minimize phishing attacks while improving digital security effectiveness when used with current cybersecurity systems according to the paper’s conclusions.
Introduction
The practice of phishing criminals replicates authentic operations to obtain user verification details and financial data. Technical progress in cybersecurity has not been able to fully resolve phishing attacks because attackers have become increasingly skilled at deceptive methods[1]. Blockchain technology brings secure tamper-resistant features which create a new method to prevent phishing attacks. Blockchain technology serves as a tool to fight phishing scams and enhances security measures through this study.
Understanding Blockchain Technology[2]
Blockchain serves as an autonomous and multi-node network system which maintains transaction records throughout its connected member systems. Key characteristics of blockchain include:
- Decentralization : Eliminates single points of failure.
- The system maintains data unchangeability so unauthorized modifications and tampering are prevented.
- Transparency: Enhances trust among users.
- The system protects data by using encryption technology which stands as cryptographic security.
Blockchain stands out as an optimal solution to boost cybersecurity protocols due to its properties which protect against phishing attacks.
Blockchain Solutions for Phishing Prevention
Decentralized Identity Management
Identity spoofing serves as the main tool attackers utilize for their phishing activities. The security of digital identities becomes possible through blockchain-based decentralized identity (DID) solutions because users remain in full control of their identity. Centralized authentication databases fail to protect identity information because DID systems employ blockchain technology to store this data thus minimizing identity theft risks[3].
Smart Contracts for Authentication
Self-executing contracts exist on blockchain networks because they contain predefined rules written within blockchain codes. The system automates authentication operations which guarantee valid entities receive access to private data. Centralized password-based authentication systems become less necessary because of this authentication method[4].
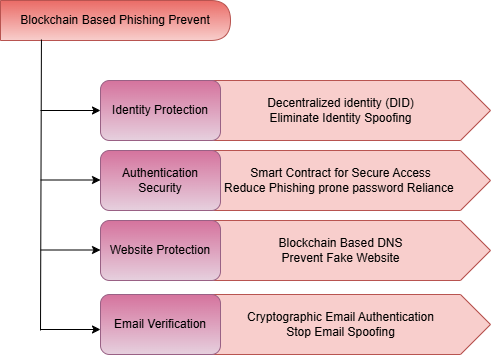
Secure Domain Name Systems (DNS)
Phishing scammers operate fake websites which use deception to replicate actual business websites. The decentralization of domain registration in blockchain DNS solutions enables better security because cybercriminals find it challenging to tamper with DNS records for creating fraudulent websites[3].
Email Verification with Blockchain
Phishing emails serve as one of the main channels through which cyberattacks occur. Digital communications by email gain authenticity through blockchain encryption signatures. The security system DMARC (Domain-based Message Authentication Reporting and Conformance) improves phishing attack prevention through blockchain integration for email spoofing defense[4].
Advantages and Challenges of Blockchain-Based Phishing Prevention
Advantages
- Blockchain improves data integrity since its ledger cannot be changed.
- Decreased reliance on central authorities since there are no single points of failure.
- Transparency: Because all transactions happen to be verifiable, it builds up trust.
- Automation: Smart Contracts- it automates the security procedures without the interference of any human intervention.
Challenges
- Scalability: Poor processing rates along with high transaction costs have restricted the scalability of the system.
- Companies need to invest millions in the accommodation of blockchain technology into their existing business processes.
- Business firms have legal and compliance issues with the usage of blockchain-based security systems, leading to regulatory hurdles.
Conclusion
Blockchain establishes a strong anti-phishing defense system which uses decentralized identity systems along with smart contracts and safe Domain Name System services and email verification protocols. The security benefits of blockchain together with its trust-enhancing features establish it as a workable response to fight against phishing threats although adoption and scalability present current obstacles. Collaborating blockchain solutions with current cybersecurity standards enables businesses to reduce their phishing exposure while advancing complete digital security covers. Research needs to investigate methods that enhance blockchain efficiency along with its cost-effectiveness as these factors will drive universal blockchain adoption. A secure digital environment requires government and cybersecurity firm and blockchain developer collaboration to develop its framework.
References
- A. Basit, M. Zafar, X. Liu, A. R. Javed, Z. Jalil, and K. Kifayat, “A comprehensive survey of AI-enabled phishing attacks detection techniques,” Telecommun. Syst., vol. 76, no. 1, pp. 139–154, Jan. 2021, doi: 10.1007/s11235-020-00733-2.
- J. J. Pieters, A. Kokkinou, and T. van Kollenburg, “Understanding Blockchain Technology Adoption by Non-experts: an Application of the Unified Theory of Acceptance and Use of Technology (UTAUT),” Oper. Res. Forum, vol. 3, no. 1, p. 1, Dec. 2021, doi: 10.1007/s43069-021-00113-9.
- J. N. Al-Karaki, A. Gawanmeh, and C. Fachkha, “Blockchain for Email Security: A Perspective on Existing and Potential Solutions for Phishing Attacks,” in 2023 Fifth International Conference on Blockchain Computing and Applications (BCCA), Oct. 2023, pp. 404–411. doi: 10.1109/BCCA58897.2023.10338865.
- D. R. Sahu, H. Tiwari, D. S. Tomar, and R. K. Pateriya, “Quantum-Resistant Cryptography to Prevent from Phishing Attack Exploiting Blockchain Wallet,” in Sustainable Security Practices Using Blockchain, Quantum and Post-Quantum Technologies for Real Time Applications, A. Kumar, N. J. Ahuja, K. Kaushik, D. S. Tomar, and S. B. Khan, Eds., Singapore: Springer Nature, 2024, pp. 171–191. doi: 10.1007/978-981-97-0088-2_9.
- Blockchain-based Supply Chain Solution Using IPFS and QR Technology for Traditional Weave in West Nusa Tenggara
- H Wijayanto, MJ Andara, D Wiraguna, N Agitha… – JURNAL INFOTEL, 2024
- Singh, A., & Gupta, B. B. (2022). Distributed denial-of-service (DDoS) attacks and defense mechanisms in various web-enabled computing platforms: issues, challenges, and future research directions. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-43.
- Gupta, B. B., Gaurav, A., Panigrahi, P. K., & Arya, V. (2023). Analysis of artificial intelligence-based technologies and approaches on sustainable entrepreneurship. Technological Forecasting and Social Change, 186, 122152.
- Sahoo, S. R., & Gupta, B. B. (2019). Hybrid approach for detection of malicious profiles in twitter. Computers & Electrical Engineering, 76, 65-81.
- REDDY K.T (2023) Unmasking Mobile Phishing Strategies, Tactics, and Defence, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) The Role of Blockchain in Preventing Phishing Scams, Insights2techinfo pp.1